A ransomware called Cerber has been floating around for about a week, but we were not able to retrieve a sample until today. Thanks to @BiebsMalwareGuy and @MeegulWorth, samples were found and further analysis of the ransomware could be done. When infected, a victim's data files will be encrypted using AES encryption and will be told they need to pay a ransom of 1.24 bitcoins or ~500 USD to get their files back. Unfortunately, at this point there is no known way to decrypt a victim's encrypted files for free.
At this time we do not currently know how the Cerber ransomware is being distributed, but according to SenseCy, it is being offered as a service on a closed underground Russian forum. This means that it is probably a new Ransomware as a Service, or RaaS, where affiliates can join in order to distribute the ransomware, while the Cerber developers earn a commission from each ransom payment.
For anyone who is infected with this ransomware or wants to discuss the infection, we have a dedicated support topic here: CERBER Ransomware Support and Help Topic.
The Cerber Encryption Process
When first run, Cerber will check to see if the victim is from a particular country. If the computer appears to be from any of the following countries, it will terminate itself and not encrypt the computer.
Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan
In the past, if the victim is not from one of the above countries, Cerber will install itself in the %AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\ folder and name itself after a random Windows executable. For example, when we performed our analysis of the ransomware it named itself autochk.exe. It will then configure Windows to automatically boot into Safe Mode with Networking on the next reboot using the following command:
C:\Windows\System32\bcdedit.exe" /set {current} safeboot network
In the past, Cerber would configure itself itself to start automatically when you login to windows, execute as your screensaver when your computer is idle, and set a task to execute itself once every minute. In this phase, when the ransomware is executed it will show a fake system alert and begin a restart process. Until this restart is allowed to occur, it will continue to display fake system alerts. Examples of alerts you may see include:
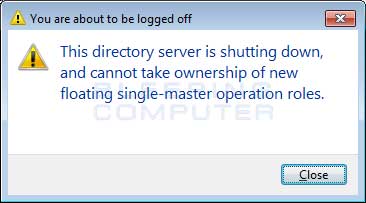 |
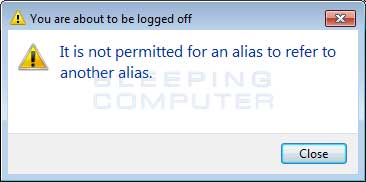 |
At this time, Cerber is no longer creating an autostart and cleans itself up afterwards leaving no executables behind.
Before Cerber encrypts any files it will also stop the following processes so that it can encrypt associated files:
msftesql.exe
sqlagent.exe
sqlbrowser.exe
sqlservr.exe
sqlwriter.exe
oracle.exe
ocssd.exe
dbsnmp.exe
synctime.exe
mydesktopqos.exe
agntsvc.exeisqlplussvc.exe
xfssvccon.exe
mydesktopservice.exe
ocautoupds.exe
agntsvc.exeagntsvc.exe
agntsvc.exeencsvc.exe
firefoxconfig.exe
tbirdconfig.exe
ocomm.exe
mysqld.exe
mysqld-nt.exe
mysqld-opt.exe
dbeng50.exe
sqbcoreservice.exe
Thanks to Hasherazade's analysis of the ransomware, it was discovered that Cerber uses a JSON configuration file for its settings when executed. This config file details what extensions to encrypt, what countries should not be encrypted, what files and folders to not encrypt, and various other configuration information.
When encrypting your data, Cerber will scan the victim's drive letters for any files that match certain file extensions. In the past, when Cerber found a matching data file, it would encrypt the file using AES-256 encryption, encrypt the file's name, and then add the .CERBER extension to it. Now it appends a random 4 digit extension. For example, the unencrypted file called test.doc may be renamed as kMWZJggq2p.a82d after it has been encrypted. The currently targeted file extensions are:
.accdb,.mdb,.mdf,.dbf,.vpd,.sdf,.sqlitedb,.sqlite3,.sqlite,.sql,.sdb,.doc,.docx,.odt,.xls,.xlsx,.ods,.ppt,.pptx,.odp,.pst,.dbx,.wab,.tbk,.pps,.ppsx,.pdf,.jpg,.tif,.pub,.one,.rtf,.csv,.docm,.xlsm,.pptm,.ppsm,.xlsb,.dot,.dotx,.dotm,.xlt,.xltx,.xltm,.pot,.potx,.potm,.xps,.wps,.xla,.xlam,.erbsql,.sqlite-shm,.sqlite-wal,.litesql,.ndf,.ost,.pab,.oab,.contact,.jnt,.mapimail,.msg,.prf,.rar,.txt,.xml,.zip,.1cd,.3ds,.3g2,.3gp,.7z,.7zip,.aoi,.asf,.asp,.aspx,.asx,.avi,.bak,.cer,.cfg,.class,.config,.css,.dds,.dwg,.dxf,.flf,.flv,.html,.idx,.js,.key,.kwm,.laccdb,.ldf,.lit,.m3u,.mbx,.md,.mid,.mlb,.mov,.mp3,.mp4,.mpg,.obj,.pages,.php,.psd,.pwm,.rm,.safe,.sav,.save,.srt,.swf,.thm,.vob,.wav,.wma,.wmv,.3dm,.aac,.ai,.arw,.c,.cdr,.cls,.cpi,.cpp,.cs,.db3,.drw,.dxb,.eps,.fla,.flac,.fxg,.java,.m,.m4v,.max,.pcd,.pct,.pl,.ppam,.ps,.pspimage,.r3d,.rw2,.sldm,.sldx,.svg,.tga,.xlm,.xlr,.xlw,.act,.adp,.al,.bkp,.blend,.cdf,.cdx,.cgm,.cr2,.crt,.dac,.dcr,.ddd,.design,.dtd,.fdb,.fff,.fpx,.h,.iif,.indd,.jpeg,.mos,.nd,.nsd,.nsf,.nsg,.nsh,.odc,.oil,.pas,.pat,.pef,.pfx,.ptx,.qbb,.qbm,.sas7bdat,.say,.st4,.st6,.stc,.sxc,.sxw,.tlg,.wad,.xlk,.aiff,.bin,.bmp,.cmt,.dat,.dit,.edb,.flvv,.gif,.groups,.hdd,.hpp,.m2ts,.m4p,.mkv,.mpeg,.nvram,.ogg,.pdb,.pif,.png,.qed,.qcow,.qcow2,.rvt,.st7,.stm,.vbox,.vdi,.vhd,.vhdx,.vmdk,.vmsd,.vmx,.vmxf,.3fr,.3pr,.ab4,.accde,.accdr,.accdt,.ach,.acr,.adb,.ads,.agdl,.ait,.apj,.asm,.awg,.back,.backup,.backupdb,.bank,.bay,.bdb,.bgt,.bik,.bpw,.cdr3,.cdr4,.cdr5,.cdr6,.cdrw,.ce1,.ce2,.cib,.craw,.crw,.csh,.csl,.db_journal,.dc2,.dcs,.ddoc,.ddrw,.der,.des,.dgc,.djvu,.dng,.drf,.dxg,.eml,.erf,.exf,.ffd,.fh,.fhd,.gray,.grey,.gry,.hbk,.ibank,.ibd,.ibz,.iiq,.incpas,.jpe,.kc2,.kdbx,.kdc,.kpdx,.lua,.mdc,.mef,.mfw,.mmw,.mny,.moneywell,.mrw,.myd,.ndd,.nef,.nk2,.nop,.nrw,.ns2,.ns3,.ns4,.nwb,.nx2,.nxl,.nyf,.odb,.odf,.odg,.odm,.orf,.otg,.oth,.otp,.ots,.ott,.p12,.p7b,.p7c,.pdd,.mts,.plus_muhd,.plc,.psafe3,.py,.qba,.qbr,.qbw,.qbx,.qby,.raf,.rat,.raw,.rdb,.rwl,.rwz,.s3db,.sd0,.sda,.sr2,.srf,.srw,.st5,.st8,.std,.sti,.stw,.stx,.sxd,.sxg,.sxi,.sxm,.tex,.wallet,.wb2,.wpd,.x11,.x3f,.xis,.ycbcra,.yuv,.mab,.json,.msf,.jar,.cdb,.srb,.abd,.qtb,.cfn,.info,.info_,.flb,.def,.atb,.tbn,.tbb,.tlx,.pml,.pmo,.pnx,.pnc,.pmi,.pmm,.lck,.pm!,.pmr,.usr,.pnd,.pmj,.pm,.lock,.srs,.pbf,.omg,.wmf,.sh,.war,.ascx,.k2p,.apk,.asset,.bsa,.d3dbsp,.das,.forge,.iwi,.lbf,.litemod,.ltx,.m4a,.re4,.slm,.tiff,.upk,.xxx,.money,.cash,.private,.cry,.vsd,.tax,.gbr,.dgn,.stl,.gho,.ma,.acc,.db
When searching for files to encrypt, Cerber will skip files that are named bootsect.bak, iconcache.db, thumbs.db, ntuser.dat, or wallet.dat and file names whose path contains the following strings:
:\$recycle.bin\
:\$windows.~bt\
:\boot\
:\documents and settings\all users\
:\documents and settings\default user\
:\documents and settings\localservice\
:\documents and settings\networkservice\
:\program files\
:\program files (x86)\
:\programdata\
:\recovery\
:\recycler\
:\users\all users\
:\windows\
:\windows.old\
\appdata\local\
\appdata\locallow\
\appdata\roaming\adobe\flash player\
\appData\roaming\apple computer\safari\
\appdata\roaming\ati\
\appdata\roaming\intel\
\appdata\roaming\intel corporation\
\appdata\roaming\google\
\appdata\roaming\macromedia\flash player\
\appdata\roaming\mozilla\
\appdata\roaming\nvidia\
\appdata\roaming\opera\
\appdata\roaming\opera software\
\appdata\roaming\microsoft\internet explorer\
\appdata\roaming\microsoft\windows\
\application data\microsoft\
\local settings\
\public\music\sample music\
\public\pictures\sample pictures\
\public\videos\sample videos\
\tor browser\
Furthermore, Cerber contains the ability to scan for and enumerate unmapped Windows shares and encrypt any data that is found on them. If the network setting is set to 1 in the configuration file, then Cerber will search for and encrypt any accessible network shares on your network, even if those shares are not mapped to the computer.
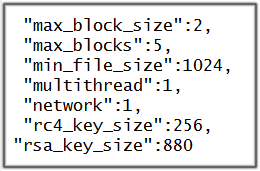
At this time, though this feature appears to be turned off in the configuration file, It is important for all system administrators to harden the security of their network shares as this feature is starting to become common in newer ransomware.
Last, but not least, Cerber will create 3 ransom notes on your desktop as well as in every folder that is encrypted. These files are called # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt, and # DECRYPT MY FILES #.vbs.
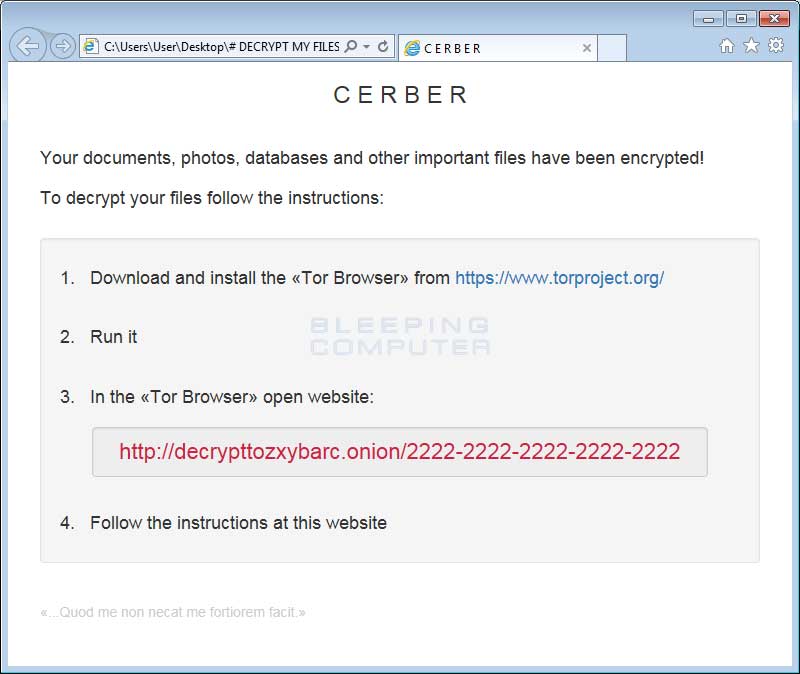
Newer versions are leaving a Readme.hta note instead, which opens a small window that looks like the following:
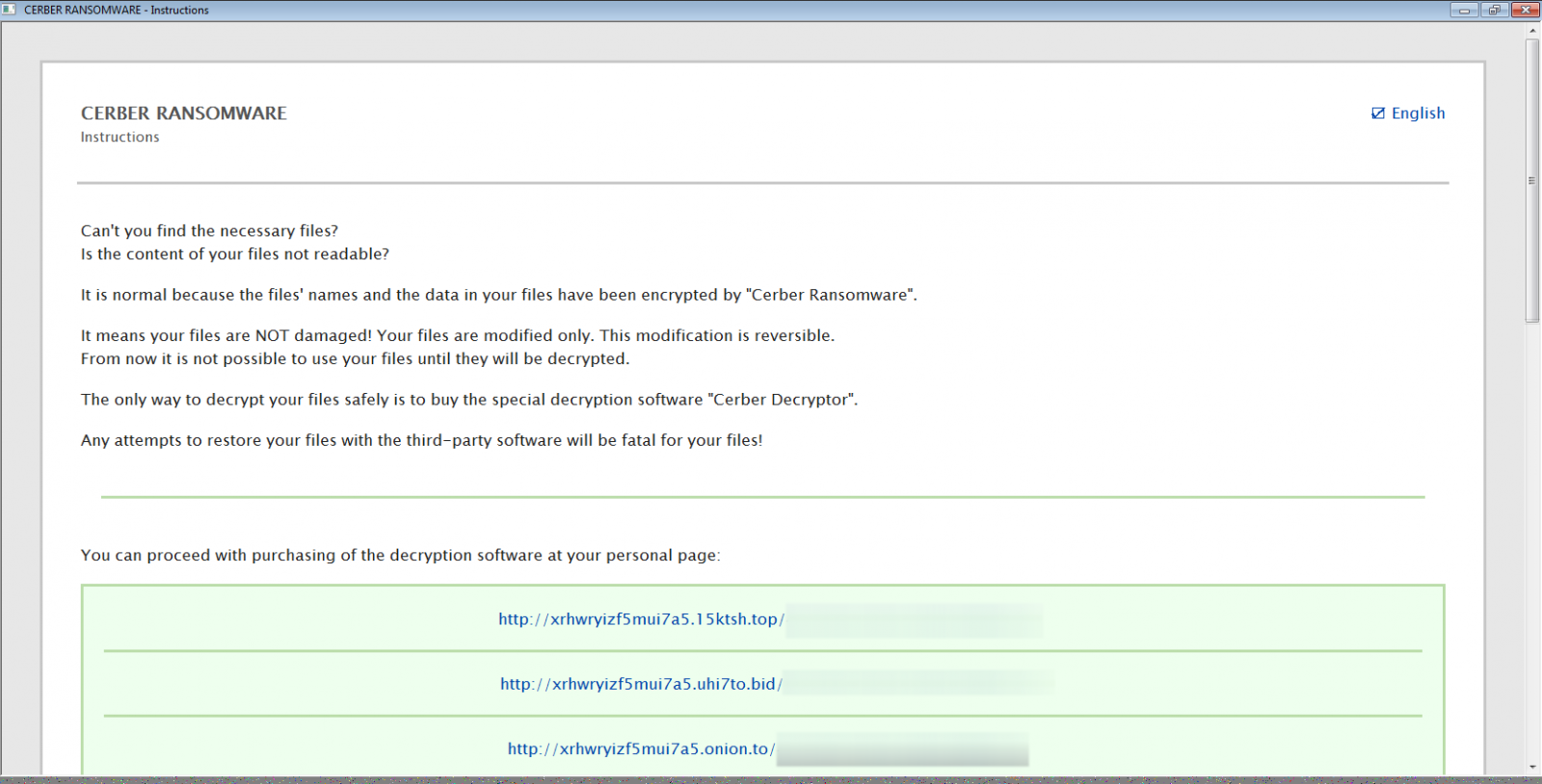
These ransom notes contain instructions on what has happened to your data and contain links to the Tor decryption service where you can make the ransom payment and retrieve the decryptor.
Older notes, used to contain the Latin quote:
.Quod me non necat me fortiorem facit
- Cerber Ransom Note
In English, this translates to "That which does not kill me makes me stronger", which I am sure all of the victims appreciate.
Last, but not least, Cerber will delete the victim's Shadow Volume Copies using the command:
C:\Windows\System32\wbem\WMIC.exe shadowcopy delete
To upset a victim even more, Cerber talks to you!
Once of the ransom notes that Cerber creates is a bit more "special" then the others. The # DECRYPT MY FILES #.vbs file contains VBScript, which will cause the victim's computer to speak to them.
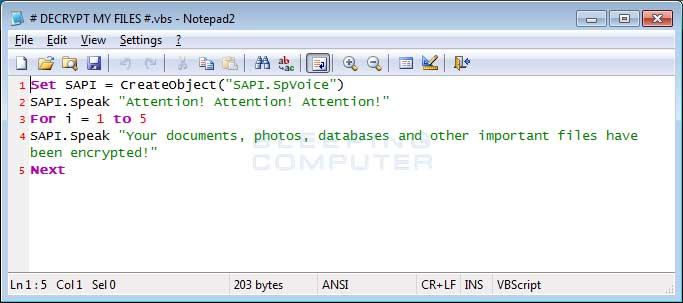
When the above script is executed, your computer will speak a message stating that your computer's files were encrypted and will repeat itself numerous times. This message can be listened to below:
The Cerber Decryptor
In the ransom notes is a link to the decrypttozxybarc.onion Tor site, which acts as the payment and decryption service. This site is named Cerber Decryptor and can be accessed in 12 different languages.
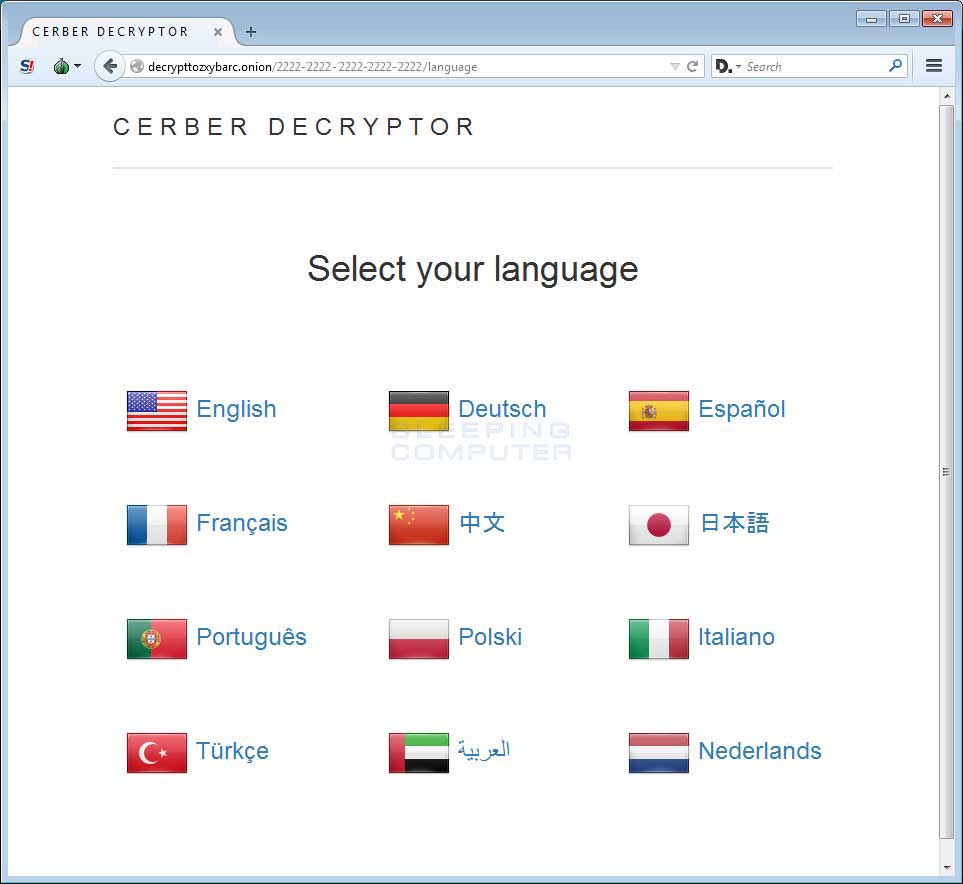
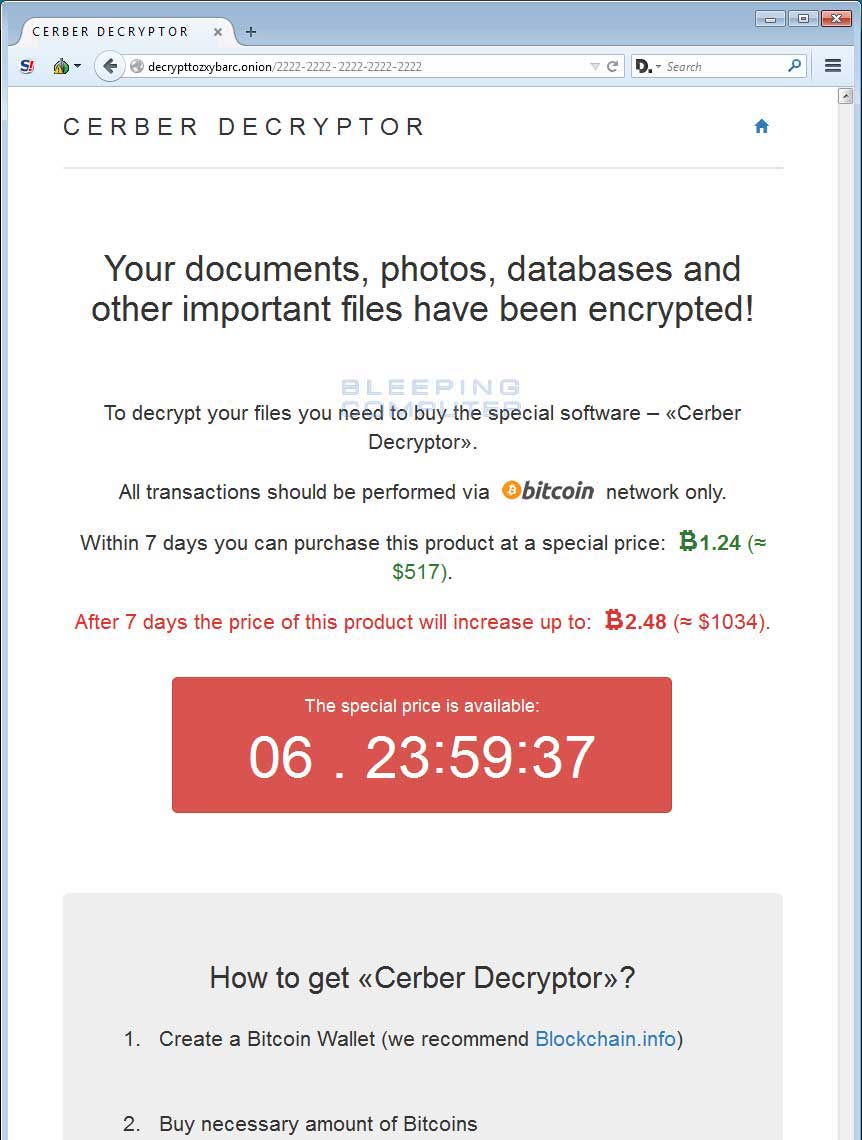
Once you select the language, you will be prompted to enter a captcha, and then you will finally be greeted with the main Cerber Decryptor page. This page will provide information on how to pay the ransom, the ransom amount, and that the ransom will double if not paid within 7 days.
|
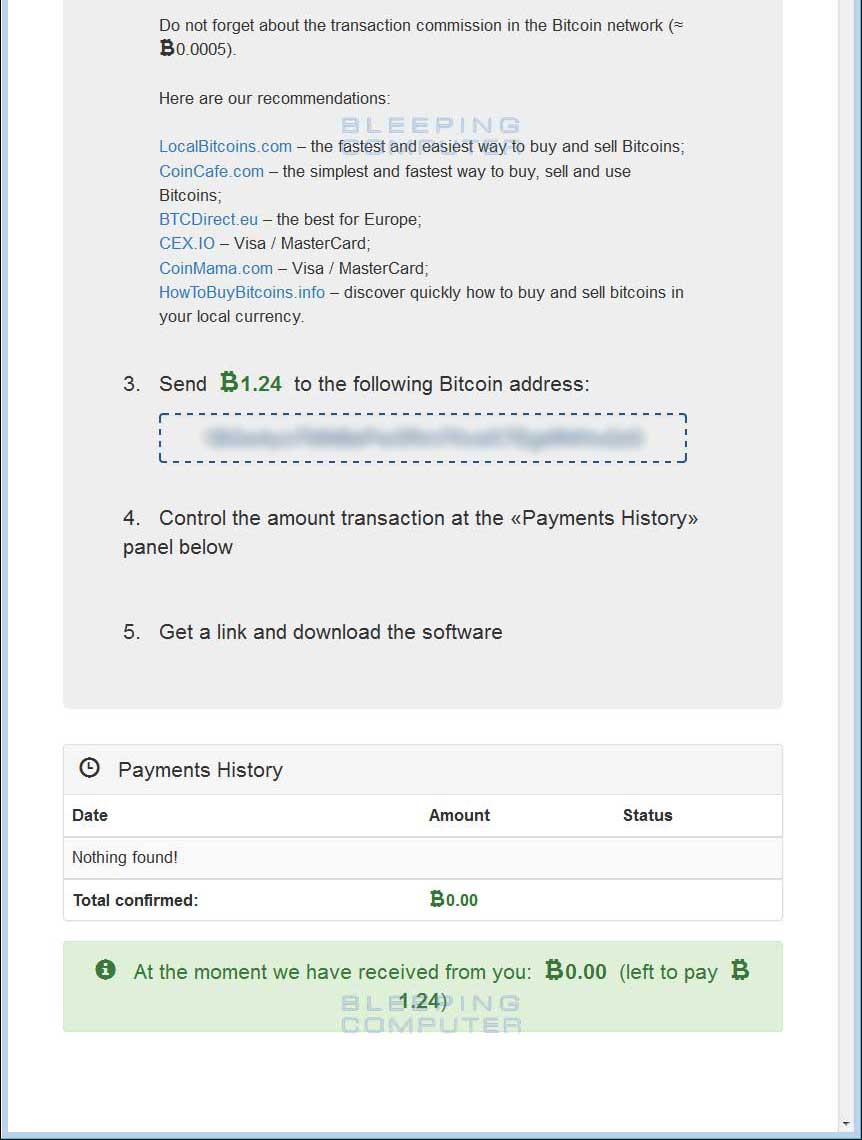
|
A complete image of the Cerber Decryptor page can be found here.
Once a victim makes a payment to the listed bitcoin address, their payment will be shown in the Payment History section of the decryptor page. After a certain amount of bitcoin transaction confirmations, this page will then provide a download link for the victim's unique decryptor.
As already said, unfortunately there is no way to decrypt your files for free. If you are a victim of this ransomware then your best option is to restore your files from a backup. For anyone who is infected with this ransomware or wants to discuss the infection, we have a dedicated support topic here: CERBER Ransomware Support and Help Topic.
How can you Protect Yourself from Ransomware?
If you were infected by Cerber, I can only say that I know what you are going through is terrible. I have helped enough people with ransomware over the past 5 years to know that its a horrible and violating experience and not one I wish on anyone.
For anyone who was infected with the Cerber Ransomware or is concerned about future infections, I highly recommend Emsisoft Anti-Malware for their behavior blocker component. Not only do you get a great security program, but their behavior blocker has an incredible track record at preventing new zero-day ransomware from encrypting a computer.
This is what happened when I tried running the Cerber installer with Emsisoft Anti-Malware's Behavior Blocker enabled.
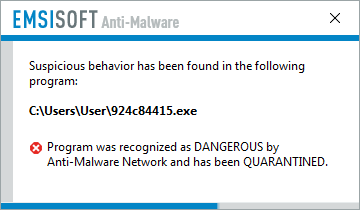
Unfortunately, the behavior blocker is only available in the paid for version, so you would need to purchase Emsisoft Anti-malware in order to benefit from this feature.
In full disclosure, we do earn a commission if you purchase Emsisoft Anti-Malware through the above link. With that said, I am only recommending Emsisoft Anti-malware because I believe in the program and that it can do a terrific job protecting you from Ransomware and other malware.
Files associated with Cerber Ransomware
HKCU\Control Panel\Desktop\SCRNSAVE.EXE "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Command Processor\AutoRun "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\[random] "%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"
Registry entries associated with Cerber Ransomware
"%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe"









Comments
ScathEnfys - 8 years ago
That ransom note script is certain to make anyone jump... what would be more unnerving is if it disabled mute too.
peterracine - 8 years ago
I can not stand these a-holes that are potentially from a country somewhere in eastern Europe that pumps out new versions of ransomware every day. I appreciate the efforts of everyone including bleeping computer, Emisoft, and Malwarebytes (I am sure there are others I missed) for developing code that helps to prevent these new threats. There is nothing worse than telling a customer that all there data is gone unless a price is paid. Does anyone know where this variant came from? It seems like old Russian satellites are producing a lot of this type of ransomware.
dimo70 - 8 years ago
Is there any way to decrypt files with .cerber extensions
Lawrence Abrams - 8 years ago
Not at this time unfortunately.
000O0000O000000 - 8 years ago
There is now: https://cerberdecrypt.com
IamDevin - 8 years ago
Not anymore I'm afraid. :-(
crisis2k - 8 years ago
Grinler, Locky & Cerber does not providing sample decrypting anymore?
Gmer99 - 8 years ago
I got an attempt of malware injection with Trojan Ransom Cerber coming from proxy server xoomer.virgilio.it but is problem with exact lcation it shows is in Virginia USA https://www.abuseipdb.com/check/174.129.145.134... also i got a scam attempt in the past days from the same area ... no luck to be hacked by morons out there , IP Void reports the site as malicious and exploit malware so i should make some phone calls to shut down those bastards
AlwaysCurious - 8 years ago
Have you tested if the anti rensomware programs, Malwarebytes Beta for instance, is effective against this?
Lawrence Abrams - 8 years ago
I personally have not.
Elewis - 8 years ago
In working on some clients machines with this ransomware, the free application Recuva has been able to recover a large amount of files lost. Not sure if anyone else has found a good method other then this but it's worked for me so far.
Sapphirewind - 8 years ago
I was able to as well but I still can't get the files to open even after renaming the extension. What to do now?
PiscesMike - 8 years ago
You haven't 'recovered' your files, all you've done is restored the original file names. The file data itself is still encrypted and will not be usable.
vanessa81 - 8 years ago
Hi, I just got infected with ransomware. This is a new computer so I don't mind loosing the very few files that I have. I have several questions?
1. Why it doesn't allow me to open Microsoft outlook anymore? It says " cannot open Microsoft outlook" "The set of folders cannot be opened"
2. If I were to re-install Windows and restore to factory settings, would this solve the problem?
3. Can they encrypt future documents?
It is also important to let users know that they are also using craigslist to infect your computer. I am a business owner who put out an add for employment, I constantly get resumes over my email for applications for employment. That is how I got infected, I had an "applicant" sending me his resume and saying he was interested in the position, but it was the ransomeware instead.
I look forward to reading your reply, thank you for your help!
• Edit•Share ›
nintendo1889 - 8 years ago
Try to open your office cd or dvd (or download your office setup at http://www.office.com/setup
run setup and choose "Repair". If you don't get a repair option, you've downloaded the wrong version of your office.
To avoid getting viruses via .doc files, I personally upload them to drive.google.com and view them there, safely.
A factory restore would fix it. All programs like this usually only run once and then delete themselves, they do not work in the future.
jdewey5676 - 8 years ago
I would like to add the ransomware came from a resume through craigslist. We have actually gotten quite a few but this was the first one that got opened and enabled editing/macros. They come as an attachment "RandomLettersRandomNumbers .docx". Hope this helps. Also this one did affect non-mapped shares but stopped after a couple servers were hit. So far only 3 servers out of 40. It appears to attack them alphabetically by server name. I am currently fighting it and looks like restoring from backup is the only option again. For server 2003 users it can also get the "Programs" folder if it is shared. It does work off of the users credentials so If you catch it early I am assuming you can stop it by disabling the users account. I was to late to know but did disable it for now just in case.
Dennismk - 8 years ago
Hello BleepingComputer.
I've had the Cerber Ransomware for a while now and I have tried some stuff to recover my files. All the important ones that mattered to me couldn't be recovered.
So my question is if I were to transfer the still crypted files over to another computer will that in turn lead to the new computer getting infected and have the Cerber ransomware take its course yet again and crypting all its files? I would like to save the crypted files for the future when there hopefully will be a decrypting tool for Cerber ransomware and that way I could recover my files and other stuff in the future.
Thank you for your time, I hope you understood me clearly.
Lawrence Abrams - 8 years ago
No, encrypted files being transferred to another computer wont do anything to that computer. Only running an executable on the other computer could cause an issue.
Dennismk - 8 years ago
And what would count as a executable? Is it anything of the type .html, .txt, .vbs, the internet shortcut or files of the type CERBER?
(sorry if this is a stupid question I'm not so familiar with viruses.)
I appreciate you taking the time to answer, I'm very grateful for that.
sysadm - 8 years ago
.html = not executable
.vbs = executable
.txt = not executable
shortcuts = can be executable
If you have been hit with ransomware and you do not have any backups, your only option is to pay the ransom and hope for the best. Let this be a lesson to you to ALWAYS MAKE A BACKUP OF IMPORTANT DATA TO AN EXTERNAL SOURCE. If you had your data backed up, you could simply reinstall your operating system and restore the data to your computer. But what good is doing that if you may run into this or another ransomware again, right?
The easiest way for you to avoid future ransomware lockout is to run a Linux-based operating system. Ransomware and viruses are written to affect the most amount of computers possible, and since more than 90% of all computers connected to the internet run Windows, that means Windows is the main target for malware authors.
Now is the time for you to try Linux. You don't have to be a computer expert to use Linux. For beginners, I recommend trying out a very user-friendly distribution like Fedora or Ubuntu. I recommend Fedora. Getting started is as simple as downloading the Fedora .ISO file, burning it to a CD or DVD, and restarting your computer. Not too difficult, right? Make sure all important data is backed up before you install your Linux operating system as the installation process will overwrite all data on your hard drive. Linux comes with built-in security features like hard drive encryption, and uses much better security defaults compared to Windows. If you'd like help getting your Linux installation up and running, feel free to reply here and I will help you out.
Take care
zr786 - 8 years ago
I have installed dropbox into my computer too. Now all the files in dropbox folder got also encrypted. My question is that will the cerber ransomware can effect my other PC where i have also installed dropbox. Infact i check the dropbox folder on my other pc and i see that my files are encrypted in dropbox but others are still normal.
To be on safe side, i have uninstalled dropbox from my other PC but i am afraid that i can also got attack on this pc too. I have installed Spyhunter too in order to increase security.
What is your opinion on it?
Thanks
Lawrence Abrams - 8 years ago
If both PCs synch to the same folders, then an infected one will affect both unfortunately. You do not have to remove dropbox, just make sure it does not have a driver letter associated with it.
AlexLutor - 8 years ago
Also, remember that Dropbox may be a security layer since it keeps a few versions of your files in their servers. I was able to recover all the infected files using Dropbox's website to revert to earlier versions.
Chubby-Ninja - 8 years ago
I've always used http://www.shadowexplorer.com/ to restore files never failed me yet. Also works on Win10
Mr.Tom - 8 years ago
Doesn't help when the ransomware also deletes your shadow copies too.
MgdElislam - 8 years ago
Could you please, Give us the "download link for the victim's unique decryptor" or the file you download, and is it was .exe or .vps or what ?
Thank you
sunshineiam - 8 years ago
so can this be removed or not. I do not care about my files, though its very devastating. I just want my computer and privacy back. I want to ask this question: Does this ransomeware track when you try to search the internet for removal methods?
IgorGanapolsky - 8 years ago
So the question is, how to protect yourself against Cerber ransomware? I mean, even if McAffee antivirus is running on your machine, this virus can still install itself. Any suggestions?
Iulian6 - 8 years ago
So a year has passed and no one did a decrypter for files affected by Cerber Ransome ! Why there is no interest, in knowing that many computers were affected worldwide ?! or we can conclude that the hackers who created Ransome Cerberus are more intelligent as IT specialists, and these are not able to make a program to restore the affected files.
Lawrence Abrams - 8 years ago
Unfortunately, not all encryption algorithms used by ransomware have weaknesses that can be exploited.
Iulian6 - 8 years ago
Let's be serious ! and not invoke on other reasons !
So who created Cerber Ransom, CAN decrypt affected files,
and IT specialists CAN NOT !!!
No only that passed one year by when he appeared, but this Cerber Ransom
infect computers in present ! around the world...and the autorities,what i do ?!
LordWoodman - 8 years ago
Sorry to disturb you, but I need your help.
My dad PC got infected with Cerber. It's an old pc, we were going to trash it.
But there is a problem: before I noticed the Cerber, I connected my usb HDD to take some old data. It stayed connected only for I few seconds before I noticed the problem and remove it from the pc.
Is my usb HDD infected now? Can I use it safely, or should I trash it?
Thank you for your help, and please excuse my poor englis, after all I am Italian.
lwlopez1 - 8 years ago
Virusproof. cryptos are very easy to stop. miletx.com. Houston only. in-person only.
Tips for the day. VBA shutdown. Next.
if exist "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" goto vbe664
goto aftervbe664
:vbe664
md "%systemroot%\backup\Program Files (x86)"
md "%systemroot%\backup\Program Files (x86)\Common Files"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\"
copy /Y "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL"
copy /Y "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL.XXX"
if exist "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL.XXX" goto vbe664success
cls
echo .
echo .
echo not enough permissions to copy "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL"
pause
:vbe664success
pause
del "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL"
:aftervbe664
if exist "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL" goto vbe6I64
goto aftervbe6I64
:vbe6I64
md "%systemroot%\backup\Program Files (x86)"
md "%systemroot%\backup\Program Files (x86)\Common Files"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6"
md "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\"
copy /Y "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL" "%systemroot%\backup\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL"
copy /Y "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL" "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL.XXX"
if exist "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL.XXX" goto vbe6I64success
cls
echo .
echo .
echo not enough permissions to copy "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL"
pause
:vbe6I64success
pause
del "C:\Program Files (x86)\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL"
:aftervbe6I64
if exist "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" goto vbe632
goto aftervbe632
:vbe632
md "%systemroot%\backup\Program Files"
md "%systemroot%\backup\Program Files\Common Files"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA\VBA6\"
copy /Y "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL"
copy /Y "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL.XXX"
copy /Y "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL" "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL.XXX"
if exist "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL.XXX" goto vbe632success
cls
echo .
echo .
echo not enough permissions to copy "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL"
pause
:vbe632success
pause
del "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\VBE6.DLL"
:aftervbe632
if exist "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL" goto vbe6I32
goto aftervbe6I32
:vbe6I32
md "%systemroot%\backup\Program Files"
md "%systemroot%\backup\Program Files\Common Files"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA\VBA6"
md "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\"
copy /Y "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL" "%systemroot%\backup\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL"
copy /Y "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL" "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL.XXX"
if exist "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL.XXX" goto vbe6I32success
cls
echo .
echo .
echo not enough permissions to copy "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL"
pause
:vbe6I32success
pause
del "C:\Program Files\Common Files\microsoft shared\VBA\VBA6\1033\VBE6INTL.DLL"
:aftervbe6I32
cyanohydrax
cascadeit - 8 years ago
Just an fyi, I had a computer that was infected. If i right clicked on a folder to restore previous versions, none showed. However, when I did this with a network computer (domain controller) i was able to select previous version and restored all of my files from a the remote server. It could not be done locally however, not sure why. This was with the version 3 variant.
Lawrence Abrams - 8 years ago
This is because the shadow volume copies are only deleted from the system that was infected. Good point, though, to let people know about.
miranduran - 8 years ago
Hi sorry, but what does that mean exactly? I'm assuming I probably don't have a network computer, but just in case there's the slightest glimmer of hope... I'm a student and I stupidly kept putting off backing up my files. Also I would half consider paying, but I REALLY REALLY don't have that kind of money. This is just so frustrating! Now this just really sucks because I lost a lot of work and I'm so mad at myself. 10 mins could've spared me so much grief right now. But sorry, this isn't about my sob story, just curious, can you please explain what cascadeit meant?
Thank you
Lawrence Abrams - 8 years ago
It means that sometimes the Shadow Volume Copies are not deleted, so you can use them to recover them. See here:
https://www.bleepingcomputer.com/tutorials/how-to-recover-files-and-folders-using-shadow-volume-copies/
tsandco - 8 years ago
Why can't windows disable encryption for Windows?
Can you be reinfected during the payment process?
Lawrence Abrams - 8 years ago
Windows uses the CryptoAPI library for many different functions, so it's not possible to disable. Even if Windows disabled their internal Crypto library, malware devs would just use other open source libraries.
As for the payment, I have never heard of anyone getting reinfected when paying.
SYNERGY-USA-LLC - 8 years ago
Out of necessity to cover our own needs and protect our clients we created an application called RansomSaver, it is an Outlook add-in and basically what it does is moves new incoming infected email to a folder under the deleted items called RansomSaver. We provide this software for free and with no strings attached.
To download or see further information regarding RansomSaver please visit http://synergy-usa-llc.com/ransomsaver-overview.html