
A phishing campaign dubbed 'Phish n' Ships' has been underway since at least 2019, infecting over a thousand legitimate online stores to promote fake product listings for hard-to-find items.
Unsuspecting users clicking on those products are redirected to a network of hundreds of fake web stores that steal their personal details and money without shipping anything.
According to HUMAN's Satori Threat Intelligence team that discovered Phish n' Ships, the campaign has impacted hundreds of thousands of consumers, causing estimated losses of tens of millions of dollars.
The Phish n' Ships operation
The attack starts by infecting legitimate sites with malicious scripts by exploiting known vulnerabilities (n-days), misconfigurations, or compromised administrator credentials.
Once a site is compromised, the threat actors upload inconspicuously named scripts such as "zenb.php" and "khyo.php," with which they upload fake product listings.
These items are complete with SEO-optimized metadata to increase their visibility on Google search results, from where victims can be drawn.
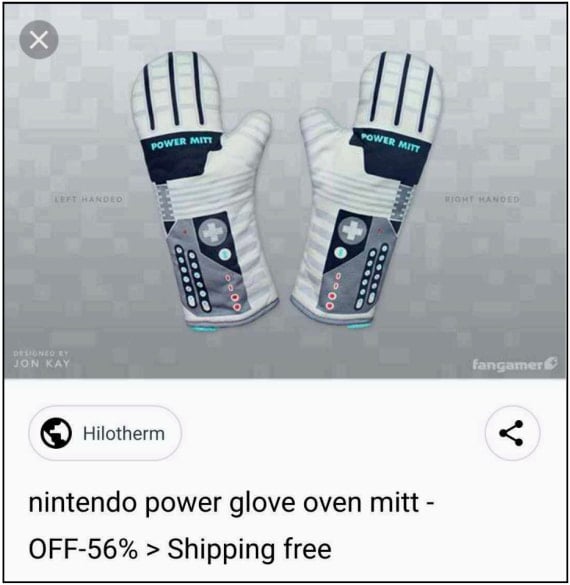
Source: HUMAN
When victims click on these links, they are redirected through a series of steps that ultimately lead to fraudulent websites, often mimicking the interface of the compromised e-store or using a similar design.
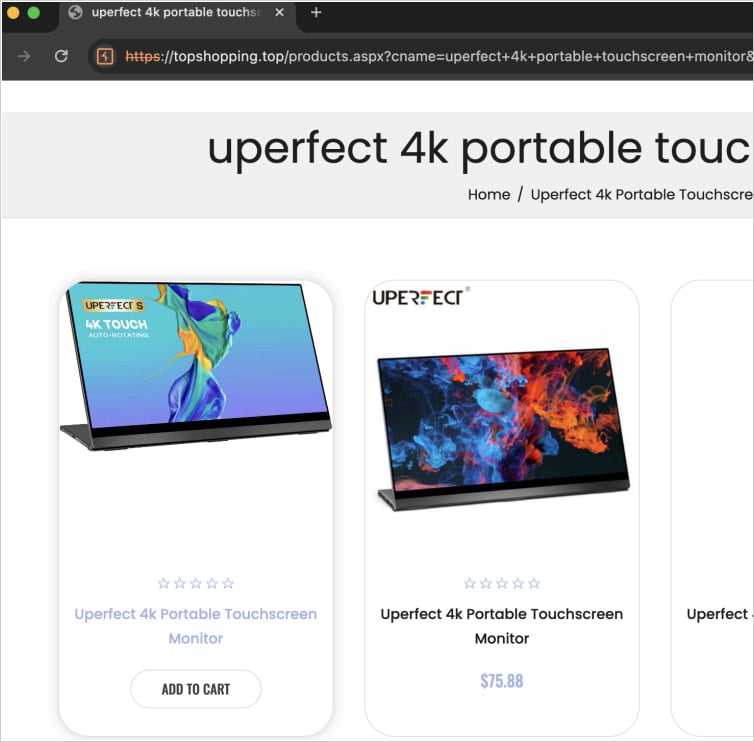
Source: HUMAN
All of these fake shops are connected to a network of fourteen IP addresses, according to Satori researchers, and they all contain a particular string in the URL that makes them identifiable.
Attempting to purchase the item on the fake shop takes victims through a fake checkout process designed to appear legitimate but does not include any data verification, a sign of potential fraud.
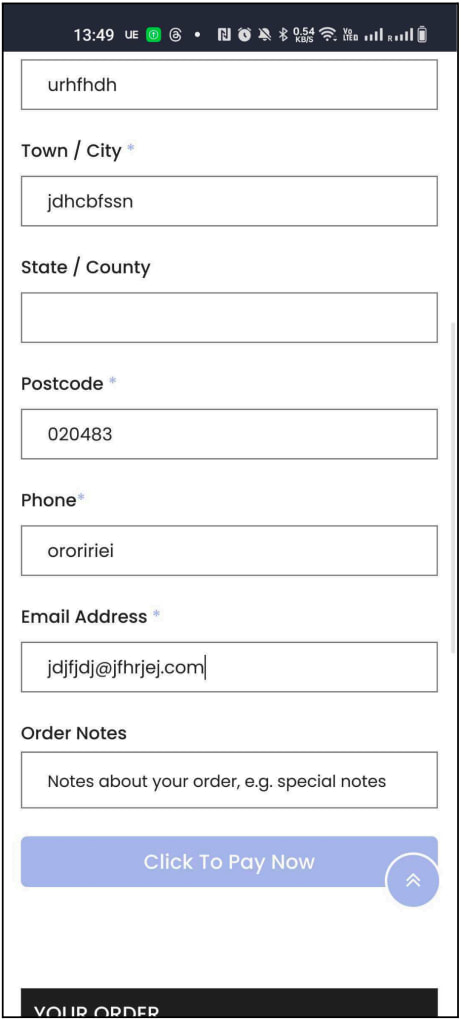
Source: HUMAN
The malicious sites steal the information victims enter in the order fields, including their credit card details, and complete the payment using a semi-legitimate payment processor account controlled by the attacker.
The purchased item is never shipped to the buyer, so the victims lose both their money and data.
Satori has found that over the five years during which Phish n' Ships has been active, the threat actors abused multiple payment providers to cash out the proceeds of the scam.
More recently, they adapted to implementing a payment mechanism on some of the fake e-shop sites so they can snatch the victim's credit card details directly.
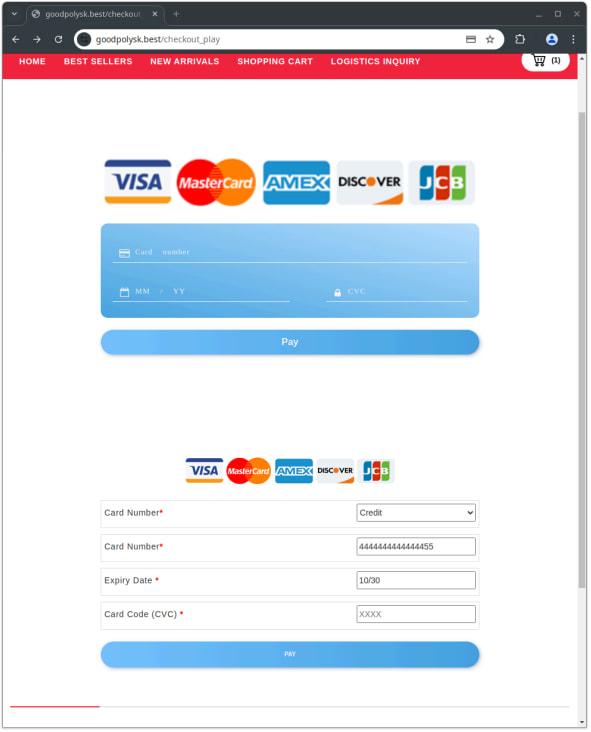
Source: HUMAN
Campaign disrupted
HUMAN and its partners coordinated a response to Phish n' Ships, informing many of the impacted organizations and reporting the fake listings to Google so they could be removed.
As of writing, most malicious search results have been cleaned, and nearly all identified shops have been taken offline.
Also, payment processors who facilitated cashouts for the fraudsters were informed accordingly and removed the offending accounts from their platforms, significantly disrupting the threat actor's ability to generate profit.
Despite all that, the threat actors can adapt to this disruption. Although Satori continues monitoring the activity for resurgence, it's unlikely that they will give up and not try to establish a new shopper-defrauding network.
Consumers are recommended to look out for unusual redirects when browsing e-commerce platforms, validate they are on the correct shop URL when attempting to buy an item, and report fraudulent charges to their bank and authorities as soon as possible.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now