Google has released the September 2024 Android security updates to fix 34 vulnerabilities, including CVE-2024-32896, an actively exploited elevation of privilege flaw that was previously fixed on Pixel devices.
The high-severity vulnerability is related to a logic error in the code, which allows an attacker to bypass certain protections on Android and elevate their privileges without requiring additional permissions. However, user interaction is necessary for the attack to work.
The flaw was fixed for Pixel devices in June 2024 and was marked as actively exploited in limited, targeted attacks, including by forensics companies, to stop auto-wiping tools like Wasted and Sentry from triggering when devices are examined.
Android's latest security update now fixes CVE-2024-32896 for devices running Android 12, 12L, 13, and 14.
The rest of the fixes that landed this month all concern high-severity issues except for two vulnerabilities in closed-course Qualcomm components, specifically the WLAN subcomponent, tracked as CVE-2024-33042 and CVE-2024-33052.
The limited information provided by Qualcomm on these flaws categorizes both as memory corruption problems in the FM Host component, only exploitable locally (physical access or previous compromise by malware).
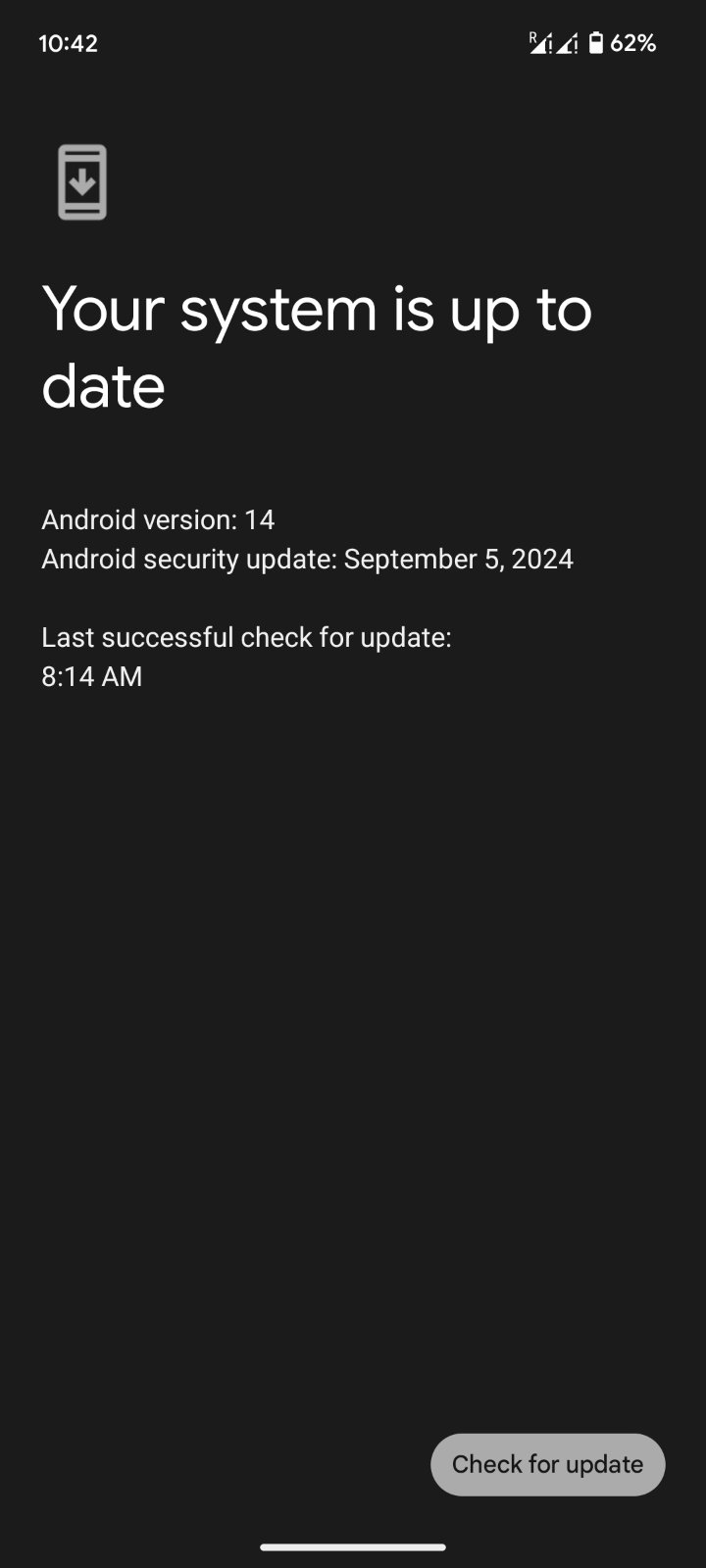
Given that Google's September 2024 security patches for Android address an actively exploited vulnerability, it is recommended that all Android users apply the update as soon as possible.
To do so, navigate to Settings > System > Software updates > System update. Alternatively, head to Settings > Security & privacy > System & updates > Security update, and click on the 'Check for update' button.
If you're using Android 11 or earlier, your device is no longer actively supported, and you're recommended to switch to a newer model or install a third-party Android distribution that incorporates important security fixes.
Pixel fixes out as well
At the same time as the Android security updates, Google released patches for its Pixel devices (series 6 and later).
The latest pack of fixes addresses six elevation of privilege and information disclosure flaws, four of which, in the Local Control Subsystem (LCS) and Low-level Device Firmware (LDFW) components, are rated critical.
Those are CVE-2024-44092 (LCS), CVE-2024-44093 (LDFW), CVE-2024-44094 (LDFW), and CVE-2024-44095 (LDFW), all elevation of privilege problems.
Though Pixel users have had a turbulent experience with security updates this year, there are no reports that this latest update is causing unexpected trouble.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now