
The Underground ransomware gang has claimed responsibility for an October 5 attack on Japanese tech giant Casio, which caused system disruptions and impacted some of the firm's services.
Earlier this week, Casio disclosed the attack on its website but withheld details about the incident, saying it had engaged external IT specialists to investigate whether personal data or other confidential information was stolen in the attack.
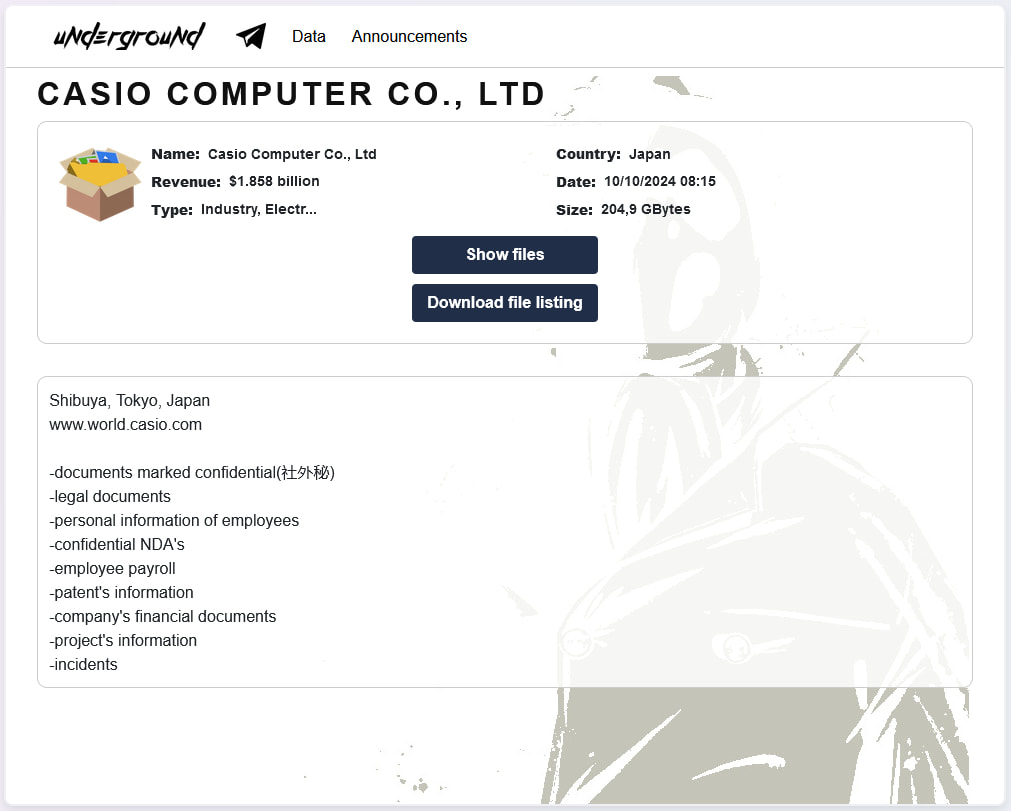
Today, the Underground ransomware group has added Casio on its dark web extortion portal, leaking troves of data allegedly stolen from the Japanese firm.
The leaked data includes:
- Confidential documents (社外秘)
- Legal documents
- Personal data of employees
- Confidential NDA's
- Employee payroll information
- Patents information
- Company financial documents
- Project information
- Incident reports
If the above is true, the attack has compromised Casio's workforce and intellectual property, which could negatively impact its business.
Source: BleepingComputer
BleepingComputer has contacted Casio again requesting a comment on the threat actors' claims and data leak, but we have not received a response by publication. Therefore, the threat actor's claims remain unverified.
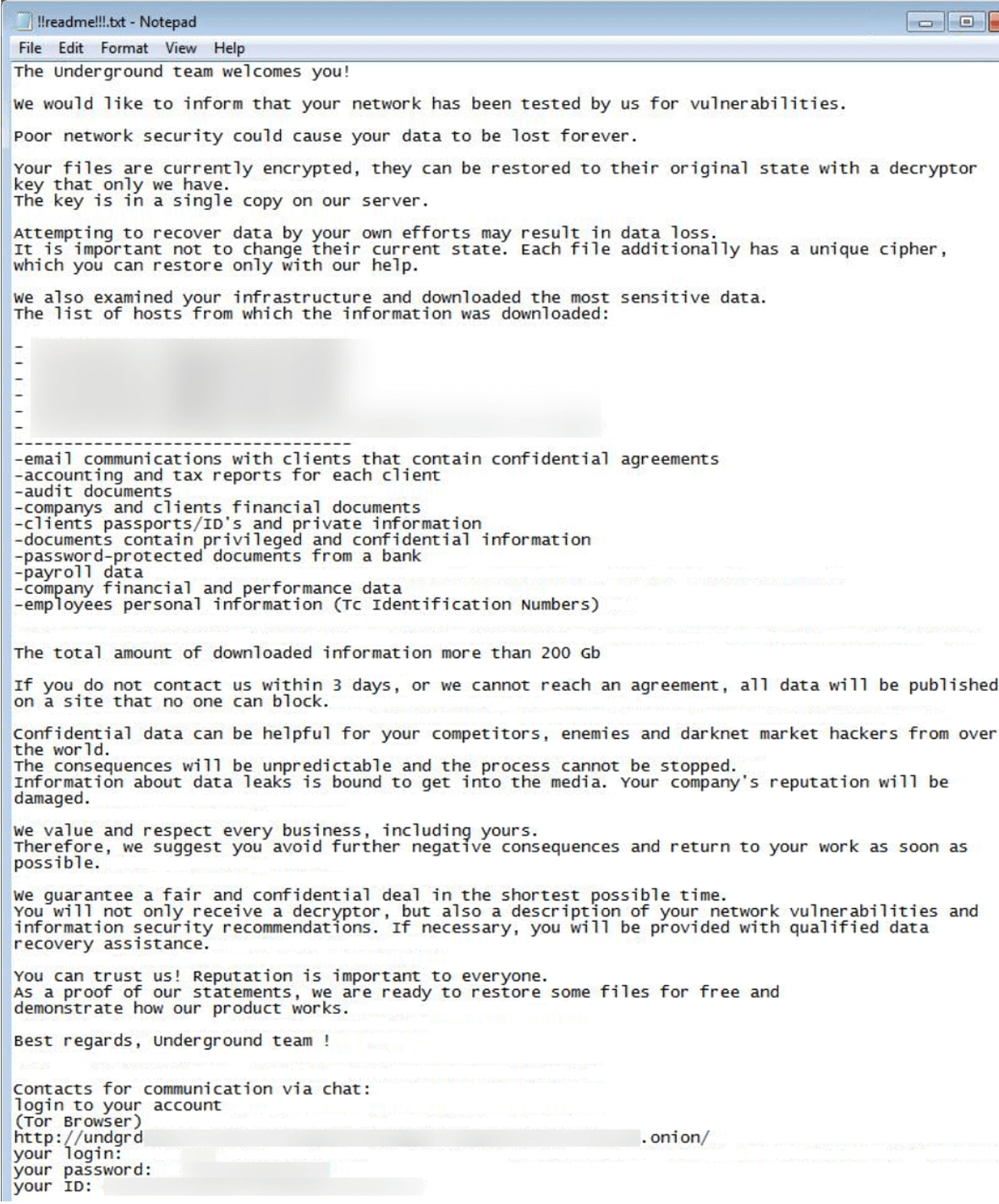
Underground ransomware overview
According to a Fortinet report from late August 2024, Underground is a relatively small-scale ransomware operation targeting Windows systems since July 2023.
The strain has been associated with the Russian cybercrime group 'RomCom' (Storm-0978), who previously delivered Cuba ransomware on breached systems.
Fortinet reports that during the summer, Underground ransomware operators engaged in exploiting CVE-2023-36884, a remote code execution flaw in Microsoft Office, likely used as an infection vector.
Once a system is breached, the attackers modify the registry to keep Remote Desktop sessions alive for 14 days after user disconnection, giving them a comfortable window to maintain access to the system.
Underground does not append any file extensions to encrypted files, and it's configured to skip file types essential for Windows operation to avoid rendering the system unusable.
Moreover, it stops the MS SQL Server service to free up data for theft and encryption, maximizing the attack's impact.
As is the case with most Windows ransomware, Underground deletes shadow copies to make easy data restoration impossible.
Source: Fortinet
An unusual trait in Underground's extortion tactics is that it also leaks the stolen data on Mega, promoting links to archives hosted there via its Telegram channel, maximizing the exposure and availability of the data.
Underground ransomware's extortion portal currently lists 17 victims, most of whom are based in the USA.
Whether or not the Casio attack will be the threat group's breakthrough into the mainstream, followed by a higher attack volume/pace, remains to be seen.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now