
DrayTek has released security updates for multiple router models to address 14 vulnerabilities of varying severity, including a remote code execution flaw that received the maximum CVSS score of 10.
The flaws, which Forescout Research – Vedere Labs discovered, impact both actively supported and models that have reached end-of-life. However, due to the severity, DrayTek has provided fixes for routers in both categories.
The researchers warned that their scans revealed that approximately 785,000 DrayTek routers might be vulnerable to the newly discovered set of flaws, with over 704,500 having their web interface exposed to the internet.
Vulnerability details
Most vulnerabilities discovered by Vedere Labs are medium-severity buffer overflow and cross-site scripting problems dictated by several exploitation requirements.
However, five of the flaws carry significant risks, requiring immediate attention. Those are summarized as follows:
- FSCT-2024-0006: A buffer overflow vulnerability in the "GetCGI()" function, responsible for handling HTTP request data, which can lead to denial of service (DoS) or remote code execution (RCE). (CVSS score: 10.0)
- FSCT-2024-0007: Command Injection in OS Communication – The "recvCmd" binary used for communication between the host and guest operating systems is vulnerable to command injection attacks, potentially allowing VM escape. (CVSS score: 9.1)
- FSCT-2024-0014: The web server backend uses a static string to seed the pseudo-random number generator (PRNG) in OpenSSL for TLS connections, which could lead to information disclosure and man-in-the-middle (MiTM) attacks. (CVSS score: 7.6)
- FSCT-2024-0001: The use of identical admin credentials across the entire system can lead to full system compromise if these credentials are obtained. (CVSS score: 7.5)
- FSCT-2024-0002: An HTML page in the Web UI improperly handles input, allowing for reflected XSS vulnerabilities. (CVSS score: 7.5)
As of yet, there have been no reports of active exploitation of these flaws, and the publication of analytical details has been withheld to allow users enough time to apply the security updates.
The above flaws impact 24 router models, of which 11 have reached the end of life yet still received fixes.
The impacted models and target firmware versions to upgrade to can be seen in the table below.
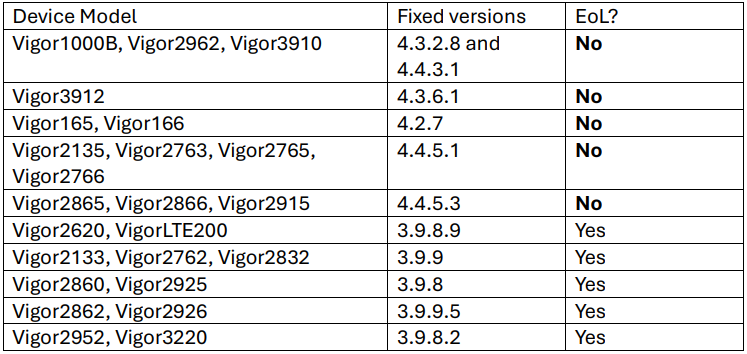
Users may download the latest firmware for their device model from DrayTek's official download portal.
Over 700,000 DrayTex devices exposed online
Verdere Labs reports that it found over 704,500 devices have the DrayTek Vigor Web user interface exposed to the internet, though it should only be accessible from a local network.
Nearly half of the devices under Forescout's direct visibility are located in the United States, but Shodan results show significant numbers in the United Kingdom, Vietnam, the Netherlands, and Australia.
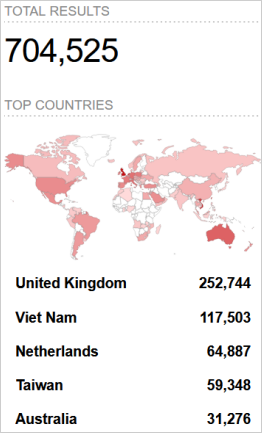
Source: Verdere Labs
Apart from applying the latest firmware updates, users are recommended to take the following actions:
- Disable remote access if not needed, and use an access control list and two-factor authentication when active.
- Check settings for arbitrary alterations or the addition of admin users or remote access profiles.
- Disable SSL VPN connections through port 443.
- Enable syslog logging to monitor for suspicious events.
- Enable auto-upgrade to HTTPs pages on your web browser.
All DrayTek users should confirm that their device's remote access console is disabled, as exploits and brute force attacks commonly target those services.









Comments
TPhillipss - 1 month ago
I have had a look and not sure if it is a typo but the Draytek 2866 latest firmware release is 4.4.5.2 but on your article it says 4.4.5.3