
An unpatched zero-day vulnerability exists in KDE 4 & 5 that could allow attackers to execute code simply by tricking a user into downloading an archive, extracting it, and then opening the folder.
BleepingComputer has been contacted by security researcher Dominik Penner about a new vulnerability that he disclosed for the Linux KDE desktop environment.
"KDE 4/5 is vulnerable to a command injection vulnerability in the KDesktopFile class. When a .desktop or .directory file is instantiated, it unsafely evaluates environment variables and shell expansions using KConfigPrivate::expandString() via the KConfigGroup::readEntry() function. Using a specially crafted .desktop file a remote user could be compromised by simply downloading and viewing the file in their file manager, or by drag and dropping a link of it into their documents or desktop."
According to Penner, this vulnerability exists in KDE version 4 and 5 and allows commands embedded in .desktop and .directory files to be executed simply by opening a folder, or in some cases, extracting an archive to the desktop.
Penner reported the bug to Ubuntu after publicly disclosing it. The researcher originally didn't report it as he "wanted to drop a 0day for Defcon that people could experiment with".
Almost all Linux distributions are currently utilizing vulnerable versions of KDE.
Shell expansion leads to code execution
Freedesktop.org-compliant desktop environments utilize special .desktop and .directory files that are used to configure how applications and folders are displayed.
A .desktop file is used to register an application in the KDE menu, while the .directory files are used to describe how KDE should display a folder. For Windows users. the .directory file is similar to the desktop.ini file.
In each of these files are various fields that tell the desktop environment how a directory or application should appear. One of these fields is called "Icon" and in .desktop files it specifies the path to the icon that KDE should display in menus and for .directory files it will specify the icon used for a folder when viewed in Dolphin.
In conversations with BleepingComputer, Penner explained that the problem is that KDE allows shell expansion to be used to dynamically generate the value of these fields through an environment variable or by executing a command.
"They use the same syntax as the freedesktop specification, however because they also allow the shell expansion (freedesktop doesn't allow this ifself), it's exploitable. It's more of a design flaw than anything, the configuration syntax for .desktop and .directory files should be consistent with that of XDG (freedesktop)'s spec.
And yeah, any entry can be injected. Theoretically this could be exploited in a lot of other areas, however it's easiest to get the entry read via icons"
As these types of files are automatically read when viewed in Dolphin or from the Desktop, it allows an attacker to craft malicious .desktop and .directory folders that execute commands located in the "Icon" field.
When asked if there is a way to mitigate this flaw, Penner told us that the fix has to come from KDE and that disabling file-previews does not help either.
"Even if you were to disable file-previews in the view properties of the file manager, it still triggers."
Testing the flaw
In tests conducted by BleepingComputer, this flaw is ridiculously easy to abuse to perform code execution on vulnerable machines.
In our test, we simply created a ZIP file that contains a subfolder with a .directory file. This directory file's Icon field contains a command to download a test.sh script from our servers and execute it to launch Kcalc.
Once a user downloads the test.zip file, extracts it, and opens it, KDE will read the .directory file and execute the command assigned to the Icon field. You can see a demonstration of this PoC in action below.
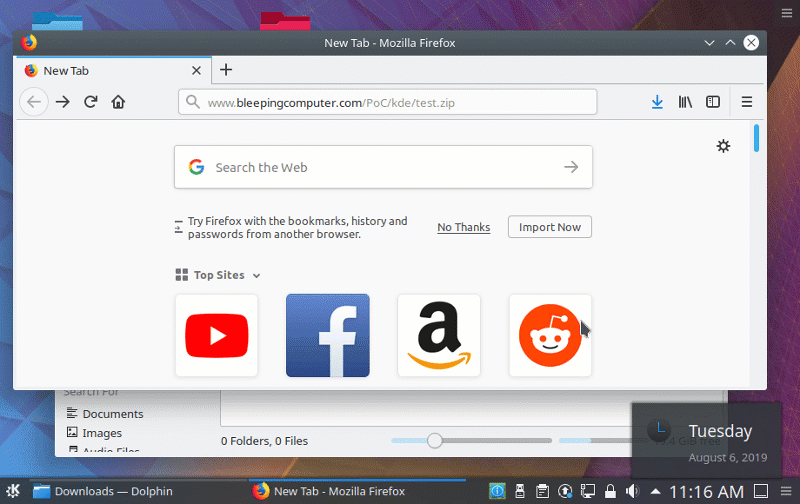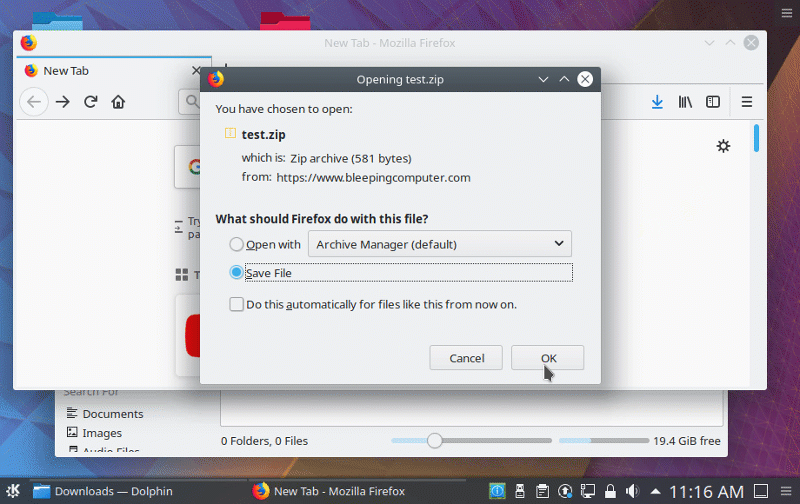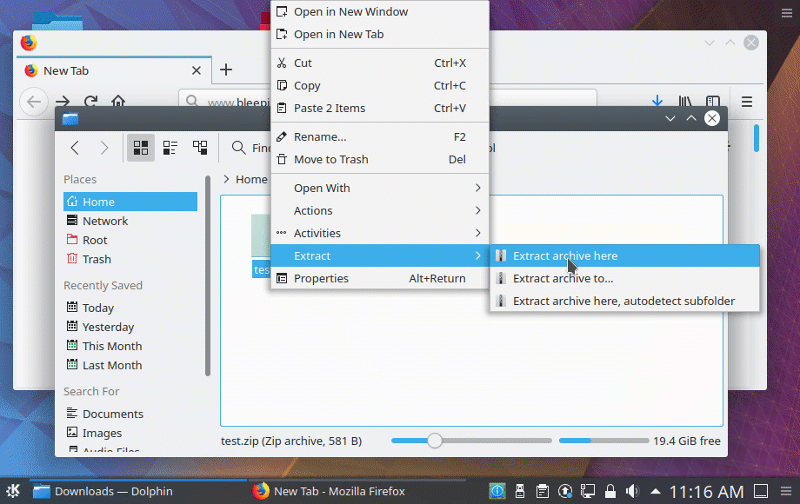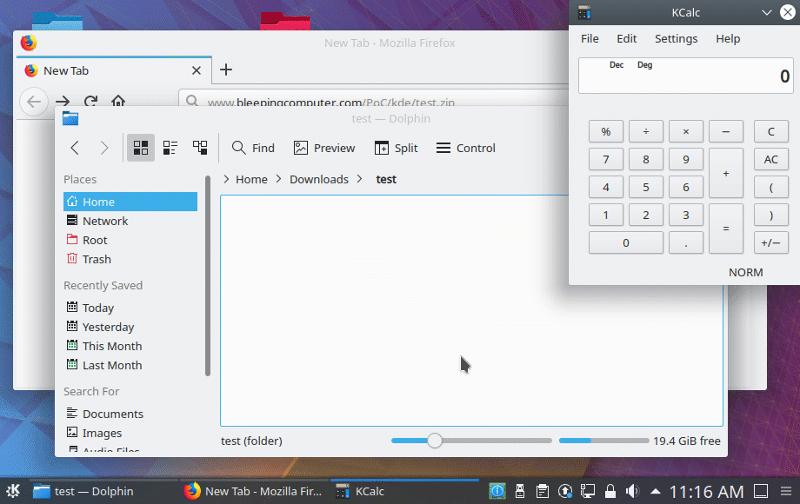
Penner also created a demonstration video showing how this bug can be used to open a reverse shell.
At this time, there is no way to turn off shell expansion in order to mitigate this flaw. Penner recommends users check any .desktop or .directory files and disable any dynamic entries.
BleepingComputer has contacted Ubuntu and Fedora about this bug, but had not heard back at the time of this publication.









Comments
NickAu - 5 years ago
Quote
" An unpatched zero-day vulnerability exists in KDE 4 & 5 that could allow attackers to execute code simply by tricking a user into downloading an archive, extracting it, and then opening the folder."
I would like to think that Linux users know better than " downloading some file from some site or somebody they don't know extracting it, and then opening the folder."
Lawrence Abrams - 5 years ago
I think most people have been trained that you have to run something to be infected and that simply opening a folder shouldn't infect you. Times have changed.
ssokolow - 5 years ago
Ooh. That's a nasty one.
Exploitable in anything that has KDE's icon-handling behaviour. (I managed to trigger it in KDE Open/Save dialogs too)
On the bright side, as long as you avoid invoking the Open/Save dialogs, Ark doesn't seem to be vulnerable and, as a user who prefers PCManFM to Dolphin, I can say that PCManFM-Qt doesn't seem to be vulnerable either.
(I got used to PCManFM when distros' over-eagerness to jump on KDE 4.x before it was ready drove me from KDE 3.5 to LXDE for a few years.)