Cerber 5.0 has been spotted by security researcher Bryan Campbell being distributed via RIG-V exploit kits. These exploit kits allow the ransomware to be installed on a victim's computer without their knowledge when they browse to a compromised web site or possibly through malvertising. I am sure Cerber 5.0 is also being distributed via email campaigns, but at this time I do not have a sample of these emails.
Update 11/24/16 1:14PM EST: Marcelo Rivero has told me that Cerber 5.0.1 has already been spotted.
Once installed, Cerber 5.0 will encrypt the victim's data and then demand a ransom payment in bitcoins to decrypt the files.

According to Cerber security researcher BloodDolly, the main changes in version 5.0 are the following:
- The ransomware will now skip 640 bytes, compared to 512 bytes in previous versions, when encrypting a file.
- The minimum file size that Cerber will encrypt a file is now 2,560 bytes, compared to 1,024 bytes in previous versions. This means that any file that is smaller than 2,560 bytes will not be encrypted.
There were also some changes in the IP ranges used to send statistical UDP packets. These ranges are: 63.55.11.0/27, 15.93.12.0/27, 194.165.16.0/22.
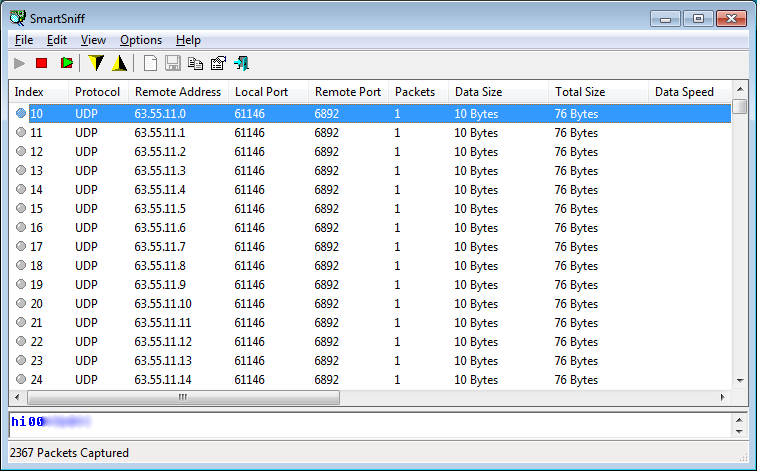
Network Communication:
63.55.11.0/27
15.93.12.0/27
194.165.16.0/22









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now