Discord has introduced the DAVE protocol, a custom end-to-end encryption (E2EE) protocol designed to protect audio and video calls on the platform from unauthorized interceptions.
DAVE was created with the help of cybersecurity experts at Trail of Bits, that also audited the E2EE system's code and implementation.
The new system will cover one-on-one audio and video calls between users in private channels, audio and video calls in small group chats, server-based voice channels used for larger group conversations, and real-time streaming.
"Today, we'll start migrating voice and video in DMs, Group DMs, voice channels, and Go Live streams to use E2EE," reads Discord's announcement.
"You will be able to confirm when calls are end-to-end encrypted and perform verification of other members in those calls."
Originally built for gamers to communicate during gameplay, Discord has now grown to become one of the world's most popular communication platforms, catering to groups with common interests, creators, businesses, and various communities.
The introduction of DAVE is a significant move to enhance data security and privacy on the platform, which is used by over 200 million people.
Most importantly, Discord decided to make the protocol and its backing libraries open-source, allowing scrutiny by security researchers. A whitepaper with the complete technical information was also published, ensuring transparency towards the community.
DAVE technical overview
DAVE uses the WebRTC encoded transform API, which allows media frames (audio and video) to be encrypted after they are encoded and before they are packetized for transmission. The receiving end decrypts the frames and then decodes them.
Only special codec metadata, such as headers and reserved sequences, are left unencrypted.
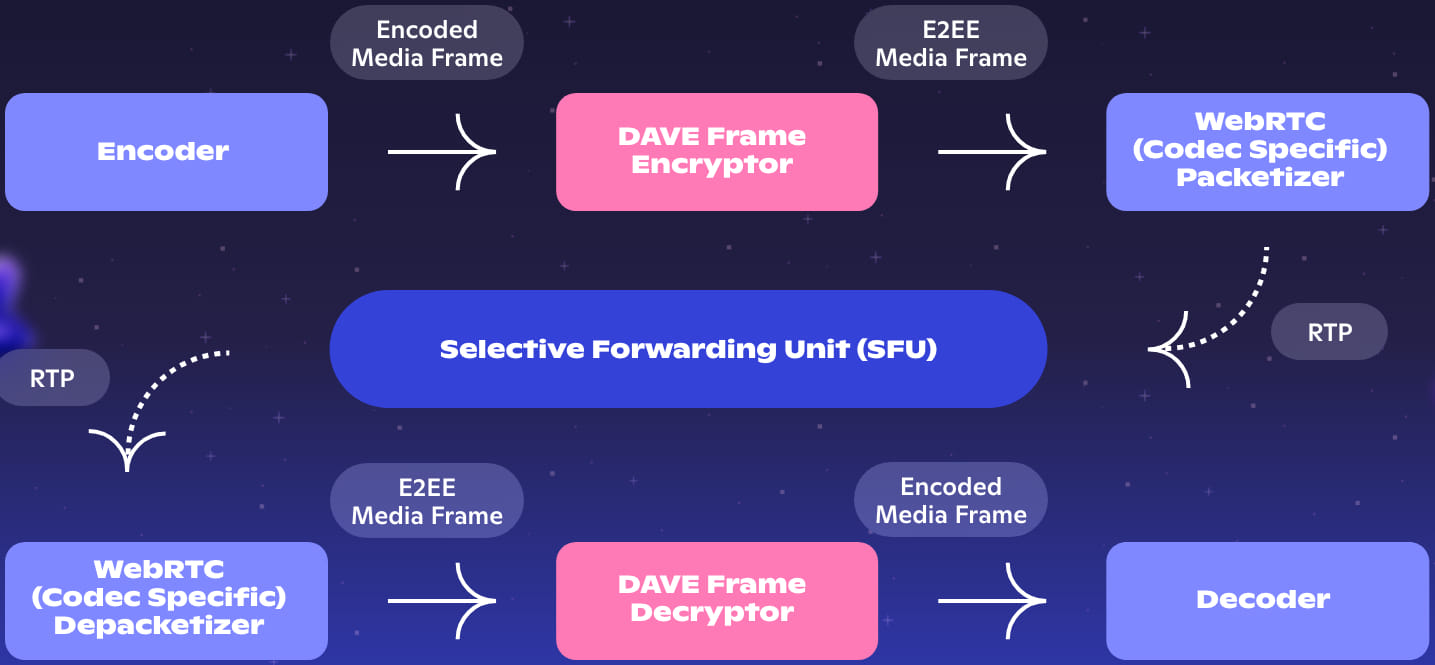
Source: Discord
In what concerns key management, the Messaging Layer Security (MLS) protocol is used for secure and scalable group key exchanges, while each participant has a per-sender symmetric media encryption key. Elliptic Curve Digital Signature Algorithm (ECDSA) is used for generating identity key pairs.
When a group's composition changes (a member leaves or a new member joins), a new 'epoch' begins, and the group's encryption state moves to that new epoch by generating new keys. This process should be completed without noticeable disruption for participants.
Discord says that MLS adds some latency for the key exchanges, but DAVE is designed to keep that delay under a few hundred milliseconds threshold, even in large group calls.
Finally, in what concerns user verification, there are out-of-band methods, such as a comparison of verification codes called 'voice privacy codes,' derived from the group's MLS epoch state.
Resistance to persistent tracking is achieved through the use of ephemeral identity keys, as users are assigned a new key for each call.
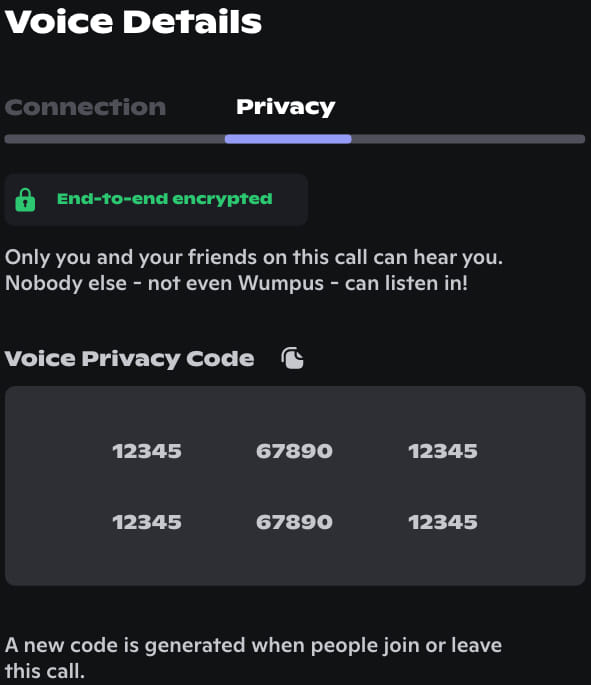
Source: Discord
Staged roll-out
Discord has started the migration process of all eligible channels to DAVE, and users will be able to confirm if their calls are end-to-end encrypted by checking the corresponding indicator on the interface.
It is expected that it will take some time before all users have full access to the new E2EE system across all devices and channels.
Users do not have to do anything other than upgrade to the latest client application, as outdated clients will be constrained to transport-only encryption.
The initial roll-out will cover Discord's desktop and mobile apps, with web clients to follow in the future.









Comments
mikebutash - 1 month ago
At least they didn't sit on their thumbs AFTER their massive leak of chat data. I'd never use it after that, but can't tell the kids today anything, and they still eat it up. Security what?
miuku - 1 month ago
It wasn't private messaging, it was only text from public channels. That's like saying you'll never use any public forum because messages from it were scraped.
Perhaps you should read up on it a little more before spouting FUD.