
A cybercriminal operation tracked as Ducktail has been hijacking Facebook Business accounts causing losses of up to $600,000 in advertising credits.
The gang has been spotted before using malware to steal Facebook-related information and hijack associated business accounts to run their own ads that are paid for by the victim.
Getting high-privilege role
Believed to be the work of a threat actor based in Vietnam, Ducktail was first documented earlier this year targeting individuals with high-level access to the Facebook business account that enables companies to reach a specific audience through paid campaigns and advertisements.
The threat actor would deliver info-stealing malware through LinkedIn, luring the target into launching a malicious file with a name related to brands, products, and product planning - typical keywords relevant to the victim.
Recent incidents investigated by researchers at WithSecure (previously F-Secure business) show that the operators behind Ducktail adapted their tactics and malware to avoid detection.
The threat actor contacted some of its newest victims over WhatsApp to lure them into accepting and executing malicious payloads that would steal sensitive information or provide the attacker access to the Facebook business account.
"One of the unique features of the malware is its ability to hijack Facebook Business accounts associated with the victim’s Facebook account. It attempts to grant the threat actor’s emails access to the business with the highest privilege roles," researchers say in a report in July.

source: WithSecure
They further explain that a Facebook business account can be associated with multiple email addresses that are used for access to the Business Manager panel with various permissions: admin, employee, finance analyst, and finance editor.
Individuals with administrator and finance editor roles are Ducktail's main targets as they have control over the settings, people's permissions, tools, and financial details (business credit card info, transactions, invoices, and account payment methods).
Once launched on the victim's system, the Ducktail malware can steal all stored cookies (Facebook session cookies included) from Google Chrome, Microsoft Edge, Brave, and Firefox.
Using the session cookie, it interacts with various Facebook endpoints from the victim's machine and collects further information (access tokens, two-factor authentication codes, user agents, IP address, geolocation) that would allow the threat actor to impersonate the victim from other systems.
Ducktail operation evolves
In the new campaign, the threat actor switched to a new malware variant that uses the .NET 7 Native AOT feature that allows compiling the binary without .NET runtime installed on the victim's machine.
Another difference is that the operator's email addresses are no longer hardcoded in the binary but delivered from Telegram bot accounts acting as command and control (C2) servers.
Telegram was also used in the same for the latest campaign, but the channels included multiple administrator accounts, which suggests that the threat actor may be running an affiliate program.
The researchers also note that exfiltrated data is now encrypted using the AES-128 algorithm and the key is protected through asymmetric encryption.

source: WithSecure
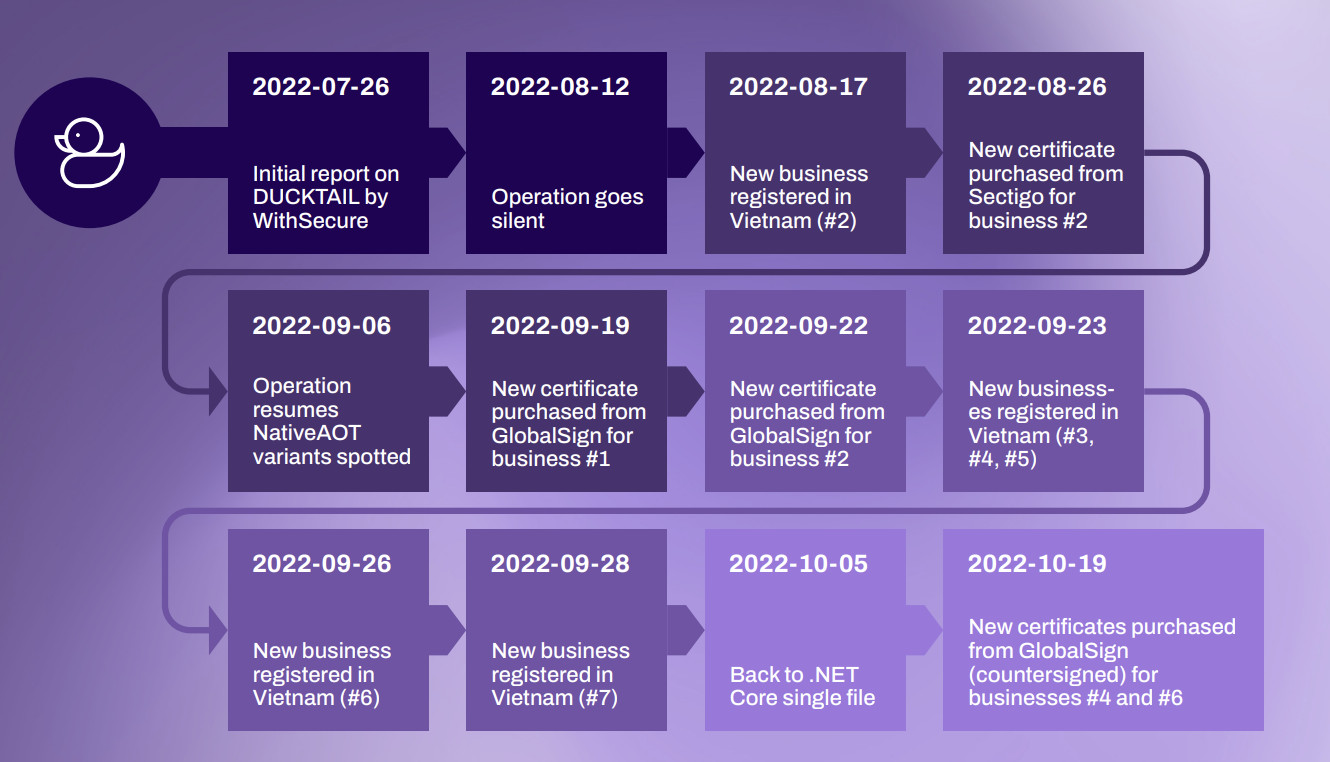
WithSecure noticed multiple malware samples submitted from Vietnam to VirusTotal between October 5-10 that they attributed with high confidence to the Ducktail operation.
To make detection more difficult, the threat actor signed their binaries with extended validation certificates, a tactic they have been using since mid-2021.
The certificates were purchased through businesses registered in Vietnam, none of the operational. WithSecure researchers identified seven of them, six of which they linked to Ducktail with medium confidence.
source: WithSecure
Based on the incident response engagements, the researchers say Ducktail targeted companies in the advertising industry, which reported direct financial damage between $100,000 and $600,000.
It is worth noting that cloud-security company ZScaler published a report in mid-October about a phishing campaign they also track as Ducktail, which shares similarities with the findings from WithSecure.
However, WithSecure told BleepingComputer that technical indicators and the intelligence collected do not reveal an overlap between the two operations.
"There are different threat actors operating in this space and WithSecure’s current assessment is that the recent campaign discovered by ZScaler is not a new variant or campaign conducted by or related to the operation tracked by WithSecure as DUCKTAIL" - WithSecure
As per WithSecure, what the two campaigns have in common is just the theft of information from the victim's Facebook account by using various Facebook pages and API endpoints (e.g. Graph).









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now