
A fake ProtonVPN website was used since November 2019 to deliver the AZORult information-stealing malware to potential victims in the form of fake ProtonVPN installers as discovered by security researchers at Kaspersky.
ProtonVPN is a security-focused open-source virtual private network (VPN) service provider developed and operated by Proton Technologies AG, the Swiss company behind the end-to-end encrypted email service ProtonMail.
AZORult is an ever-evolving data-stealing Trojan selling for roughly $100 on Russian underground forums, also known to act as a downloader for other malware families when used in multi-stage campaigns.
This Trojan was previously spotted by researchers as part of large scale malicious campaigns spreading ransomware, data and cryptocurrency stealing malware.
AZORult is designed to collect and deliver as much sensitive information as possible to its operators, from files, passwords, cookies, and browser history to cryptocurrency wallets and banking credentials once it infects a targeted machine.
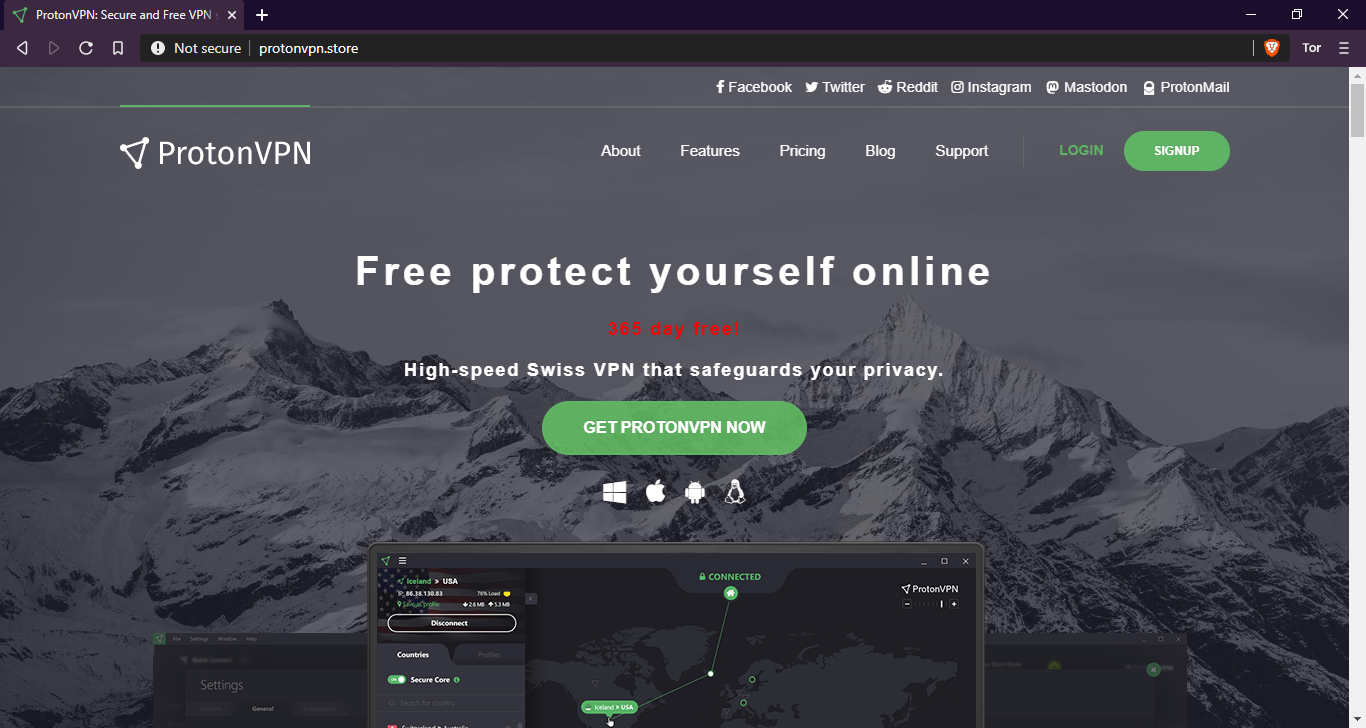
Delivery through fake ProtonVPN site
As Kaspersky's researchers discovered, protonvpn[.]store, the website used to deliver the malicious fake ProtonVPN installers (also spotted by DrStache), was registered via a Russian registrar in November 2019.
That is when this campaign also started delivering AZORult malware payloads using affiliation banner network malvertising as one of the initial infection vectors.
"When the victim visits a counterfeit website and downloads a fake ProtonVPN installer for Windows, they receive a copy of the AZORult botnet implant," Kaspersky threat researcher Dmitry Bestuzhev explains.
The campaign's operators made an identical copy of the official ProtonVPN website with the help of the open-source HTTrack web crawler and website downloader utility.
.png)
After the fake ProtonVPN installer named ProtonVPN_win_v1.10.0[.]exe is launched and successfully infects a target's computer, the malware starts collecting system information that gets delivered to the command-and-control (C2) server located on the same server as the fake site, at accounts[.]protonvpn[.]store.
The AZORult Trojan then proceeds to "to steal cryptocurrency from locally available wallets (Electrum, Bitcoin, Etherium, etc.), FTP logins and passwords from FileZilla, email credentials, information from locally installed browsers (including cookies), credentials for WinSCP, Pidgin messenger and others."
This information will then be packed and exfiltrated to the threat actors operating this malvertising campaign that abuses the ProtonVPN service.
More details and indicators of compromise (IOCs) including file names and hashes of fake ProtonVPN installers used in this campaign are available within Kaspersky's report.
Previous fake site encounters
This is not the first time attackers have used fake VPN sites to push malware payloads on unsuspecting victims, with an almost perfect clone of the NordVPN VPN service official website being used as a delivery platform for a banking Trojan.
A fake VPN named 'Pirate Chick VPN' was used to infect victims with the AZORult password-stealing Trojan last year after the initial installation.
The AZORult Trojan was also delivered via a fake BleachBit website with the end goal of harvesting and exfiltrating the victims' credentials and files.
Another threat actor created a site that promoted a fake VPN that would install the Vidar and CryptBot password-stealing Trojans and attempt to steal user credentials and other sensitive information from the victims' computers.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now