
Hackers are increasingly targeting Windows users with the malicious Winos4.0 framework, distributed via seemingly benign game-related apps.
The toolkit is the equivalent of Sliver and Cobalt Strike post-exploitation frameworks and it was documented by Trend Micro this summer in a report on attacks against Chinese users.
At the time, a threat actor tracked as Void Arachne/Silver Fox lured victims with offers of various software (VPNs, Google Chrome browser) modified for the Chinese market that bundled the malicious component.
A report today from cybersecurity company Fortinet indicates an evolution in the activity, with hackers now relying on games and game-related files in their continued targeting of Chinese users.

Source: Fortinet
When the seemingly legitimate installers are executed, they download a DLL file from “ad59t82g[.]com” to initiate a multi-step infection process.
In the first stage, a DLL file (you.dll) downloads additional files, sets up the execution environment, and establishes persistence by adding entries in the Windows Registry.
In the second stage, injected shellcode loads APIs, retrieves configuration data, and establishes a connection to the command-and-control (C2) server.
In the third phase, another DLL (上线模块.dll) retrieves extra encoded data from the C2 server, stores it in the registry at "HKEY_CURRENT_USER\\Console\\0" and updates the C2 addresses.
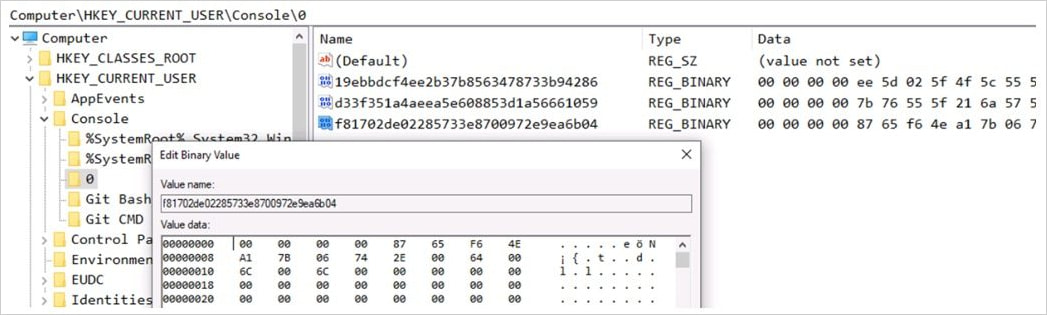
Source: Fortinet
In the last stage of the attack chain, the login module (登录模块.dll) is loaded, which performs the primary malicious actions:
- Collects system and environment information (e.g., IP address, OS details, CPU).
- Checks for anti-virus and monitoring software running on the host.
- Gathers data on specific cryptocurrency wallet extensions used by the victim.
- Maintains a persistent backdoor connection to the C2 server, allowing the attacker to issue commands and retrieve additional data.
- Exfiltrates data after taking screenshots, monitoring for clipboard changes, and stealing documents.
.jpeg)
Source: Fortinet
Winos4.0 checks for a variety of security tools on the system, including Kaspersky, Avast, Avira, Symantec, Bitdefender, Dr.Web, Malwarebytes, McAfee, AhnLab, ESET, Panda Security, and the now discontinued Microsoft Security Essentials.
By identifying these processes, the malware determines if it is running in a monitored environment and adjusts its behavior accordingly, or halts execution.
Hackers have continued using the Winos4.0 framework for several months now, and seeing new campaigns emerging is an indication that its role in malicious operations appears to have solidified.
Fortinet describes the framework as a powerful one that can be used to control compromised systems, with functionality similar to Cobalt Strike and Sliver. Indicators of compromise (IoCs) are available in the reports from Fortinet and Trend Micro.









Comments
EndangeredPootisBird - 1 week ago
I'm still surprised that the developers of pen-testing tools haven't been arrested yet, considering that their tool have done nothing but aid criminals.
amonas - 1 week ago
a screwdriver is a usefull tool. If you use it to stab someone, is it the manufacturer's or the inventor's fault?
powerspork - 1 week ago
Screwdriver analogy sure, but I think Cobalt strike is more akin to a grenade launcher. You can choose to use it in a way that doesn't kill people, but it was made for it.
I agree that the developer should not be liable.However, grenade launchers are tightly controlled for good reasons and I don't see how we can regulate these tools the same way.
MisterVVV - 1 week ago
it's not the developers, it's not the tools, it's the people who use them incorrectly.
//...nice day
PeterAlexLondon - 1 week ago
The American way of life
Guns don't kill people, people kill
Most of them are Christians; god fearing.
Guns should no longer be available for people like that.
The same is for any other kind of weapon.
This must be stopped any how any way
"god bless" y'all
PeterAlexLondon - 1 week ago
Come on get me your replies
PeterAlexLondon - 1 week ago
Maybe a little off topic; really