
Hackers have compromised the website of the world-famous Tupperware brand and are stealing customers' payment card details at checkout. The risk existed for a while as researcher’s attempts to alert the company remained unanswered.
Some localized versions of the official Tupperware website were also running malicious code that skims credit card data.
The attack was carefully orchestrated to keep the skimmer active for as long as possible - a clear indication that this is not the work of run-of-the-mill MageCart attackers.
Clever tactic
The hackers used an ingenious method to steal credit card data from Tupperware customers at checkout: they integrated a malicious iframe that displays a fake payment form fields to shoppers.
Discovered by researchers at Malwarebytes, the iframe loaded the content from “deskofhelp[.]com,” a domain that was created on March 9 and it is hosted on a server with multiple phishing domains.

Tupperware fixed the issue and the payment form is currently loading from the legitimate domain cybersource.com, owned by Visa. However, code from the attackers is still available.
The researchers looked closer at the domain hosting the malicious content and noticed that it was registered with a Yandex email address, something that is downright suspicious when it comes to loading payment forms on a US-branded website.
The fraudsters made an effort to conceal the compromise by loading the iframe dynamically on the checkout page. Thus, looking at the HTML source code shows nothing dubious.
However, checking the iframe source revealed the malicious domain hosting the iframe content.

Multiple localized Tuppperware sites were compromised in the same way and one mistake the attackers made was that they used the same payment form on all of them.
As such, the Spanish version of Tupperware site loaded the attacker’s payment form in English, Jérôme Segura from Malwarebytes writes in a report today, while the legitimate form is localized.
To keep shoppers unaware of the credit card skimming, they would see an error immediately after entering the sensitive data. Next, the page would be reloaded with the legitimate form and they could complete the purchase.
“Upon close inspection, we see the fraudsters even copied the session time-out message from CyberSource, the payment platform used by Tupperware. The legitimate payment form from CyberSource includes a security feature where, if a user is inactive after a certain amount of time, the payment form is cancelled and a session time-out message appears” - Jérôme Segura, Malwarebytes
Tupperware customer data collected by cybercriminals this way includes first and last name, billing address, phone number, credit card number, credit card expiry date, and the CVV (card verification value, required for online shopping).
How the rogue iframe came to load on Tupperware website is also interesting. Segura found a snippet of code on the homepage that was dynamically calling a FAQ icon from Tupperware server.
The icon loaded silently and invisibly to shoppers and contained malicious JavaScript responsible for loading the attackers’ iframe on the checkout page.
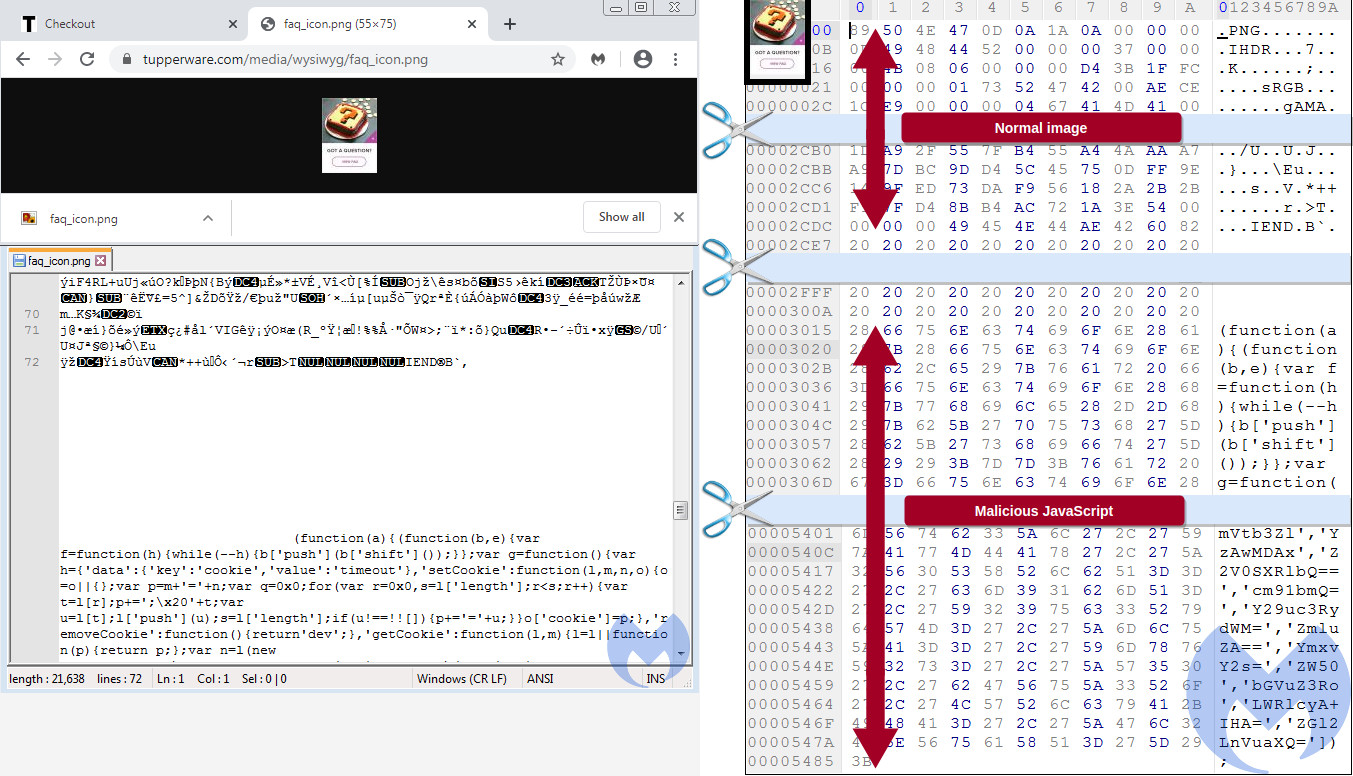
It is unclear for how long the malicious activity survived on Tupperware website but the March 9 registration date of domain hosting the fake payment form is an indication; especially since the rogue code was not present in February.
Incomplete cleanup
As for how the compromise happened, Segura found a possible answer by using Sucuri’s SiteCheck service, which shows that the website is running an outdated version of Magento e-commerce software.
Tupperware did not respond to Malwarebytes's attempts to disclose the breach responsibly but did take action to remove the risk to customers.
The PNG file with code that loaded the iframe is no longer available on the website but the script that called it in the first place is still present, Segura told BleepingComputer.
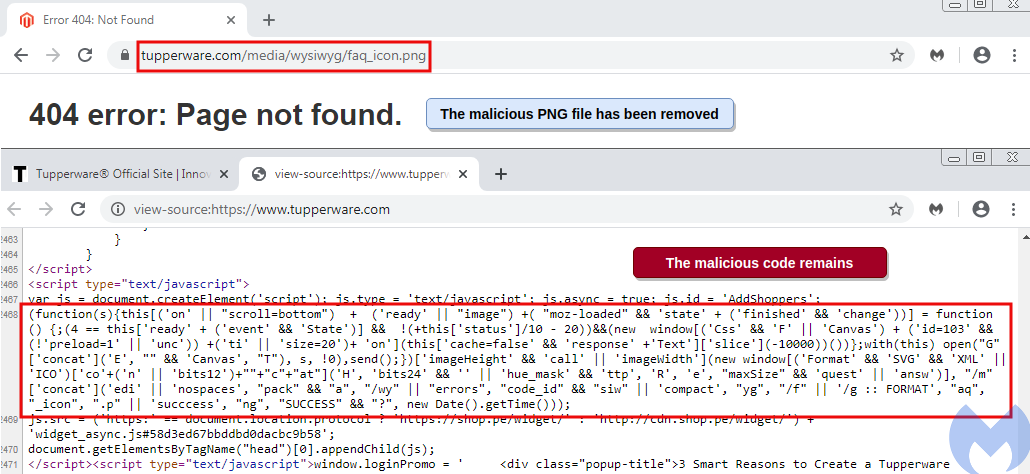
The researcher says that shutting hackers out of a website requires deep inspection to determine how the compromised happened in the first place and to make sure that there are no vulnerabilities that could lead to a new breach.
"Like any website compromise, it is important to look for the root cause by inspecting server side logs and determine if the attackers still have access. Often times, criminals will leave PHP backdoors or can simply re-exploit the same vulnerability to get back in" - Jérôme Segura, Malwarebytes
Update March 25, 11:22 EDT: A tweet from Malwarebytes informs that Tupperware removed the rest of the client-side malicious artifacts. Hopefully, the company did a thorough investigation to close any gaps that hackers might use for a future attack.









Comments
AppSecGuy - 4 years ago
When you say the iframe was loaded dynamically and the HTML showed nothing dubious, are you saying that the malicious javascript in the image file modified the DOM to create the iframe element? Or that the malicious javascript in the image file loaded another js file that modified the DOM to create the iframe element ? or some other dynamic mechanism?