
A new ClickFix campaign is luring users to fraudulent Google Meet conference pages showing fake connectivity errors that deliver info-stealing malware for Windows and macOS operating systems.
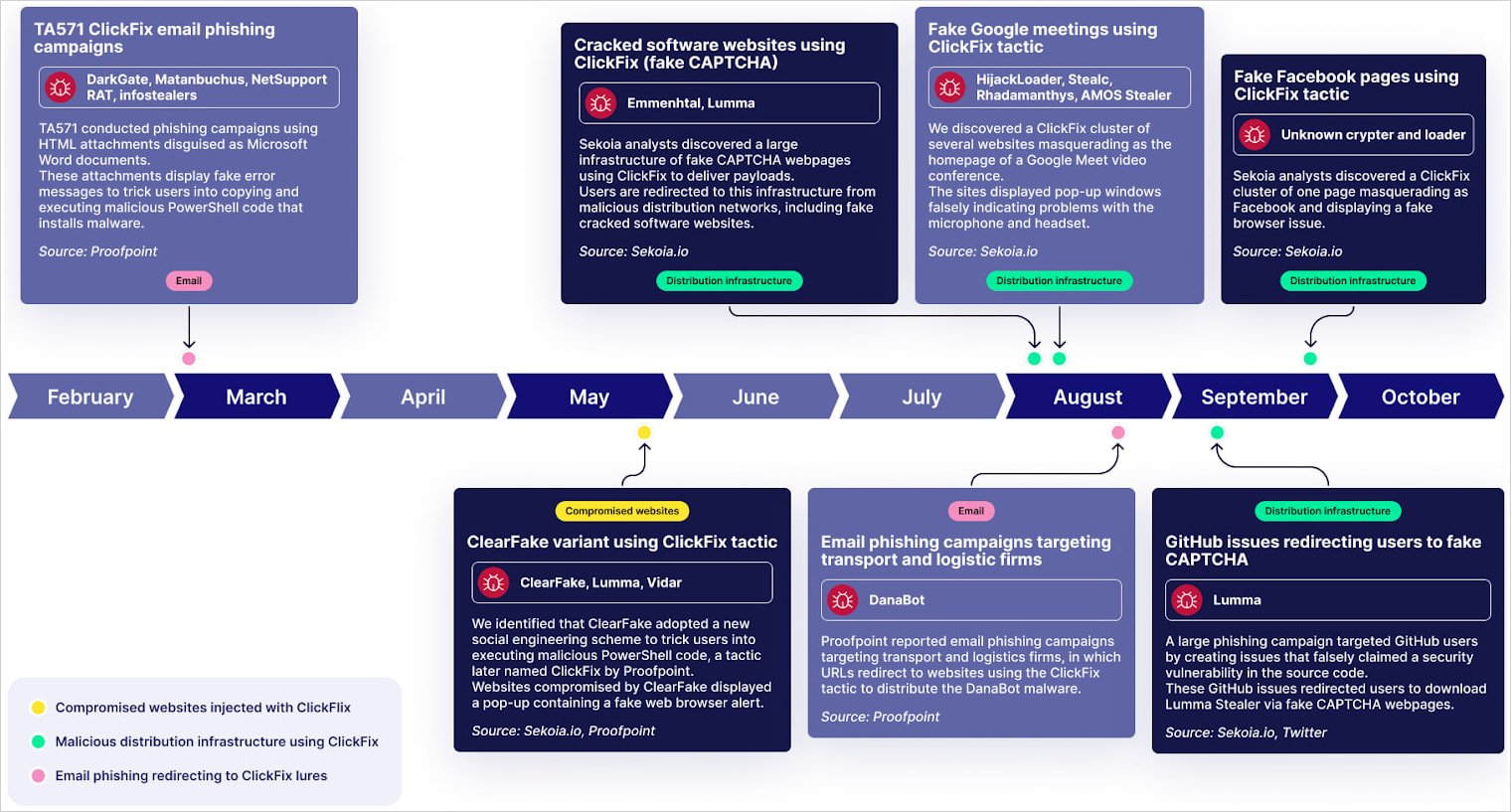
ClickFix is a social-engineering tactic that emerged in May, first reported by cybersecurity company Proofpoint, from a threat actor (TA571) that used messages impersonating errors for Google Chrome, Microsoft Word, and OneDrive.
The errors prompted the victim to copy to clipboard a piece of PowerShell code that would fix the issues by running it in Windows Command Prompt.
Victims would thus infect systems with various malware such as DarkGate, Matanbuchus, NetSupport, Amadey Loader, XMRig, a clipboard hijacker, and Lumma Stealer.
In July, McAfee reported that the ClickFix campaigns were becoming mode frequent, especially in the United States and Japan.
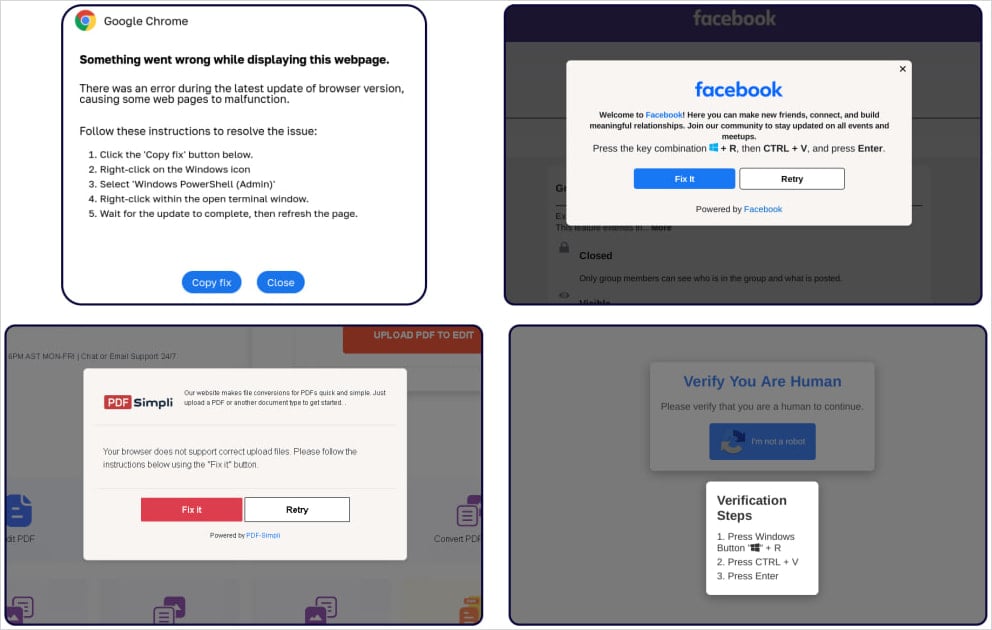
A new report from Sekoia, a SaaS cybersecurity provider, notes that ClickFix campaigns have evolved significantly and now use a Google Meet lure, phishing emails targeting transport and logistics firms, fake Facebook pages, and deceptive GitHub issues.
Source: Sekoia
According to the French cybersecurity company, some of the more recent campaigns are conducted by two threat groups, the Slavic Nation Empire (SNE) and Scamquerteo, considered to be sub-teams of the cryptocurrency scam gangs Marko Polo and CryptoLove.
Source: Sekoia
The Google Meet trap
The threat actors are using fake pages for Google Meet, the video communication service part of Google Workspace suite, popular in corporate environments for virtual meetings, webinars, and online collaboration.
An attacker would send victims emails that appear like legitimate Google Meet invitations related to a work meeting/conference or some other important event.
The URLs closely resemble actual Google Meet links:
- meet[.]google[.]us-join[.]com
- meet[.]google[.]web-join[.]com
- meet[.]googie[.]com-join[.]us
- meet[.]google[.]cdm-join[.]us
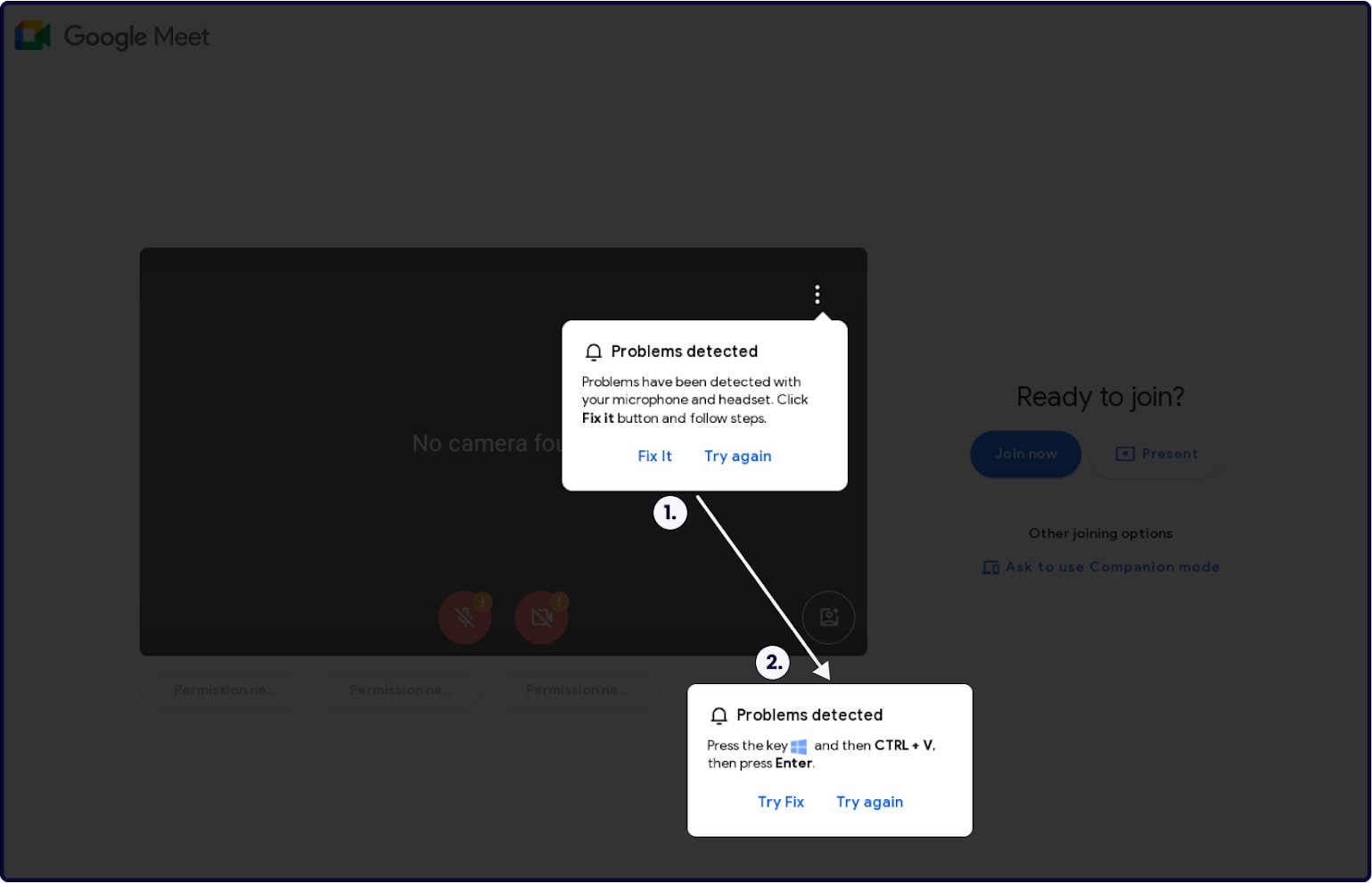
Once the victim gets on the fake page, they receive a pop-up message informing of a technical issue, such as a microphone or headset problem.
Source: Sekoia
If they click on "Try Fix," a standard ClickFix infection process starts where PowerShell code copied by the website and pasted on the Windows prompt infects their computer with malware, fetching the payload from the 'googiedrivers[.]com' domain.
The final payloads are infostealing malware Stealc or Rhadamanthys on Windows. On a macOS machine, the threat actor drops the AMOS Stealer as a .DMG (Apple disk image) file named 'Launcher_v194.'
Sekoia has identified several other malware distribution clusters in addition to Google Meet, including Zoom, PDF readers, fake video games (Lunacy, Calipso, Battleforge, Ragon), web3 browsers and projects (NGT Studio), and messenger apps (Nortex).









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now