
Google announced today the beta release of Security Health Analytics, a product designed to help Google Cloud Platform (GCP) admins take action after identifying security misconfigurations or compliance violations.
"Today, we’re excited to announce the beta of Security Health Analytics, a security product that integrates into Cloud Security Command Center (Cloud SCC)," says Google product manager Kyle Olive.
After enabling Security Health Analytics, it will automatically run scans twice each day, 12 hours apart, checking for vulnerabilities and misconfigurations in GCP across multiple resources.
"At beta, products or features are ready for broader customer testing and use. Betas are often publicly announced," says Google Cloud Platform's info on product launch stages.
"There are no SLAs or technical support obligations in a beta release unless otherwise specified in product terms or the terms of a particular beta program. The average beta phase lasts about six months."
Comes with several built-in scanners
At the moment, Google's Security Health Analytics can scan for issues affecting Stackdriver Monitoring and Stackdriver Logging, Compute Engine, Google Kubernetes Engine containers and networks, Cloud Storage, Cloud SQL, Cloud Identity and Access Management (Cloud IAM), Cloud Key Management Service (Cloud KMS), and Cloud DNS.
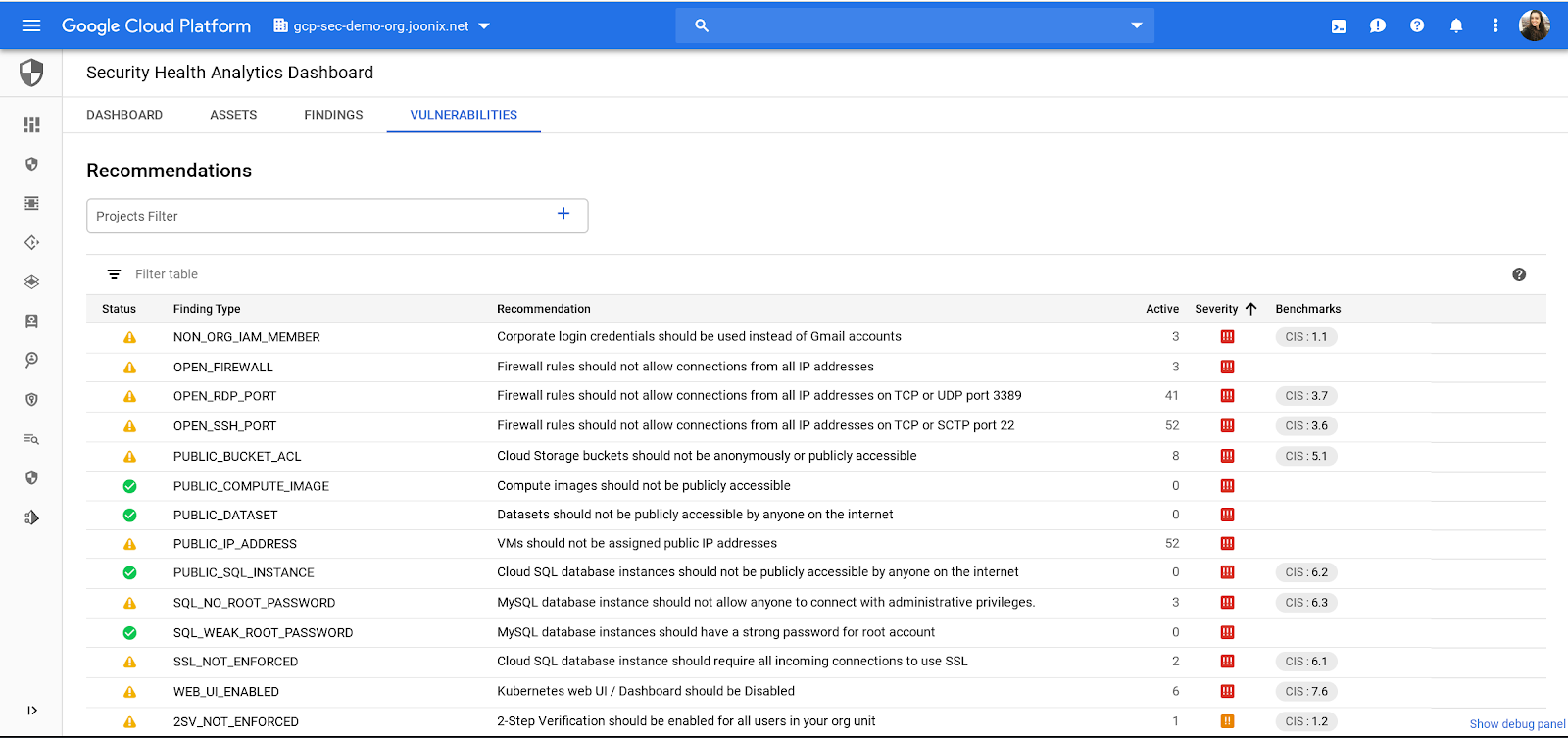
Security Health Analytics can display a wide array of information related to the security issues it discovers using its built-in scanners, including:
• API key vulnerability findings
• Compute image vulnerability findings
• Compute instance vulnerability findings
• Container vulnerability findings
• Dataset vulnerability findings
• DNS vulnerability findings
• Firewall vulnerability findings
• IAM vulnerability findings
• KMS vulnerability findings
• Logging vulnerability findings
• Monitoring vulnerability findings
• Network vulnerability findings
• SSH password vulnerability findings
• SQL vulnerability findings
• Storage vulnerability findings
• Subnetwork vulnerability findings
"You can filter findings by scanner name and finding type using the Cloud SCC Analytics tab in the Google Cloud Platform Console," says Google.
To be able to view Security Health Analytics findings within Cloud SCC, you have to enable it as a security source using the following steps (requires the Security Center Admin Cloud IAM role):
- Go to the Security Command Center Security Sources page in the GCP Console.
- Under Enabled, click to enable Security Health Analytics.
Step-by-step remediation plan
The Security Health Analytics Vulnerabilities Dashboard allows you to view all potential security issues found during the scanning stage, listed as findings.
Each of the findings provides you with a detailed remediation procedure when clicked designed to help one solve the identified issue like "overly privileged access to a storage bucket" or "an open firewall," as well as a direct link to the affected resource.

With the beta release, Google added support for CIS benchmarks into Security Health Analytics to allow IT professionals to actively monitor for assets that violate CIS recommendations.
"Security Health Analytics is now fully certified by the Center for Internet Security (CIS) to monitor Google Cloud Platform Foundation benchmarks—recommendations for keeping your GCP resources secure and compliant," adds Olive.
For instance, by monitoring GCP assets, publicly accessible storage buckets can be easily identified thus preventing possible data leaks or breaches.
Google provides an extensive list of techniques and reference guides for managing and remediating Security Health Analytics findings with Cloud SCC.
If you want to give it a try, you can start a free GCP trial, enable Cloud SCC, and turn on the Security Health Analytics source as detailed above.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now