
Over 60,000 Android apps disguised as legitimate applications have been quietly installing adware on mobile devices while remaining undetected for the past six months.
The discovery comes from Romanian cybersecurity firm Bitdefender which detected the malicious apps using an anomaly detection feature added to its Bitdefender Mobile Security software last month.
"To date, Bitdefender has discovered 60,000 completely different samples (unique apps) carrying the adware and we suspect there is much more in the wild," warned Romanian cybersecurity firm Bitdefender.
The campaign is believed to have started in October 2022 and is being distributed as fake security software, game cracks, cheats, VPN software, Netflix, and utility apps on third-party sites.
The malware campaign predominantly targets users in the United States, followed by South Korea, Brazil, Germany, the United Kingdom, and France.
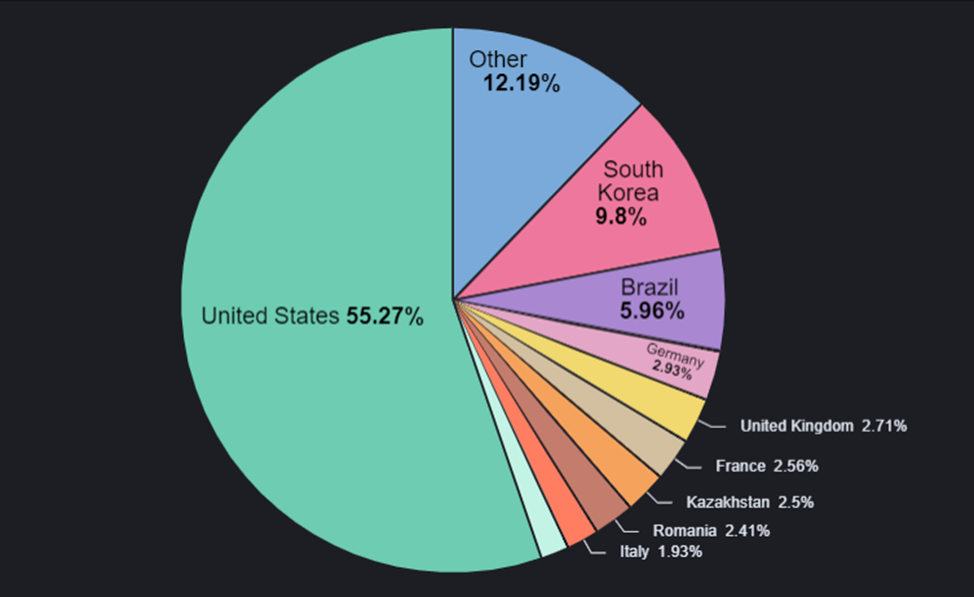
Source: Bitdefender
Stealthily installed to evade detection
The malicious apps are not hosted on Google Play but on third-party websites in Google Search that push APKs, Android packages that allow you to manually install mobile apps.
When visiting the sites, you will either be redirected to websites showing advertisements or prompted to download the searched-for app. The download sites are purposely created to distribute the malicious Android apps as an APK that, when installed, infect the Android devices with adware.
When the app is installed, it does not configure itself to run automatically, as that requires additional privileges. Instead, it relies on the normal Android app installation flow, which prompts users to 'Open' an app after it is installed.
Furthermore, the apps do not utilize an icon and have a UTF-8 character in the app's label, making it harder to spot. This is a double-edged sword, as it also means if a user does not start the app after it's installed, it likely won't be launched after.
If launched, the app will display an error message stating that the "Application is unavailable in your region. Tap OK to uninstall."
However, in reality, the app is not uninstalled but simply sleeps for two hours before registering two 'intents' that cause the app to launch when the device is booted or when the device is unlocked. Bitdefender says the latter intent is disabled for the first two days, likely to evade detection by the user.
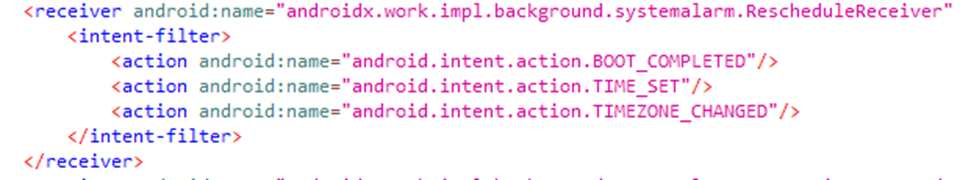
Source: Bitdefender
When launched, the app will reach out to the attackers' servers and retrieve advertisement URLs to be displayed in the mobile browser or as a full-screen WebView ad.
While the malicious apps are currently only used to display advertisements, the researchers warn that the threat actors could easily swap out the adware URLs for more malicious websites.
"Upon analysis, the campaign is designed to aggressively push adware to Android devices with the purpose of driving revenue," warns Bitdefender.
"However, the threat actors involved can easily switch tactics to redirect users to other types of malware, such as banking Trojans to steal credentials and financial information or ransomware."
Android devices are highly targeted by malware developers as they are able to install applications outside of the Google Play Store, where they are not better inspected for malware.
However, threat actors continue to evade detection, even on Google Play, allowing broad distribution of malicious apps.
Just this past week, researchers from Dr. Web and CloudSEK discovered a malicious spyware SDK installed over 400 million times on Android devices from apps on Google Play.
While Google Play still has its share of malicious apps, installing your Android apps from the official Android store is far safer. It is also strongly advised not to install any Android apps from third-party sites, as they are a common vector for malware.









Comments
aztony - 1 year ago
Damn if you do, damn if you don't! Download from the play store is akin to playing Russian roulette. Sideload from another source more roulette...
larkapal - 1 year ago
Where is the list?