
Security researcher Michael Gillespie has developed a new Windows app to help victims of ransomware infections.
Named CryptoSearch, this tool identifies files encrypted by several types of ransomware families and provides the user with the option to copy or move the files to a new location, in hopes that a decrypter that can recover the locked files will be released in the future.
Gillespie developed the app as a recovery and cleaning utility for computers that have been infected by undecryptable ransomware strains.
In these cases, it is impossible for PC owners to recover locked files, so the best course of action is to move all the encrypted data to a backup drive and wait until security researchers find a way to break the ransomware's encryption.
Gathering all encrypted files is a different story. Ransomware works by encrypting file types, and not folders, so victims usually have encrypted files spread all over their PC, not in a few central locations.
This is where CryptoSearch comes to help, by automating this search process, and the movement of these files to a new location. Once this operation finishes and PC owners have a backup of the encrypted data, they can clean up the computer by removing the ransomware's file, or optionally, wiping the hard drive and reinstalling the entire OS.
CryptoSearch works together with ID Ransomware
Under the hood, CryptoSearch works in tandem with the ID Ransomware service, meaning you have to be online when running the app.
According to Gillespie, CryptoSearch will query the ID Ransomware service in order to retrieve data needed to identify the type of ransomware that has locked the user's PC.
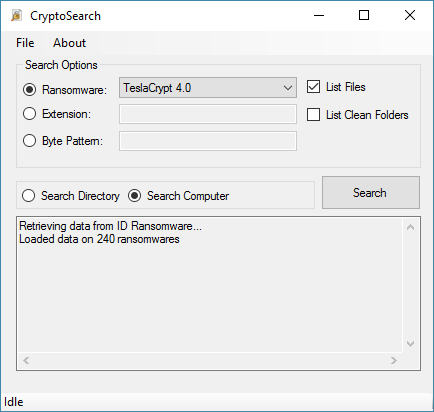
"This program is powered by my service ID Ransomware, and thus is always updated with definitions on the latest known ransomwares and their signatures," Gillespie wrote today on the Bleeping Computer forums, where he officially launched the app.
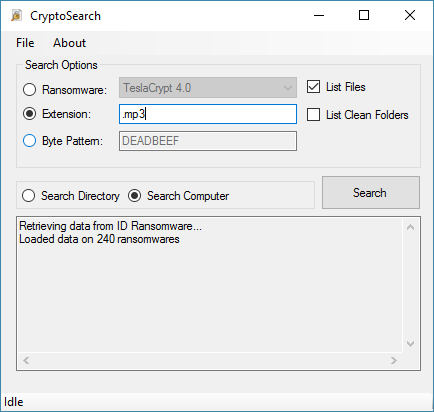
"When CryptoSearch is first launched, it will contact the website, and pull down the latest information on known extensions and byte patterns," Gillespie added. "It will identify files by known filename pattern or extension, or for some variants, the hex pattern in the encrypted file."
CryptoSearch uses this database to search the local file system, identify the ransomware infection, and then find all files locked by that ransomware.
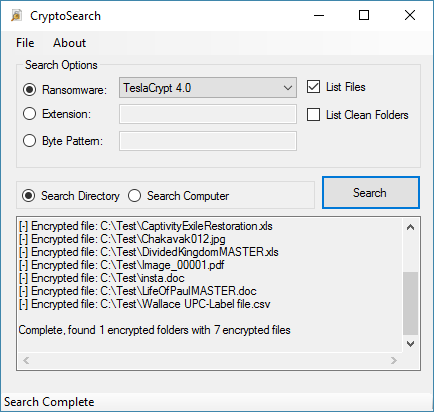
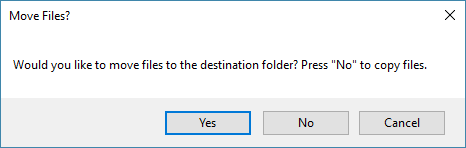
Once CryptoSearch has identified all files, the user is prompted via a menu and asked if he wants to move or copy the files, and then asked where to relocate the encrypted data.
Gillespie says that CryptoSearch is smart in the way it transfers files, keeping the initial folder structure. For example, files found in "C:\Test\Folder" will be moved to "J:\Backup\C\Test\Folder"
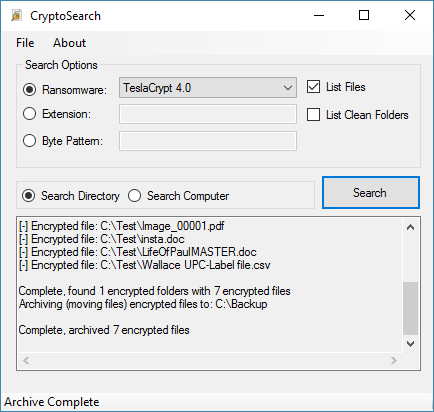
CryptoSearch is currently in a beta development stage, meaning more features will arrive in the future.
One of the currently requested features is an "offline mode" that will include static copies of the ID Ransomware database so that CryptoSearch could be used on computers not connected to the Internet.
Users asked for this feature because it's a standard practice in the case of ransomware infections to isolate computers by taking them offline. There's no timeline for this feature, so you'll have to keep an eye on Gillespie's Twitter feed or the CryptoSearch Bleeping Computer forum topic. CryptoSearch can be downloaded from here (For now, the ZIP is password-protected with the password: false-positive).
UPDATE: That was fast! Support for an "offline mode" was added just shortly after this article's publication.









Comments
DodoIso - 7 years ago
Excellent idea! Congratulations! In the forums, users are often confused as to what they can be kept aside, and what must be deleted.
vilhavekktesla - 7 years ago
Hi crypto trojans demon slayer :) Would you consider adding a view content of file. in some cases a .mp3 is valid, or for Cerber, where the extenison is changed while the content is not encrypted. And all other things I cannot think of right now. Since I have very few samples of encrypted files. I'm a bit hypothetic. but I guess I'd like to have a filter function or select all deselect all etc, select if, maybe regexp...
Since it is only about moving a file to another location and not simply erase no crisis when moving a false positive but still there may be issues. For instance you as the expert can show / detect the magic bytes of files with that. In other words try to minimise the chance for false positives :) But the simplest initial check is let the user show the content (hex and text view) And possible show highlite the the hex-patterns "proving" a file is encrypted as with Cryptowall. I just put out some ideas and I'm sure you have considered some already. It has to be implemented but it is less likely unless anyone requests them. If you need more details want to discuss you can use PM. Keep up the great work you do.
Amigo-A - 7 years ago
"""(For now, the ZIP is password-protected with the password: false-positive)."""
This phrase is already possible to remove. Password anymore not.
ntenzin75 - 7 years ago
didnt work for me, IN ID RANSOMWARE its detecting as xorist but by using CRypto Search not even single encrypted files is detecting . what cud be the problem
Demonslay335 - 7 years ago
What identifiers did ID Ransomware tag it as Xorist? CryptoSearch can only work off of known extensions for it, so if IDR identified only by attributes of the ransom note, then it won't be able to find the files.
You can PM me some encrypted files and I can test it out to see if its a bug.
xboch - 5 years ago
sir plis give me decrypt tools for ransomware ext .kiratos
vilhavekktesla - 5 years ago
Hi xboch, unfortunately it does not work that way. Many encryptors are quite sophisticated so when the data is encryptet it is lost / may be lost. Most advices is about backup and try not to pay ransom, which ofte has a considerable price. On bllping thoug you often find a forum deicated to your specific case and sometimes there is something to do. Search on blleping forums and chek the service id ransomware referred above.
717 different ransomwares are identified as of today.
hotguy1979 - 5 years ago
sir please provide .skymap decryptor tool
sunnykumar - 5 years ago
sir please provide .fordan decryptor tool
karafisalleh - 5 years ago
is there any decryptor for rumba variant that work? all else seems doesnt really work for me..
BonaAbraham - 5 years ago
some of my files decrypted with stopdecryptor, but can't see where it located. please help me to decrypt my all files. Here is same info:
No key for ID: wKtYvYaEdt2ty68nSobDaFNP1BdrVao7GLVJjeJN (.mogranos )
No key for ID: 9vfpmvri6cTZ9H29Z9uMVrZYgr4wwXG36rYZShtC (.format )
MACs: F4:30:B9:37:17:A8, 10:F0:05:C4:05:14, 00:FF:D8:BC:8B:C7, 10:F0:05:C4:05:13
Please let me know if any news
Thanks
Alituma - 5 years ago
I'm not sure but I think I found the key for encrypted files with .DOMN extension by using the notepad++.it was written in the last line of every .DOMN program with personal ID but can I decrypt the files with that key without using any program? please answer me
Demonslay335 - 5 years ago
First off, your commend is unrelated to this article...
Second off, no. That is your personal ID, and the filemarker left by the ransomware. Read the FAQ in the support topic for STOP Djvu.
Ruslan_Aminov - 5 years ago
My files are encrypted. And identified like this. What am I to do?
ransomnote_email: gorentos@bitmessage.ch
sample_extension: .domn
sample_bytes: [0x1A3 - 0x1BD] 0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357D
jacquesb2 - 5 years ago
Brilliant work sir
AdnanMinhas - 5 years ago
Result:
We have identified "STOP (Djvu)".
This ransomware may be decryptable under certain circumstances.
Please refer to the appropriate
guide for more information.
Identified by:
sample_extension: .reco
sample_bytes: [0x1155B5 - 0x1155CF]
0x7B33364136393842392D443637432D344530372D424538322D3045433542313442344446357
D
Click here for more information about STOP (Djvu).
lusterr - 4 years ago
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-Be28TGxMAy
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
helprestore@firemail.cc
Reserve e-mail address to contact us:
datarestore@iran.ir
Your personal ID:
0194Asd374y5iuhldmjQby8HJfDgVqVAfkURTeXwrzQ5ym9SJknsR5n6p
edsonARQ - 4 years ago
ATTENTION!
Don't worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-BxcdyO2dt7
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
helpmanager@mail.ch
Reserve e-mail address to contact us:
helpdatarestore@firemail.cc
Your personal ID:
0223yiuduy6S5d01KCd0sa5ZVVwA8gOMyB7IrT1zf5LgYsSvBEVSnw
edsonARQ - 4 years ago
<p>como puedo recuperar mis archivos una ayuda por favor</p>
<p>Translated to English:<span lang="en">how can I get my files back please help</span></p>