
You rarely root for a cybercriminal, but a new malware campaign targeting child exploiters doesn't make you feel bad for the victims.
Since 2012, threat actors have been creating a variety of malware and ransomware that pretend to be government agencies warning infected Windows users that they were viewing CSAM. The malware tells victims they must pay a "penalty" to prevent their information from being sent to law enforcement.
One of the first "modern" ransomware operations, called Anti-Child Porn Spam Protection or ACCDFISA, used this extortion tactic combined with initially locking Windows desktops and encrypting files in later versions.
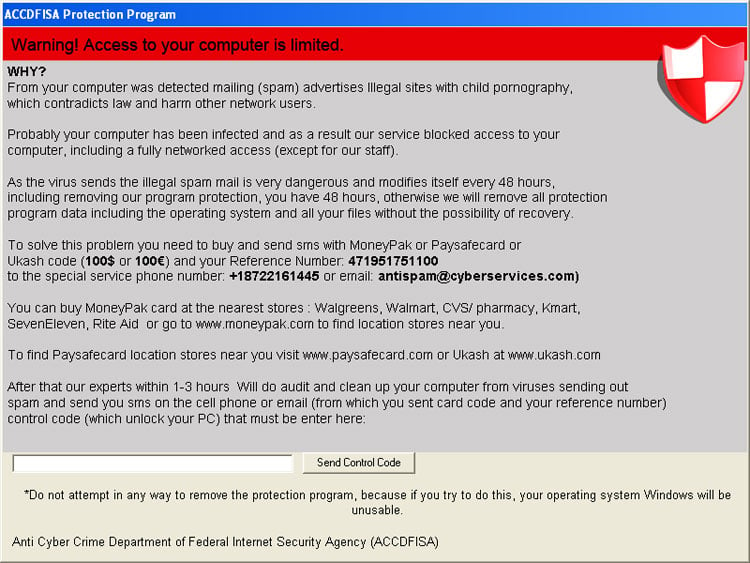
Source: BleepingComputer
Soon followed other malware families that pretended to be law enforcement issuing fines for watching CSAM, such as Harasom, Urausy, and the Reveton trojans.
An unlikely hero
Last week, cybersecurity researcher MalwareHunterTeam shared a sample of a malware executable with BleepingComputer called 'CryptVPN' [VirusTotal] using similar extortion tactics.
However, this time, rather than targeting innocent people, the malware developer is targeting those who actively seek out child pornography.
After researching the malware, BleepingComputer found that threat actors created a website to impersonate UsenetClub, a subscription service for "uncensored" access to images and videos downloaded from Usenet.
Usenet is an online discussion platform allowing people to discuss various topics in "newsgroups" to which they subscribe. While Usenet is used for valid discussion on a wide range of issues, it is also a known source of child pornography.
A fake site created by the threat actors pretends to be UsenetClub, offering three subscription tiers to the site's content. The first two are paid-for subscriptions ranging from $69.99 per month to $279.99 per year.
However, a third option claims to provide free access after you install a free "CryptVPN" software and use it to access the site.
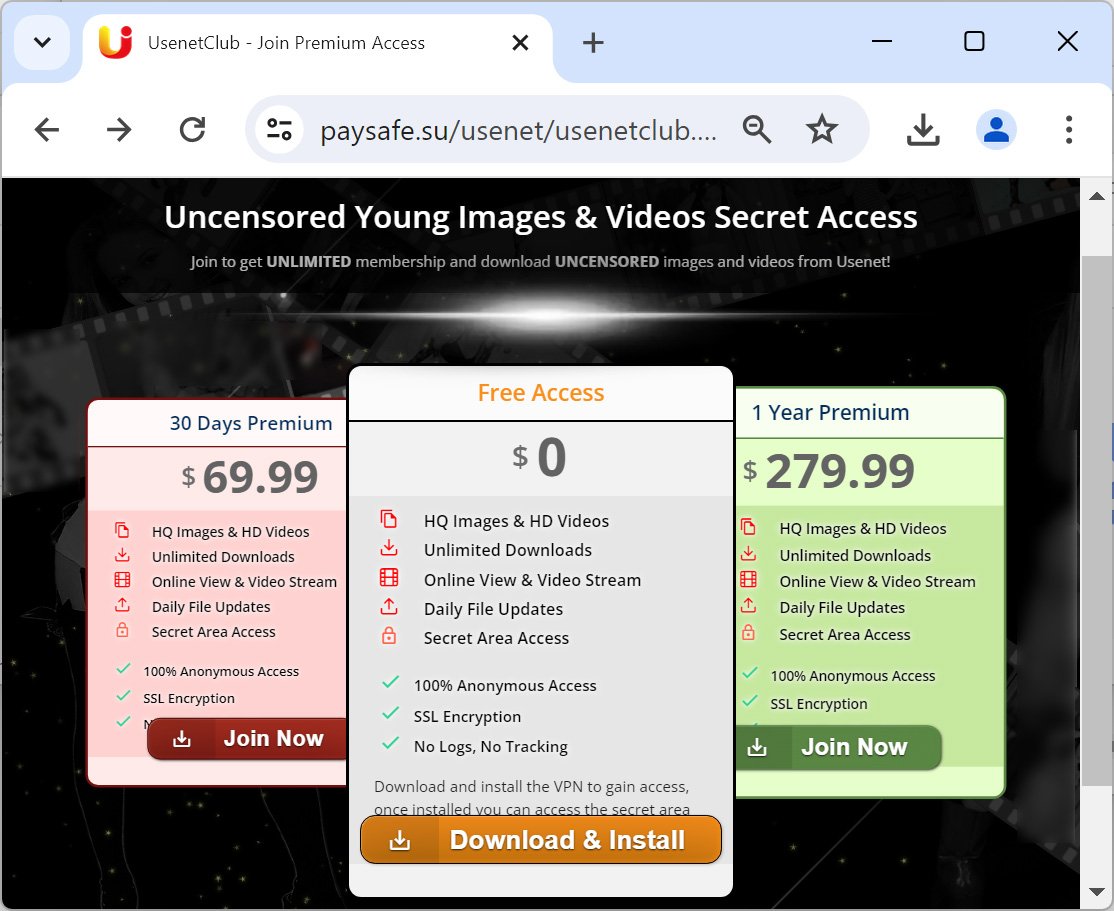
Source: BleepingComputer
Clicking on the "Download & Install" button will download a CryptVPN.zip file from the site that, when extracted, contains a Windows shortcut called "CLICK-HERE-TO-INSTALL".
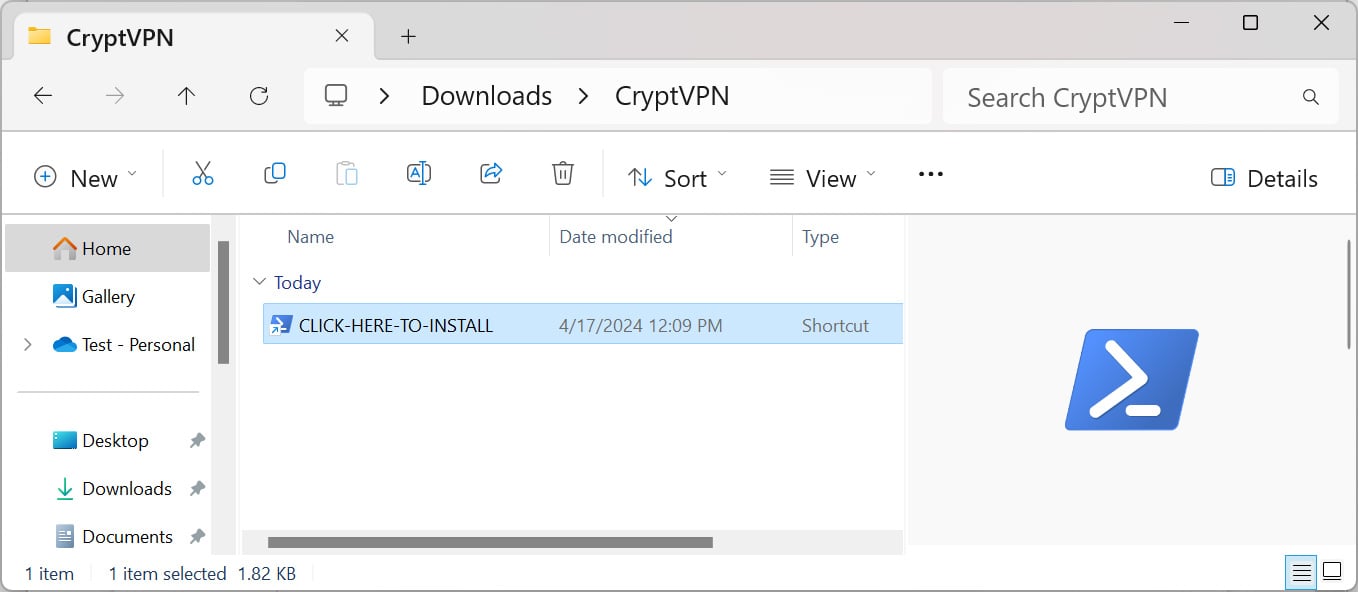
Source: BleepingComputer
This file is a shortcut to the PowerShell.exe executable with arguments to download the CryptVPN.exe executable, save it to C:\Windows\Tasks.exe, and execute it.
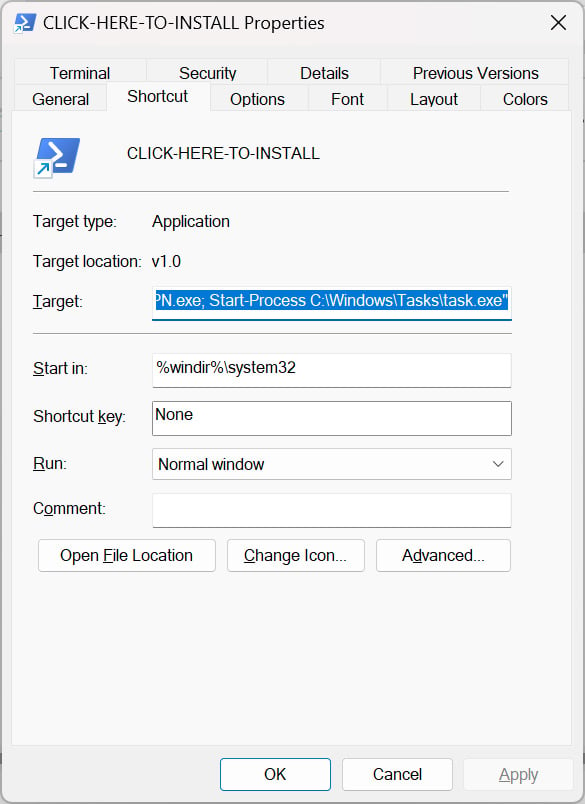
Source: BleepingComputer
The malware executable is packed with UPX, but when unpacked, it contains a PDB string that indicates that the author called the malware "PedoRansom".
C:\Users\user\source\repos\PedoRansom\x64\Release\PedoRansom.pdb
There is nothing special about the malware as all it does is change the target's wallpaper to an extortion demand and drops a ransom note named README.TXT on the desktop, containing similar extortion threats.
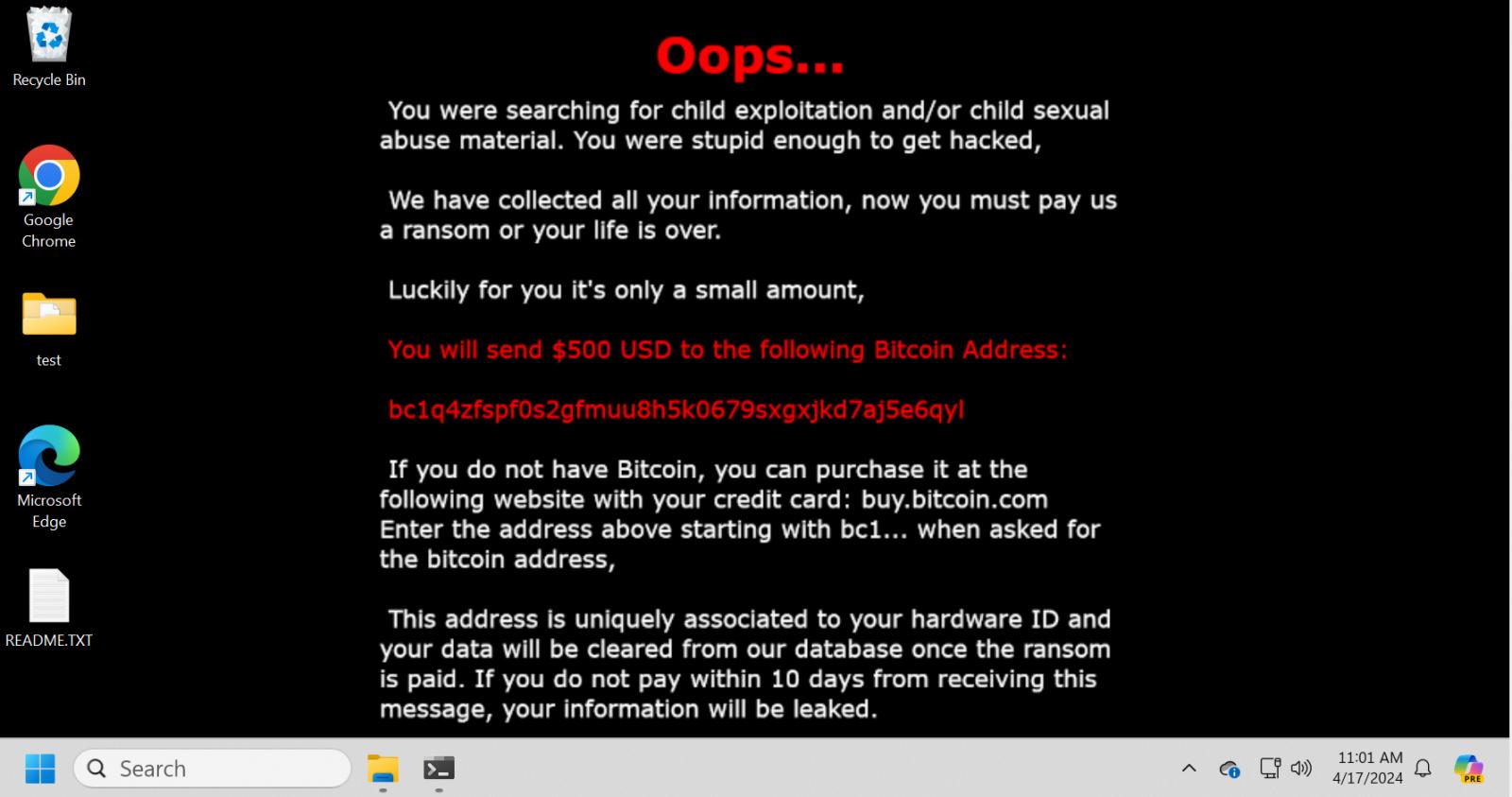
Source: BleepingComputer
"You were searching for child exploitation and/or child sexual abuse material. You were stupid enough to get hacked," reads the extortion demand.
"We have collected all your information, now you must pay us a ransom or your life is over."
The extortion goes on to state that the person must pay $500 to the bc1q4zfspf0s2gfmuu8h5k0679sxgxjkd7aj5e6qyl Bitcoin address within ten days or their information will be leaked.
This bitcoin address has only received approximately $86 in payments at this time.
Threat actors have been using "sextortion" tactics for a long time, commonly sending mass emails to large numbers of people to try and scare them into paying an extortion demand.
These tactics performed very well initially, with spammers extorting over $50,000 weekly in the early campaigns.
However, as time has gone by and recipients of these scams have grown wiser, sextortion campaigns do not generate the same revenue as they once did.
While this particular campaign is a bit more inventive and will scare many seeking this type of content, we will likely not see many people paying this extortion demand.









Comments
ZeroYourHero - 6 months ago
This should be a government sponsored group.
StodgyGolf - 6 months ago
Imma send money to that bitcoin address fr