
Signal is finally tightening its desktop client’s security by changing how it stores plain text encryption keys for the data store after downplaying the issue since 2018.
As reported by BleepingComputer in 2018, when Signal Desktop for Windows or Mac is installed, it creates an encrypted SQLite database to store a user's messages. This database is encrypted using a key generated by the program and without input from the user.
For a program to be able to decrypt an encrypted database and use it to store data, it must have access to the encryption key. In Signal's case, it stores the key as plain text in a local file called %AppData%\Signal\config.json in Windows and ~/Library/Application Support/Signal/config.json on a Mac.
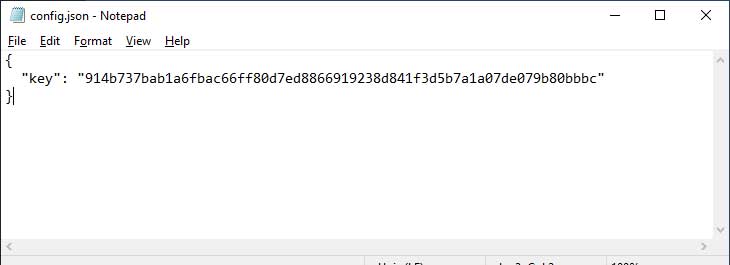
Source: BleepingComputer
However, if Signal can access this key then so can any other user or program running on the computer, making the encrypted database worthless and providing little to no extra security.
One solution offered by the researcher who found this flaw, Nathaniel Suchy, was to encrypt the local database with a user-supplied password that is never stored anywhere, as we see with cloud backup software, web browsers, password managers, and cryptocurrency wallets.
When BleepingComputer contacted Signal about the flaw in 2018, we never received a response.
Instead, a Signal Support Manager responded to a user's concerns in the Signal forum, stating that the security of its database was never something it claimed to provide.
"The database key was never intended to be a secret. At-rest encryption is not something that Signal Desktop is currently trying to provide or has ever claimed to provide," responded the Signal employee.
To be fair to Signal, encrypting local databases without a user-supplied password is a problem for all applications and relies on extra steps to tighten security further.
However, as a company that prides itself on its security and privacy, it was strange that the organization dismissed the issue and did not attempt to provide a solution.
Design flaw resurfaces again on X
Fast-forward almost six years later, and Elon Musk tweeted, "There are known vulnerabilities with Signal that are not being addressed. Seems odd …"
Musk did not share what vulnerabilities he was referring to, and some saw Musk's tweet as an attempt to assist Telegram in a campaign claiming it was more secure than Signal.
Signal President Meredith Whittaker responded that no known vulnerabilities need to be addressed, and if there are, they should be responsibly disclosed to the organization.
"Hi, hello, we don't have evidence of extant vulnerabilities, and haven't been notified of anything. We follow responsible disclosure practices, and closely monitor security@signal.org + respond & fix any valid issues quickly," Whittaker tweeted.
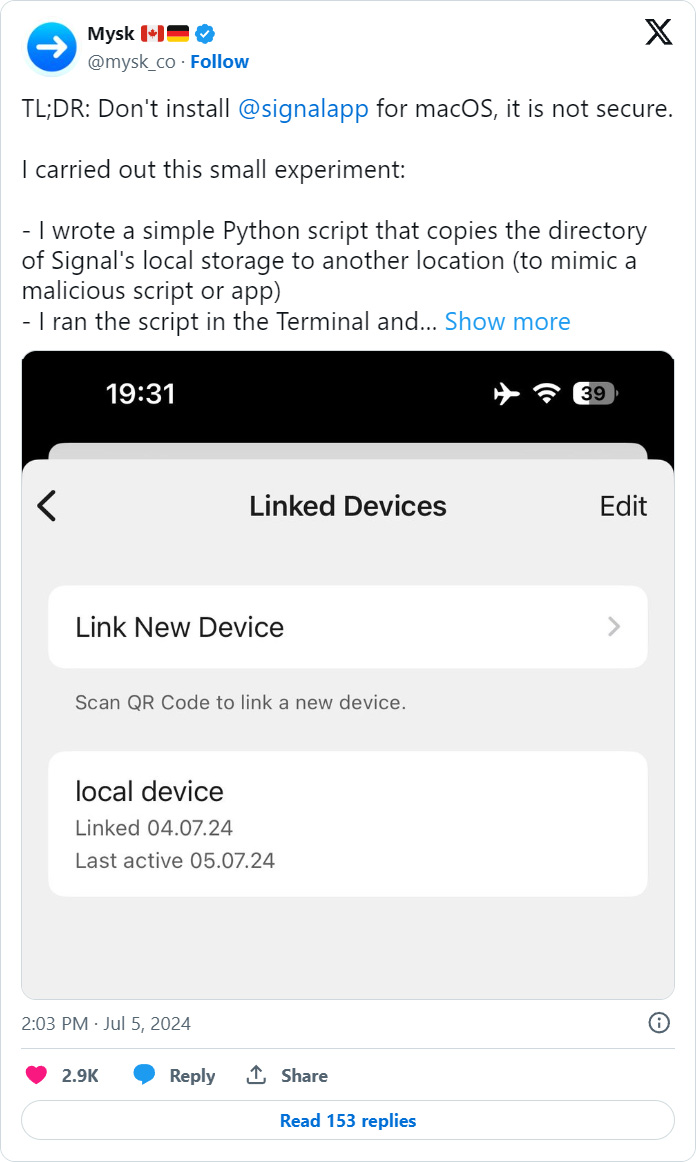
However, last week, mobile security researchers Talal Haj Bakry and Tommy Mysk of Mysk Inc warned on X not to use Signal Desktop because of the same security weakness we reported on in 2018.
In a series of tweets, Mysk Inc illustrated how photos and apps sent through the messaging app are not stored in a secure or encrypted location and that the encryption key for the message store is still stored in plain text on the system.
"The community note is wrong and Elon Musk is right. Signal's desktop apps encrypt local chat history with a key stored in plain text and made accessible to any process," tweeted the researchers in another thread.
"This leaves users vulnerable to exfiltration. The issue was reported in 2018, but it hasn't been addressed"
In response, Whittaker downplayed the flaw, stating that if an attacker has full access to your device, Signal cannot completely protect the data.
"The reported issues rely on an attacker already having *full access to your device* — either physically, through a malware compromise, or via a malicious application running on the same device," Whittaker tweeted.
"This is not something that Signal, or any other app, can fully protect against. Nor do we ever claim to."
While it is unclear what full access to a device means, anyone with remote access or malware running on the device could access the data.
The response was unusual after Whittaker's constant retweets about the security and privacy implications of Microsoft's Windows Recall and how data could be stolen by local attackers or malware.
While the Windows Recall feature undoubtedly consumes far more sensitive data, similar concerns could be applied to Signal, which is used for confidential messaging that, in some countries, could land a person in prison.
However, Microsoft responded to the much-deserved criticism by saying they would delay the release of Windows Recall to add additional protections to secure collected data from local attacks and test the product further.
Signal will now tighten database encryption
In April, an independent developer, Tom Plant, created a request to merge code that uses Electron's SafeStorage API to further secure Signal's data store from offline attacks.
"As a simple mitigation, I've implemented Electron's safeStorage API to opportunistically encrypt the key with platform APIs like DPAPI on Windows and Keychain on macOS," Plant explained in the merge request.
Electron's safeStorage API provides additional methods to secure the encryption key used to encrypt data stored locally on a device.
When used, encryption keys are generated and stored using an operating system's cryptography system and secure key stores. For example, on Macs, the encryption key would be stored in the Keychain, and on Linux, it would use the windows manager's secret store, such as kwallet, kwallet5, kwallet6, and gnome-libsecret.
The safeStorage API falls short for Windows, as it uses DPAPI, which only secures the encryption key against other users on the same device. That means any program or malware running under the same user context as the one who uses Signal would theoretically be able to access the data.
While the solution would provide additional security for all Signal desktop users, the request lay dormant until last week's X drama. Two days ago, a Signal developer finally replied that they implemented support for Electron's safeStorage, which would be available soon in an upcoming Beta version.
While the new safeStorage implementation is tested, Signal also included a fallback mechanism that allows the program to decrypt the database using the legacy database decryption key.
"In addition to migrating to encrypted/keystore-backed local database encryption keys on supported platforms, our implementation also includes some additional troubleshooting steps and a temporary fallback option that will allow users to recover their message database using their legacy database encryption key if something goes wrong," explained Signal developer Jamie Kyle.
"This should help minimize data loss if any edge cases or other keystore-related bugs are discovered during the migration process and production rollout.
Signal says that the legacy key will be removed once the new feature is tested.
Though its good to see that we have these additional protections coming to Signal, some are disappointed it only happened after the uproar on X.
BleepingComputer contacted Signal with further questions but has yet to receive a response.









Comments
GT500 - 4 months ago
I've never considered Signal to be a safe messenger service to use. The fact that originally you couldn't sign up for it unless you gave them your entire contact list on your phone was pretty telling.
pnda73 - 4 months ago
That's just the way signal works, it uses phone numbers to contact people just like many other messaging apps, the only difference though is it's commitment to privacy security and E2EE (regardless of this not making them look good).
If you want, there are other less popular apps that allow you to use an alias and you don't need any number, but to kerb spam/bots Signal wanted to hold off.
To accuse Signal of being insecure because it needs your contact list to functions is ridiculous, it's a messaging app, that's the reason the permission was created for Android to begin with. You simply seem fatigued by all the permissions random apps need, but that's no reason to take a snipe at Signal!
GT500 - 4 months ago
It wasn't the fact that it used phone numbers that was the issue. It was the fact that giving the app your entire contact list was mandatory was the issue.
fidetev87 - 3 months ago
This is false. You have never been required to give permissions to your contact list. The app worked just fine without it. Perhaps you're confusing it with WhatsApp.
beepboopboopbleeep - 4 months ago
Why not link Mysk Fediverse posts instead of X posts? Why push X in 2024?!
NoneRain - 4 months ago
Push? Aren't the original posts in X? Bro, you care about such trivial stuff....
jipjip - 4 months ago
If malware has access to your system, all these solutions are pointless. These solutions only mitigate the situation where the attacker has already stolen your signal data but lost remote access to your device.
AdvancedSetup - 4 months ago
Not true. Just because a system is infected does not mean it can decrypt encrypted data from Signal or any other application. It might be able to intercept current communications but it cannot go decrypt old messages without the key
AdvancedSetup - 4 months ago
There are other apps don't force you to use your contact list. That is a complaint many have made. I use secure messaging for about ten people the other fifty people don't use any type of secure messaging and I don't need the marketing of Signal contacting them asking them to install it. I will decide who I want to use secure messaging with.
Figueiredo - 3 months ago
Mr. Elon Musk buy Signal app, remove people linked to the CIA/Deep State/WEF, call Mr. Edward Snowden to enhance security and encryption, keep the Signal app simple as it is for messaging and video.
Make Signal Great Again.