
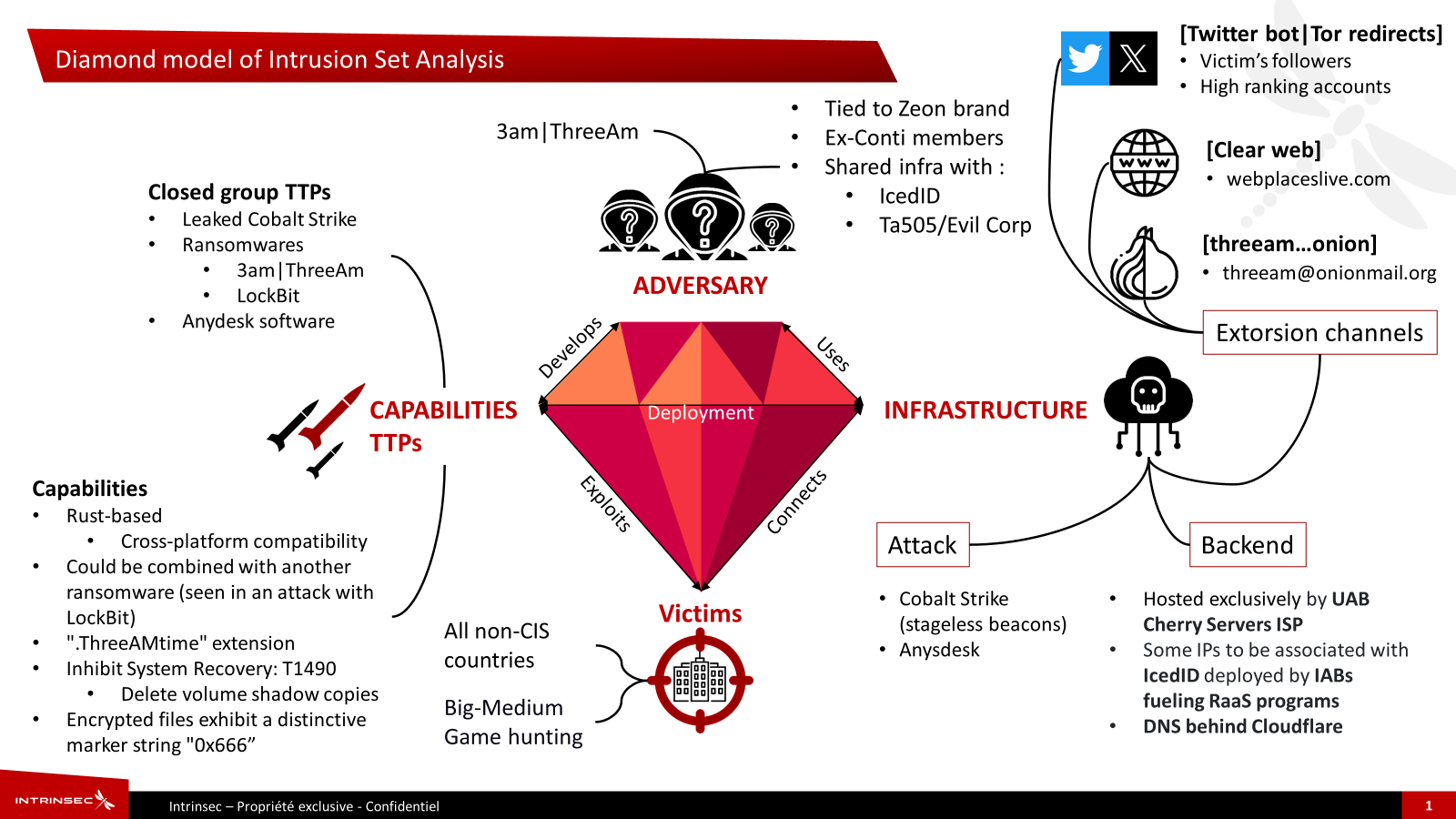
Security researchers analyzing the activity of the recently emerged 3AM ransomware operation uncovered close connections with infamous groups, such as the Conti syndicate and the Royal ransomware gang.
3AM, also spelled ThreeAM, has also been trying out a new extortion tactic: sharing news of a data leak with the victim’s social media followers and using bots to reply to high-ranking accounts on X (formerly Twitter) with messages pointing to data leaks.
3AM tied to Conti cybercrime syndicate
The 3AM ransomware gang's activity was first documented publicly in mid-September when the Threat Hunter Team at Symantec, now part of Broadcom, revealed that they noticed threat actors switching to ThreeAM ransomware after failing to deploy the LockBit malware.
According to researchers at French cybersecurity company Intrinsec, ThreeAM is likely connected to the Royal ransomware group - now rebranded as Blacksuit, a gang of former members of Team 2 within the Conti syndicate.
The link between 3AM ransomware and the Conti syndicate became stronger as Intrinsec progressed in their investigation of the group’s tactics, infrastructure used in attacks, and communication channels.
In a report shared with BleepingComputer, Intrinsec says that their analysis of the threat actor revealed “a significant overlap” in communication channels, infrastructure, and tactics, techniques, and procedures (TTPs) between 3AM and the Conti syndicate.
Using an IP address that Symantec listed as a network indicator of compromise (185.202.0[.]111) in their report on the threat actor's attack, Intrinsec researchers found on VirusTotal a PowerShell script for dropping Cobalt Strike that had been detected since 2020.
In another finding, Intrinsec observed a SOCKS4 proxy on TCP port 8000 that is typically used for tunneling communication. The researchers note that "the signature associated with this Socks4 service was displayed on two IP addresses showing such a proxy hallmark since mid-2022."
"This timeline of activity is in line with the one known for Zeon ransomware, which was observed in September 2022 according to Trend Micro but could have first spiked even earlier in late January 2022" - Intrinsec
Furthermore, Intrinsec analysts identified a TLS certificate for an RDP service on a machine called "DESKTOP-TCRDU4C" that is associated with attacks from mid-2022, some of them leveraging the IcedID malware dropper in campaings from Royal ransomware.
Previously, IcedID was used to deliver ransomware from XingLocker, which rebranded as Quantum, and Conti groups.
The researchers also found that the HTML content from 3AM’s data leak site in the Tor network had been indexed by the Shodan platform for internet-connected servers, meaning that it was available over the clear web.
Shodan showed an IP address associated with an “nginx product that could be used to proxy network traffic upstream towards a genuine server,” the researcher said.
Following the trail, Intrinsec noticed that the same Apache httpd banner on the server was present on 27 other servers, all hosted by an organization called “UAB Cherry Servers.”
Cherry Servers is a Lithuanian hosting company that has a relatively low fraud risk, but threat intelligence services have seen the company's customers hosting malware, such as Cobalt Strike.
source: Intrinsec
A closer analysis revealed that six of the 27 servers shared the same port, protocol, Apache product with the same version, autonomous system (AS16125), organization, and the text “llc” indicating a ‘limited liability company’.
Apart from this, the domains at the analyzed IP addresses had TLS certificates from Google Trust Services LLC and were transferred to Cloudflare.
Intrinsec found the same IP subnet in a report from cybersecurity and managed services company Bridewell last April, which notes that the ALPHV/BlackCat ransomware operation hosted its backend infrastructure exclusively on the UAB Cherry Servers ISP, used IP addresses in the same subnet, and some of them have been associated with the IcedID malware that had been used for Conti attacks.
Intrinsec's technical finding aligns with threat intelligence from RedSense saying that ALPHV is an allied group that is not part of the Conti syndicate but could help the gang in various ways to carry out attacks.
Testing Twitter bots to pressure victim
Digging for more public information about ThreeAM, Intrinsec’s cyber threat intelligence team discovered that the gang likely tested a new extortion technique using automated replies on X (formerly Twitter) to broadcast news of their successful attacks.
The threat actor set up an X/Twitter account last year on August 10 and used it to leave “numerous replies” mentioning one of its victims and redirecting to the data leak site.
3AM ransomware replied with a link to 3AM's data leak site on Tor network to tweets from the victim as well as various accounts, some with hundreds of thousands of followers, such as the example below.
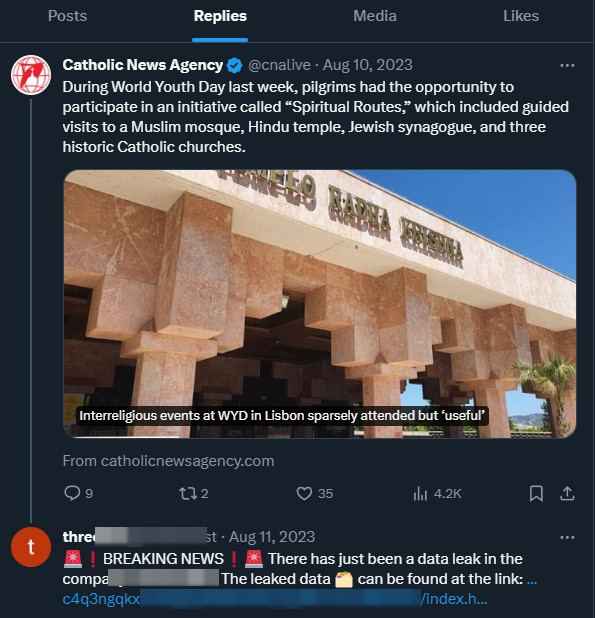
source: BleepingComputer
This tactic was likely employed to spread the news of the attack and subsequent data leak and to damage the business reputation of the victim - a U.S. company providing automated packaging services.
Intrinsec researchers determined that ThreeAM used the same message in an automated fashion to respond to multiple tweets from some of the victim’s followers.
“We assess with good confidence that an X/Twitter bot was likely used to conduct such a name and shame campaign,” Intrinsec writes in the private report shared with BleepingComputer.
Pointing to this theory is the increased volume and frequency of ThreeAM replies, sometimes as many as 86 per day, well over the average of a real user, and around four per minute.
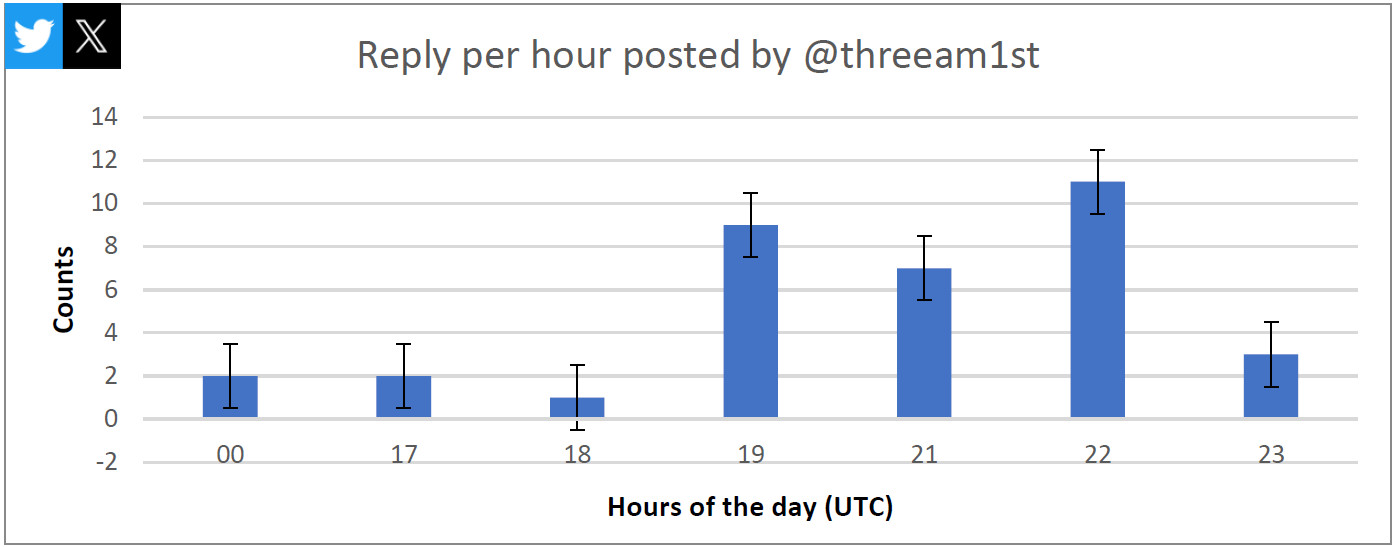
source: Intrinsec
It is worth noting that this tactic appears to have been employed only with one 3AM victim, likely because it did not yield the results the threat actor expected.
A look at 3AM’s data leak site in the Tor network shows a list of 19 victims who did not pay the ransom and whose data the threat actor leaked. Surprisingly, 3AM’s site looks very similar to the one the LockBit ransomware operation uses.
Intrinsec notes that “although ThreeAM intrusion sets seem to be a less sophisticated subgroup of Royal” and the gang displays less operational security it should not be underestimated and it could still deploy a large number of attacks.
The Conti syndicate
The Conti cybercrime syndicate was the largest and most aggressive ransomware operation between 2020 and when it shut down in May 2022 following a data breach known as Conti Leaks.
During one of its most productive hacking sprees, the operation’s affiliates compromised more than 40 organizations in a little under a month, the quickest attacks taking just three days from initial access to encrypting systems.
The syndicate split into multiple cells and the ransomware brand dissolved but many of its members and affiliates partnered with other operations, contributing with experienced individuals for all stages of an attack, from target analysis and initial access, to negotiations, infrastructure, developers, and operators.
One continuation is Royal ransomware, “the direct heir of Conti,” according to RedSense cyber threat intelligence researcher Yelisey Bohuslavskiy, a closed operation with members knowing one another personally.
Because of a post on a hacker forum, some researchers speculate that one of the leaders of the Royal group is a threat actor calling themselves Baddie. However, no other evidence has been disclosed publicly about this and ransomware these days is a constantly shifting scene, and Baddie could have just been working with multiple ransomware-as-a-service (RaaS) operations, Bohuslavskiy says.
On a scene as chaotic as affiliates working with multiple RaaS groups, it is difficult to track the members of a particular gang or tie them to an operation.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now