
Over 90 malicious Android apps were found installed over 5.5 million times through Google Play to deliver malware and adware, with the Anatsa banking trojan seeing a recent surge in activity.
Anatsa (aka "Teabot") is a banking trojan that targets over 650 applications of financial institutions in Europe, the US, the UK, and Asia. It attempts to steal people's e-banking credentials to perform fraudulent transactions.
In February 2024, Threat Fabric reported that since late last year, Anatsa had achieved at least 150,000 infections via Google Play using various decoy apps in the productivity software category.
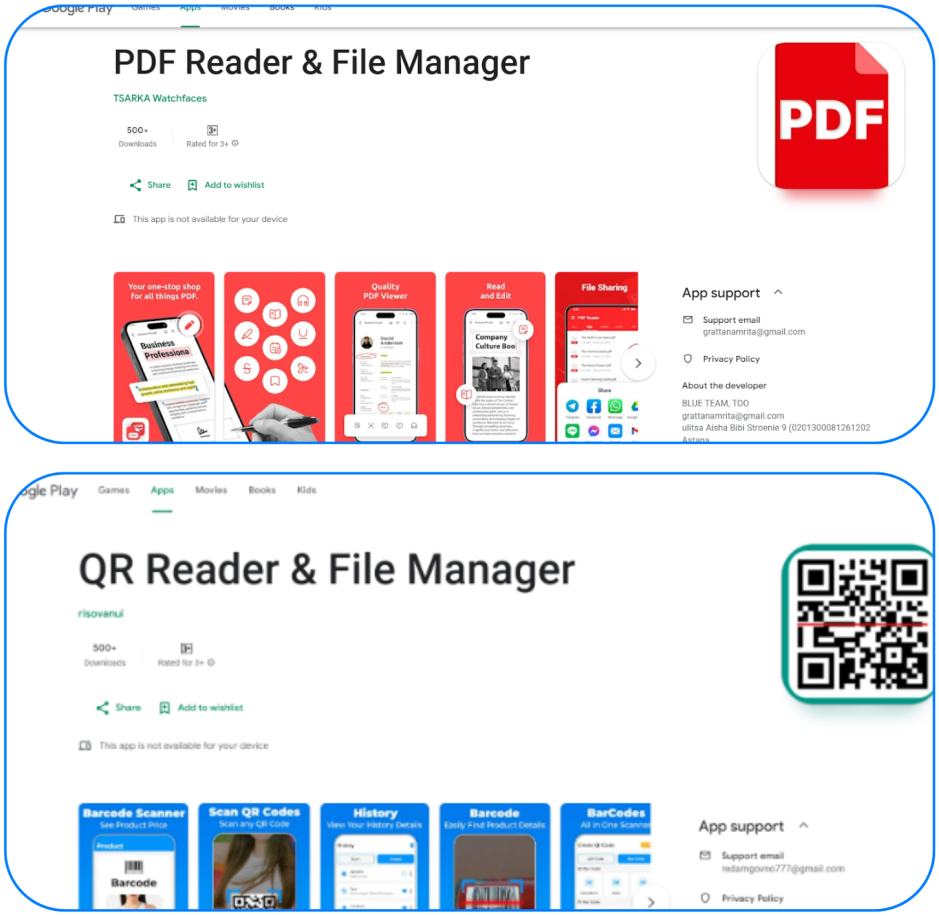
Today, Zscaler reports that Anatsa has returned to Android's official app store and is now distributed via two decoy applications: 'PDF Reader & File Manager' and 'QR Reader & File Manager.'
Source: Zscaler
At the time of Zscaler's analysis, the two apps had already amassed 70,000 installations, demonstrating the high risk of malicious dropper apps slipping through the cracks in Google's review process.
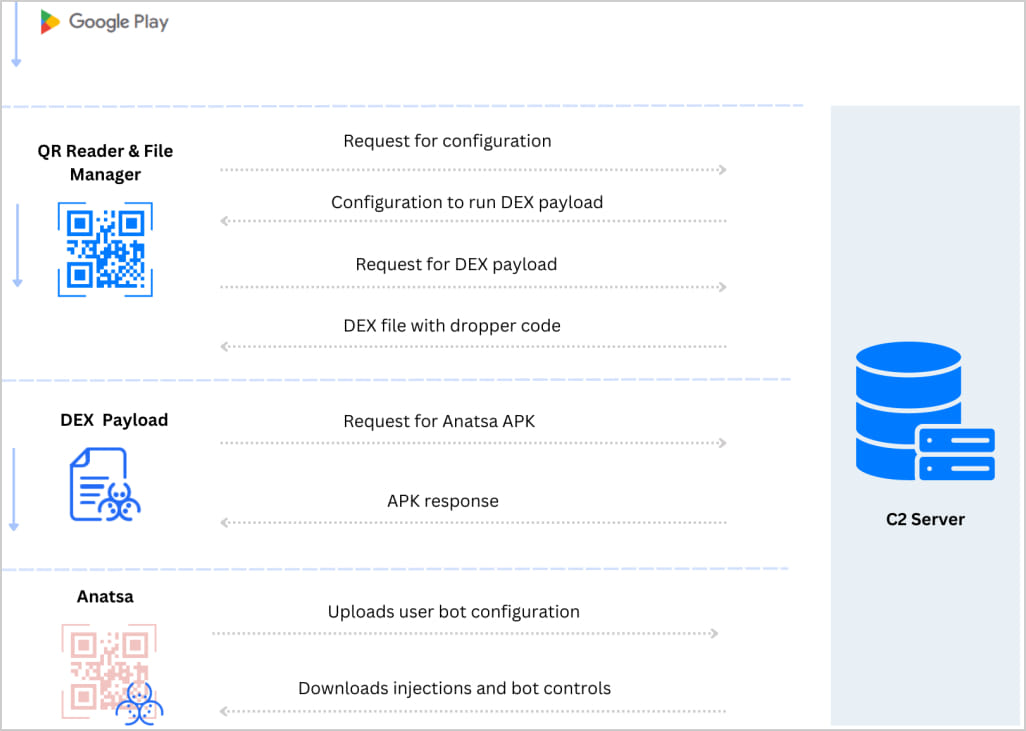
One thing that helps Anatsa dropper apps evade detection is the multi-stage payload loading mechanism that involves four distinct steps:
- Dropper app retrieves configuration and essential strings from the C2 server
- DEX file containing malicious dropper code is downloaded and activated on the device
- Configuration file with Anatsa payload URL is downloaded
- DEX file fetches and installs the malware payload (APK), completing the infection
Source: Zscaler
The DEX file also performs anti-analysis checks to ensure the malware won't be executed on sandboxes or emulating environments.
Once Anatsa is up and running on the newly infected device, it uploads the bot configuration and app scan results and then downloads the injections that match the victim's location and profile.
Source: Zscaler
Other Google Play threats
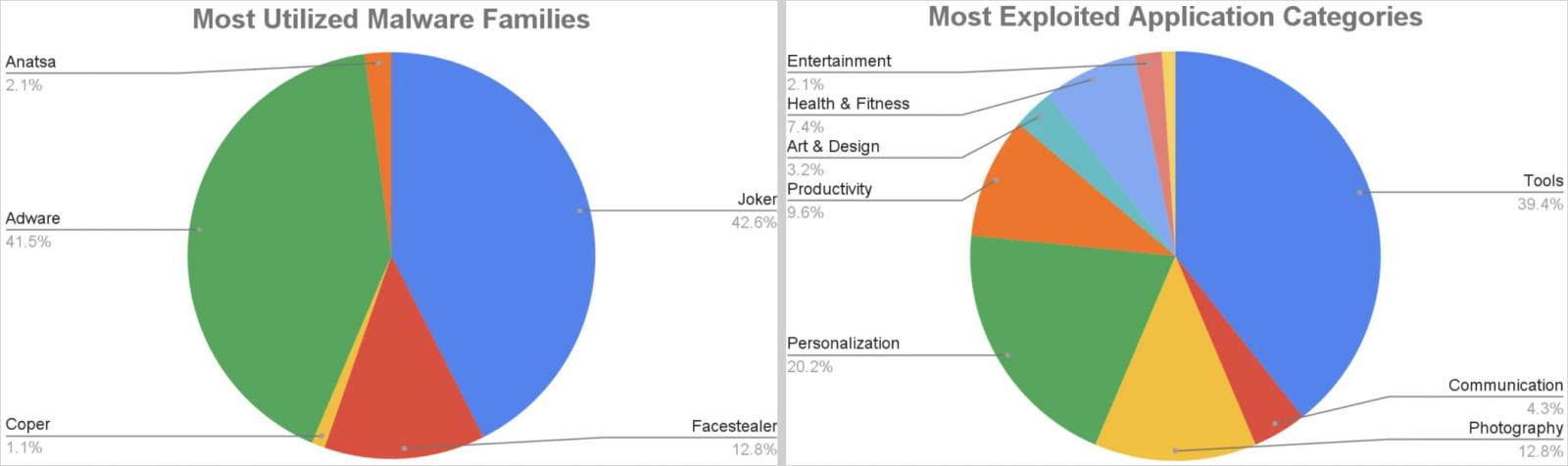
Zscaler reports that during the past couple of months, it has also discovered over 90 malicious applications on Google Play, which were collectively installed 5.5 million times.
Most of the malicious apps impersonated tools, personalization apps, photography utilities, productivity, and health & fitness apps.
The five malware families dominating the scene are Joker, Facestealer, Anatsa, Coper, and various adware.
Source: Zscaler
Though Anatsa and Coper only account for 3% of the total malicious downloads from Google Play, they are far more dangerous than the others, capable of performing on-device fraud and stealing sensitive information.
When installing new apps on Google Play, review the requested permissions and decline those associated with high-risk activities such as Accessibility Service, SMS, and contacts list.
The researchers did not disclose the names of the 90+ apps and whether they had been reported to Google for takedown.
However, at the time of writing this, the two Anatsa dropper apps discovered by Zscaler have been removed from Google Play.
Update 5/30 - A Google spokesperson told BleepingComputer that the developers behind the offending apps have been banned, and shared the following statement:
All of the identified malicious apps have been removed from Google Play.
Google Play Protect also protects users by automatically removing or disabling apps known to contain this malware on Android devices with Google Play Services.









Comments
povlhp - 5 months ago
What is malware ? I can point to 20+ mio installs among <5 apps. Controlled by Putler's friends. They might not be malicious right now, but they might be spying, delivering crap in peoples mail, and could pull malware from the servers.
Basically, everything that talks to the net could pull down malware. Thus you need to trust the developer/backend owner.
powerspork - 5 months ago
Malware in this context is referring to software that was designed to steal sensitive data, with all other goals being secondary. Legitimate software that can be modified to be malicious is not inherently malicious in nature.
The state of the industry indicates we should do everything we can in the browser, not an app, and the rest should be done on a PC using vetted software. Just about everyone is out to "steal" some amount of data from you for their own purposes, though some are clearly more dangerous than others.
NoneRain - 5 months ago
Software that collects data/do stuff illegitimately are malware. Even if in today's world data collection get kinda crazy, companies must comply with regulations and laws. Softwares that fail to comply AND can't be held responsible, can be considered malware.
If the intent of the software is to do malicius stuff, malware.
"Basically, everything that talks to the net could pull down malware. Thus you need to trust the developer/backend owner." - yep. That's why is so important to install apps only from devs you know are unlikely to go rogue.
Dr. Technical - 5 months ago
What exactly is the process by which any app is declared "safe" to include in Google's app store? What does the process look for? What does it consider dicey enough to ban from the store? Does it consider an app acceptable even though it connects constantly to one or more servers? Is there any auditing of what information is sent to those servers, how often and for what purpose?
To my mind, acceptance in any of the app stores is absolutely no assurance that the app is safe to use.
MarkMandyT - 5 months ago
My thoughts exactly. As for using how many servers and how long an app connects to them,; I’ll argue that really can’t be a metric. I’m sure my driving, hiking and other legitimate apps that I need running very well might connected to multiple servers and constantly at that.
I’d have really appreciated a list of those 90+ apps that were identified. The update didn’t actually say the full set was removed from Google’s Play Store or just the two “main” ones discussed. Additionally, even though the apps were removed is there any notice to [active] users of those that they’ve been deemed malicious? If not there’s absolutely no value added by Bleeping Computer publishing articles such as this or Google’s anti-malware efforts.
Hmm888 - 5 months ago
What kind of clickbait is this? 90 malware applications referred to but only 2 listed? You're digging yourself into a hole BC. Soon nobody is going to visit your site unless you stop with these kinds of shenanigans..
buddy215 - 5 months ago
Reread the article. Your comment says you didn't comprehend what was written.