
Roughly 1,450 pfSense instances exposed online are vulnerable to command injection and cross-site scripting flaws that, if chained, could enable attackers to perform remote code execution on the appliance.
pfSense is a popular open-source firewall and router software that allows extensive customization and deployment flexibility. It is a cost-effective solution that accommodates specific needs, offering a wide range of features typically found in expensive commercial products.
In mid-November, SonarSource’s researchers with the aid of their SonarCloud solution discovered three flaws impacting pfSense 2.7.0 and older and pfSense Plus 23.05.01 and older. The flaws are tracked as CVE-2023-42325 (XSS), CVE-2023-42327 (XSS), and CVE-2023-42326 (command injection).
Although the reflected XSS flaws require user action on the victim’s side to work, the command injection flaw is more severe (CVSS score: 8.8).
This vulnerability in pfSense’s web UI arises from shell commands being constructed from user-provided data for configuring network interfaces without applying proper validation.
The flaw impacts the "gifif" network interface parameter, which isn’t checked for safe values, allowing malicious actors to inject additional commands in the parameter, leading to their execution with root privileges.
For this exploit to work, the threat actor needs access to an account with interface editing permissions, hence the need to chain the flaws together for a powerful attack.
Either CVE-2023-42325 or CVE-2023-42327 can be used for executing malicious JavaScript in an authenticated user’s browser to gain control over their pfSense session.
Netgate, the vendor of pfSense, received reports about the three flaws on July 3, 2023, and released security updates that addressed them on November 6 (pfSense Plus 23.09) and November 16 (pfSense CE 2.7.1).
However, a month after patches have been made available by Netgate, nearly 1,500 pfSense instances remain vulnerable to attacks.
Shodan scan results SonarSource’s researchers shared with BleepingComputer show that out of the 1,569 internet-exposed pfSense instances, 42 use pfSense Plus 23.09, and another 77 run pfSense Community Edition 2.7.1.
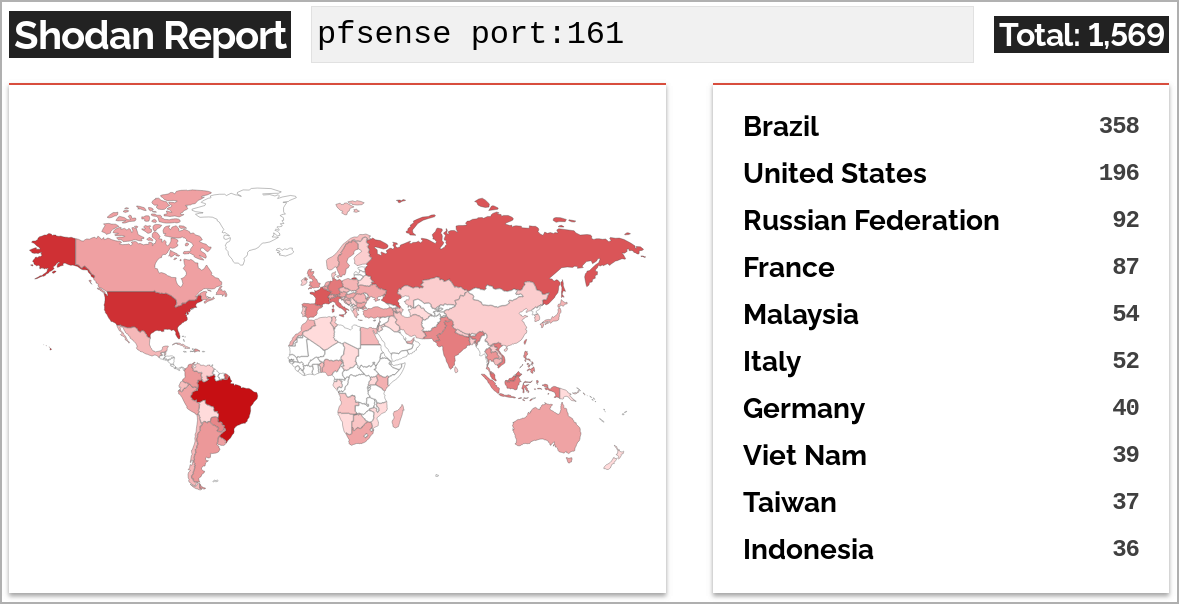
This leaves 1,450 instances (92.4%), which are directly discoverable through Shodan, vulnerable to the mentioned flaws.
While this exposure does not make these instances susceptible to immediate compromise, as threat actors would first need to target victims with XSS flaws, the exposure creates a significant attack surface.
While the number of vulnerable endpoints represents a small fraction of pfSense deployments globally, the fact that large enterprises often use the software makes this status particularly dangerous.
An attacker with access to pfSense operating with high-level privileges can easily cause data breaches, access sensitive internal resources, and move laterally within the compromised network.









Comments
Galactica-Actual - 11 months ago
From the Netgate forum:
This bug requires the user to be authenticated AND have access to the pages in question to exploit it, so just because some poor soul left their GUI open to the world doesn't mean they can be exploited directly unless they also happen to use weak credentials or give up access in some other way (e.g. XSS). [But we get that] "Authenticated command execution" doesn't get as many clicks/shares.
Netgate had this patched and available for pfSense+ and pfSense CE within two days. All security updates between releases are swept into the following release and further documented in the release notes.
I hope the 1,450 installs that were found by Shodan will reconfigure to stop publicly exposing their GUI, as well as upgrade to the latest release to receive all improvements or at least install the back-ported patches on their system.
Feel free to reach out next time for additional background info, so we can help keep everyone safe out there!
LeonStraathof - 11 months ago
The 1450 installs are not exposing their GUI but they expose SNMP on the public side which is also not recommended. So there was a bug that is only a problem if you configure something that you should not do in the first place and it is already fixed. I guess if people configure something that you should not do those are that same that never run fixes and updates. Netgate handled this very good, but they cannot protect ignorant administrators. Also to the OpenSense community this has no value to bash on Netgate, i like both products the same as they are very similar. The fact that mayor releases are less frequent for pfSense then OpenSense does not matter also because security and bugfixes are easily applied or reverted under "System -> Patches" in the GUI that is visible if the official package for this is added. And important patches are released as frequent as the fixed versions on OpenSense, only the methode how is different.