
In a confusing mess, a recent Microsoft Defender update rolled out a new security feature called 'Kernel-mode Hardware-enforced Stack Protection,' while removing the LSA protection feature. Unfortunately, Microsoft has not provided any documentation on this change, leading to more questions than answers.
Local Security Authority Protection, aka LSA Protection, is a security feature that protects sensitive information, like credentials, from being stolen by blocking untrusted code from being injected into the LSASS process and LSASS process memory dumping.
Windows users can enable LSA Protection in the Windows Security > Device Security > Core Isolation settings page for CPUs that support virtualization.
However, for the past few weeks, Windows 11 users have complained that they cannot enable the Local Security Authority Protection security feature in the Windows Security 'Core Isolation' settings.
When attempting to do so, Windows prompts users to restart the computer to enable the feature, but on reboot, it would not be enabled, and Windows would once again display a reboot prompt.
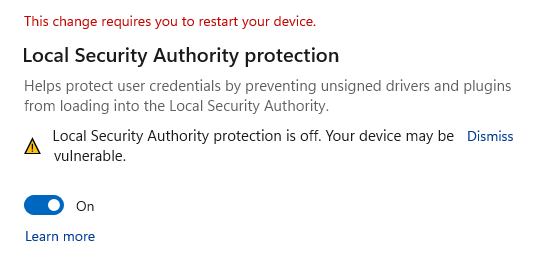
Microsoft later said that if you had enabled LSA Protection and restarted your device at least once, you could ignore these warnings.
A workaround was also provided to check if LSA Protection is enabled and how to configure two Registry keys to disable the warning.
Microsoft Defender update creates confusion
A recent Microsoft Defender update has made this feature even more confusing, as after it is installed, the LSA Protection feature is removed and replaced by a new feature called Kernel-mode Hardware-enforced Stack Protection.
Kernel-mode Hardware-enforced Stack Protection is a security feature that attempts to prevent ROP (Return Oriented Programming) based control flow attacks that could lead to code execution.
"For code running in kernel mode, the CPU confirms requested return addresses with a second copy of the address stored in the shadow stack to prevent attackers from substituting an address that runs malicious code instead," explains the Windows Kernel-mode Hardware-enforced Stack Protection setting.
"Note that not all drivers are compatible with this security feature."
However, to use this feature, a Windows device must be using Intel Tiger Lake CPUs or AMD Zen3 CPUs and later. Therefore, Windows will only display this new setting if the device has the required hardware.
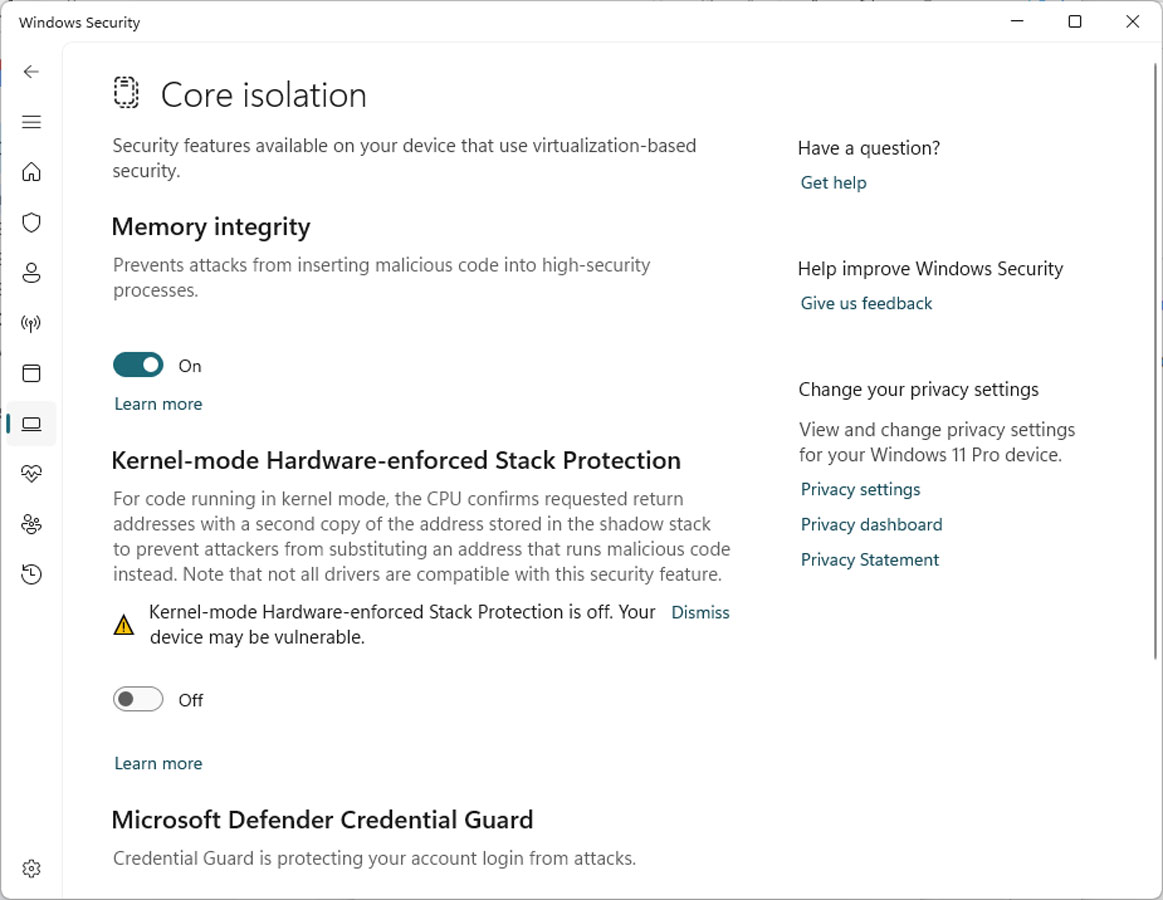
Like Memory Integrity, when enabling Kernel-mode Hardware-enforced Stack Protection, Windows will ensure that no incompatible drivers are loaded in Windows. If there are, the Stack Protection feature will not enable, and Windows will display a list of incompatible drivers.
Windows 11 users now report seeing Windows security notifications that the new feature is disabled due to conflicting drivers.
"Kernel-mode Hardware-enforced Stack Protection is off. Your device may be vulnerable," reads a warning in the Windows Security Center.
Source: BleepingComputer
However, when they examine the list, it is empty, making it confusing how to enable the feature.
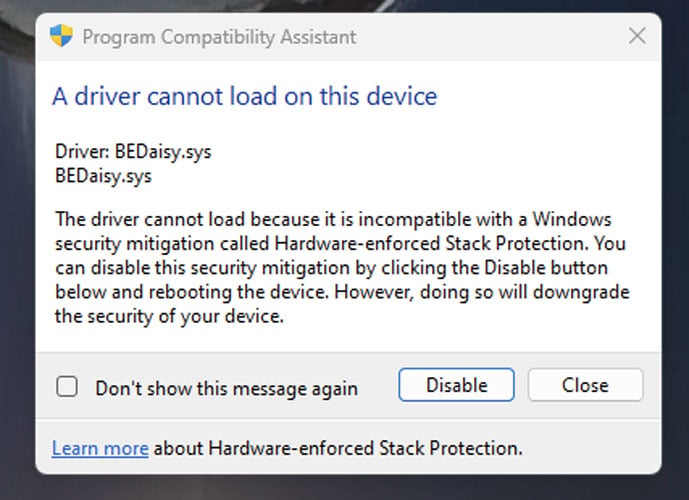
Even worse, some conflicting game anti-cheat drivers are not detected as incompatible, and Kernel-mode Hardware-enforced Stack Protection is still enabled. These conflicting drivers are causing Windows to crash or for games not to run when the security feature is enabled and a game is launched.
Windows 11 users have reported these problems for PUBG, Valorant (Riot Vanguard), Bloodhunt, Destiny 2, Genshin Impact, Phantasy Star Online 2 (Game Guard) and Dayz.
Source: Reddit
What happened to LSA Protection?
Even more frustrating is that Windows 11 users can no longer enable LSA Protection, which did not require newer CPUs, from the Windows Security settings.
It's not even clear if LSA protection is bundled into the Kernel-mode Hardware-enforced Stack Protection or has been removed from the Windows Setting interface entirely, requiring users to enable it manually via the Registry.
Furthermore, there has been no notice from Microsoft about the swapping of these security features or about Kernel-mode Hardware-enforced Stack Protection being added other than the brief description found in Windows Security and the scattered documentation [1, 2, 3] on the Stack Protection feature.
BleepingComputer asked Microsoft about the new Stack Protection feature if LSA Protection is now bundled within it, and the conflicts people are having.
This article will be updated with any responses we receive.









Comments
NoneRain - 1 year ago
Another good beta-testing of features on end users, I suppose.