A new version of the Locky Ransomware was released yesterday that uses a new naming scheme for encrypted files. Previously Locky had renamed files and then appended a Locky extension so that filename was similar to A65091F1B14A911F0DD0E81ED3029F08.locky.
With this new version, Locky uses the .zepto extension and files are renamed to a name like 024BCD33-41D1-ACD3-3EEA-84083E322DFA.zepto.
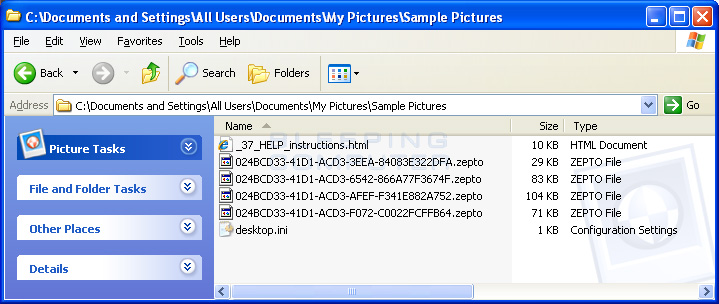
This new naming format is in the form of [first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[4_hexadecimal_chars]-[12_hexadecimal_chars].zepto. For example, for a file called 024BCD33-41D1-ACD3-3EEA-84083E322DFA.zepto, the extracted victim ID would be 024BCD3341D1ACD3.
If there are any other modifications to this version we will update this article.









Comments
alphapune - 8 years ago
Any solution to decrypt?
Lawrence Abrams - 8 years ago
Nothing on locky yet unfortunately.
walterman90 - 8 years ago
any solution to decrypt?
xadam91 - 8 years ago
any solution to decrypt?
lukelukex2 - 7 years ago
Still no way to decrypt the .zepto files?
Lawrence Abrams - 7 years ago
Unfortunately not.