We are happy to report that the Fedor Sinitsyn, a senior malware analyst at Kaspersky Labs, has discovered a weakness in the Jaff ransomware and was able to release a decryptor for all variants that have been released to date. For those who were infected with the Jaff Ransomware and had their files encrypted with the .jaff, .wlu, or .sVn extensions, this decryptor can recover your files for free.
While using the decryptor, if you have any questions or need support in decrypting your files, please feel free to post in our dedicated Jaff Ransomware Help & Support Topic.
How to Decrypt Jaff (SVN, WLU, Jaff) Encrypted Files Using RakhniDecryptor
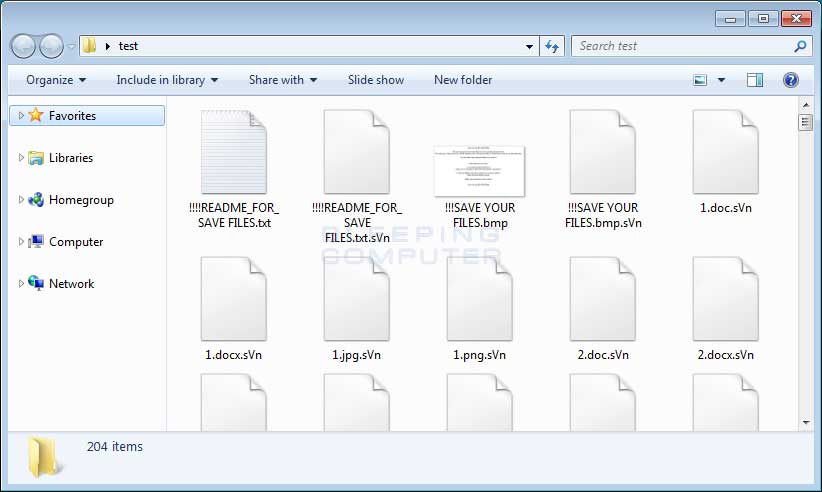
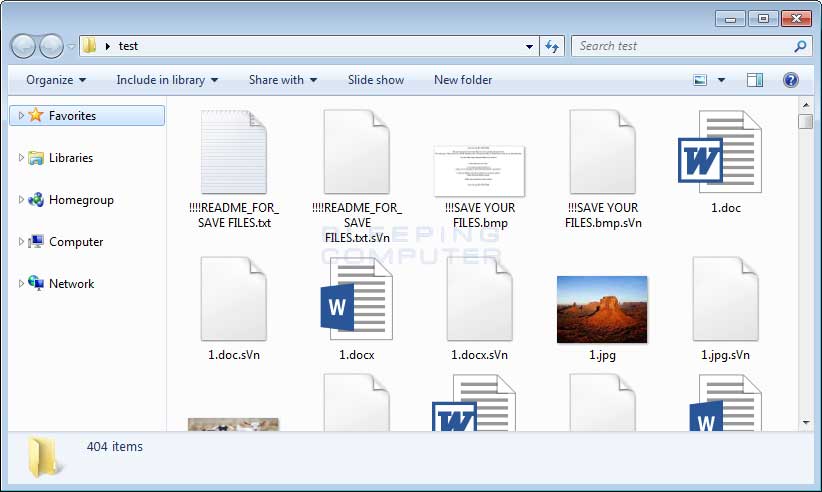
Victims of the Jaff ransomware can be identified by their files being encrypted and have either the .jaff, .wlu, or .sVn extension appended to the file name. For example, a file called test.jpg would be encrypted and renamed as test.jpg.jaff, test.jpg.wlu, or test.jpg.sVn. An example of a folder of files encrypted by the .sVn variant of Jaff can be seen below.
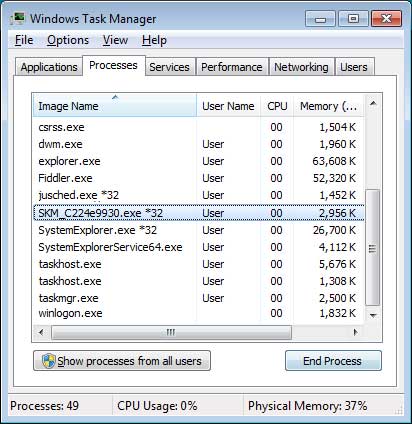
Before we can begin decrypting Jaff encrypted files, we first need to terminate the ransomware. To do this, open the Windows Task Manager by pressing the Ctrl+Alt+Delete keyboard combination on your keyboard to open the Windows security screen. Then select Task Manager.
Once Task Manager is open, look for a process that appears to have a random name. For example, one campaign of the .sVn variant was using file names such as SKM_C224e9930.exe. Once you determine the Jaff process that is running, you should terminate it by clicking on the End Process button while the process is highlighted. If you cannot identify a running process, please feel free to post an image of your task manager or a list of running processes and we can let you know which process to terminate. It may also be possible that there will be no Jaff process running.
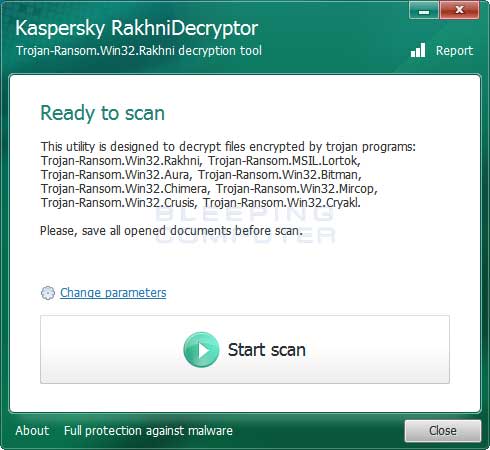
Now that Jaff is no longer running on the computer, we can begin to decrypt the encrypted files. First you need to download the RakhniDecryptor, extract the program, and then run it. Once running it will display the main screen as shown below.
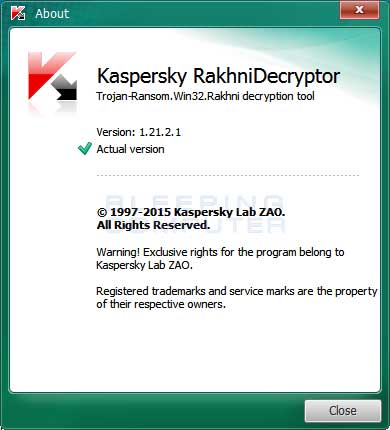
Before starting, you need to make sure that you are using version 1.21.2.1, which supports the Jaff ransomware. To check the version of the RakhniDecryptor you can click on the About link at the bottom left of the above screen. This will display a small window that shows the version of RakhniDecryptor.
If you are using version 1.21.2.1 or greater, then you should click on the Start scan button and RakhniDecryptor will prompt you to select an encrypted file. Browse to a folder that contains Jaff encrypted files and select a .Word, Excel, PDF, music, or image file.
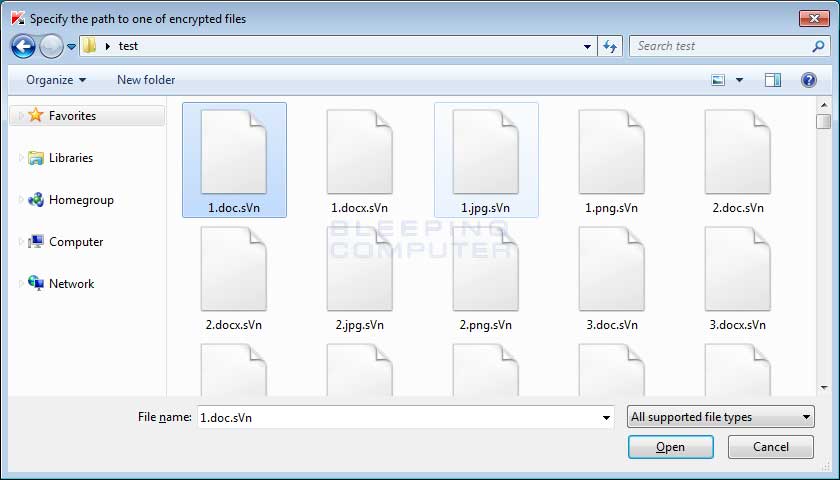
Once you have selected an encrypted file, RakhniDecryptor will prompt you to select a ransom note as well.
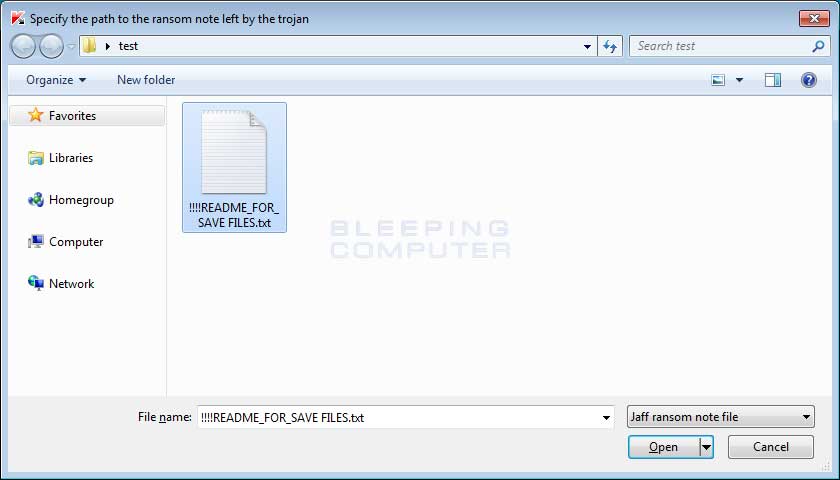
Once you have selected the ransom note, click on the Open button. RakhniDecryptor will now scan the entire computer for encrypted files and decrypt them.
This process can take quite a long time, so please be patient while it scans your computer and decrypts the files.
When it has finished, you will be at a completed screen as shown below.
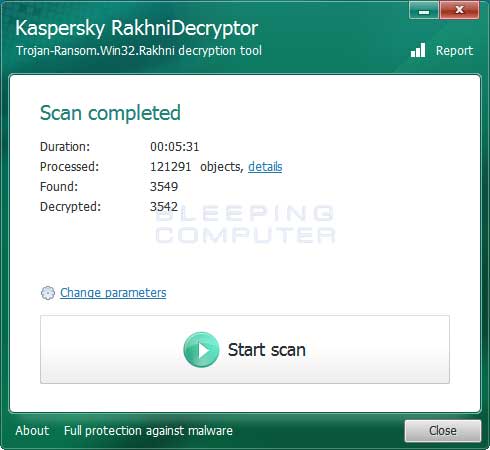
You can then click on the details link to see a full list of Jaff files decrypted by the decryptor.
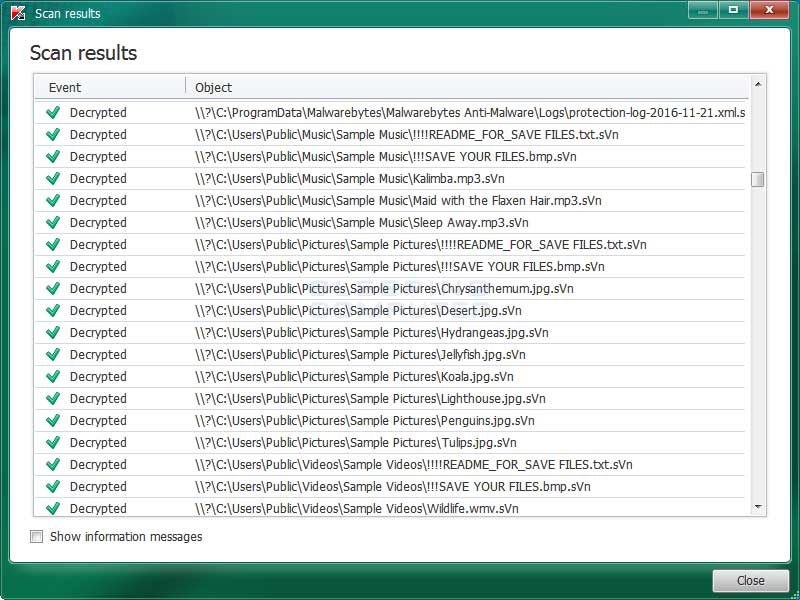
It should be noted that even though your files are now decrypted, the original encrypted files will be left behind.
Though your files are now decrypted, the original encrypted files will still be on your computer. Once you confirm that your files have been properly decrypted, you can use CryptoSearch to move all the encrypted files into one folder so you can delete or archive them.
Now that the files have been decrypted, you can close the RahkniDecryptor program.









Comments
Gsc2000 - 7 years ago
Looks like a great tool but when will they fix kaspersky security centre so it can speak to mobile endpoints on the right ip address. Scandalous that it gets tripped up so easily even when the agent reports in on a new IP. We live in a mobile world so Fix it Kaspersky.
vicky_baloch1 - 7 years ago
O my.... please someone Release decrypter of Cryptolocker .. my hands are now paining to typing and keep on searching for a single valid decrypter for my files
GT500 - 7 years ago
CryptoLocker? That came out in 2013, and hasn't been seen in-the-wild for years. Have you used ID Ransomware to check and see if it is a different ransomware?
https://id-ransomware.malwarehunterteam.com/
MikeF12 - 7 years ago
Is the malware removed by the decryptor scan?
Lawrence Abrams - 7 years ago
No. Need to do a scan with anti-malware/anti-virus software for that.
MikeF12 - 7 years ago
Thanks.
JosC - 7 years ago
Has anyone reported or heard of the RakhniDecryptor dencrypting some but not all Jaff encrypted files?