
A criminal group has made at least $450,000 by infecting organizations with the Samas ransomware in the past year, according to an analysis by researchers from security firm Palo Alto Networks.
The Samas ransomware first came to light in March 2016, when the FBI issued an alert about a wave of ransomware infections that hit several US companies, mainly those working in the healthcare sector.
A few days later, researchers from the Microsoft Malware Protection Center were publishing the first report on this threat, which was also known by other names such as SamSam, Samsa, Kazi, or RDN/Ransom.
Samas isn't your run-of-the-mill ransomware
Microsoft revealed that Samas wasn't your regular spray-and-pray ransomware, and that the people behind weren't interested in mass infection campaigns.
Crooks were exploiting vulnerabilities in Java servers and weak RDP credentials to break into corporate networks and infect as many computers as possible, in many cases installing the ransomware by hand.
Attackers were targeting only companies, and asking large sums of money from each victim, knowing they could push for more money compared to a regular Locky or CryptoWall infection. The bigger the company and the more computers they infected, the more money they asked.
The success of Samas operations quickly spurred a wave of copycats, but Samas continued to remain a threat, with new infections each month, albeit not as frequent and common as those by ransomware families such as Locky or Cerber, which took the classic spam shotgun approach. For example, based on statistics from ID Ransomware, a service for identifying the type of ransomware has locked your computer, Samas infections rarely reached five detections per day, while Locky and Cerber were well in the hundreds.
Samas group made $450,000 in one year
According to a report released last Friday by Palo Alto, Samas was first saw about one year ago, at the start of December 2015, and slowly ramped up activity, as the group behind it were successful in their attacks.
The ransomware constantly evolved each month, as crooks adapted their tool for each of their targets.
For each attack, the crooks used a slightly different Samas version and often changed the Bitcoin address at which they requested ransom payments.
Researchers say they've kept track of all these addresses. In total, Palo Alto says they were able to identify transactions that totaled 607 Bitcoin across 19 different Bitcoin addresses.
Converted using today's Bitcoin-dollar exchange rate, the group behind Samas made around $450,000 since they've launched their operation.
This number can be even higher, according to researchers, who admitted they weren't able to get samples of all Samas versions.
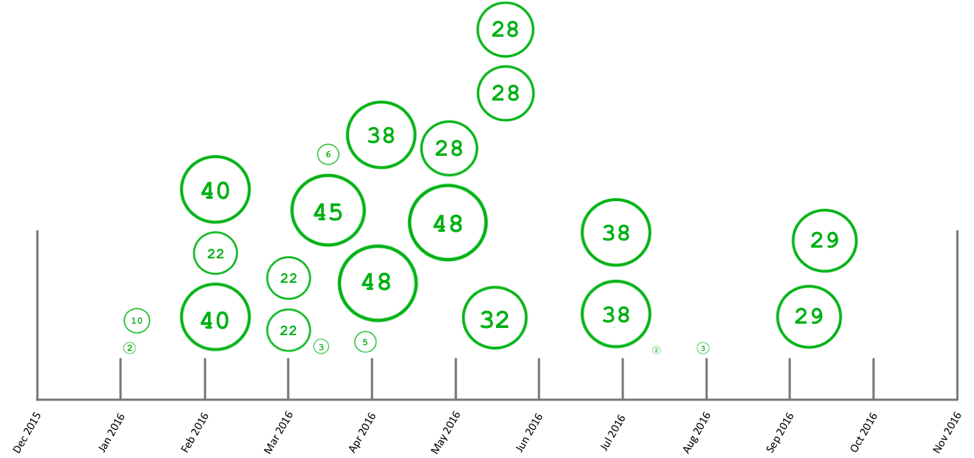
"As we can see, there is a large gap in between June and September of 2016," researchers say, referring to the graph above. "This is most likely due to the sample set used during research, as there were only a few samples obtained in recent months."
Despite going under the radar for most of the year, the Samas group earned quite a nice sum of money.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now