
An affiliate of the Mallox ransomware operation, also known as TargetCompany, was spotted using a slightly modified version of the Kryptina ransomware to attack Linux systems.
This version, according to SentinelLabs, is separate from other Linux-targeting variants of Mallox, such as the one described last June by Trend Micro researchers, highlighting the shifting tactics of the ransomware ecosystem.
Also, this is another sign that Mallox, previously a Windows-only malware, is putting Linux and VMWare ESXi systems into its crosshairs, marking a significant evolution for the operation.
From Kryptina to Mallox
Kryptina was launched as a low-cost ($500-$800) ransomware-as-a-service (RaaS) platform for targeting Linux systems in late 2023 but failed to gain traction in the cybercrime community.
In February 2024, its purported administrator, using the alias "Corlys," leaked Kryptina's source code for free on hacking forums, which was presumably acquired by random ransomware actors interested in getting their hands on a working Linux variant.
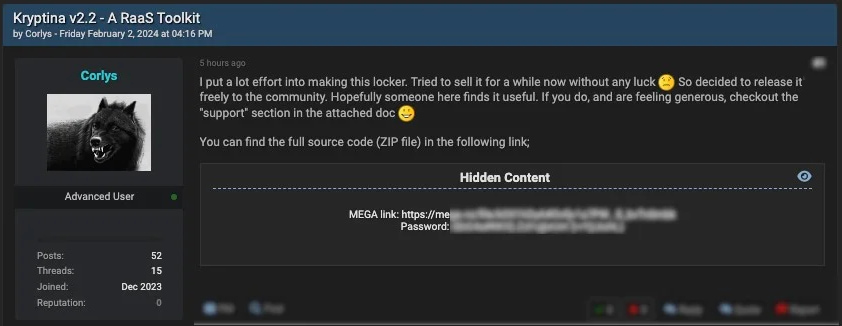
Source: SentinelLabs
After a Mallox affiliate suffered an operational error and exposed their tools, SentinelLabs discovered that Kryptina had been adopted by the project and its source code was used for building rebranded Mallox payloads.
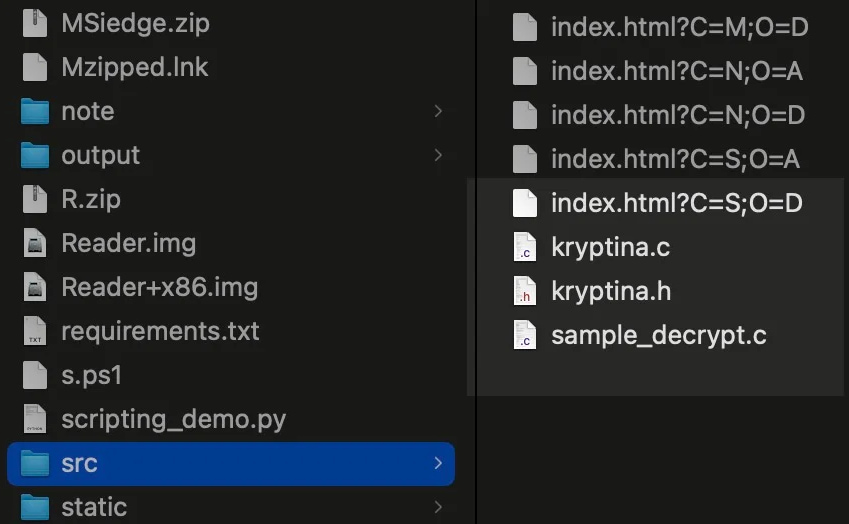
Source: SentinelLabs
The initial discovery of the exposing opendir was made in late May 2024 by security researcher Efstratios Lontzetidis, who found multiple samples of the new Mallox variant.
The rebranded encryptor, named "Mallox Linux 1.0," uses Kryptina's core source code, the same AES-256-CBC encryption mechanism and decryption routines, and also the same command-line builder and configuration parameters.
This indicates that the Mallox affiliate only modified the appearance and name, removed references to Kryptina on ransom notes, scripts, and files, and transposed the existing documentation into a "lite" form, leaving all the rest unchanged.
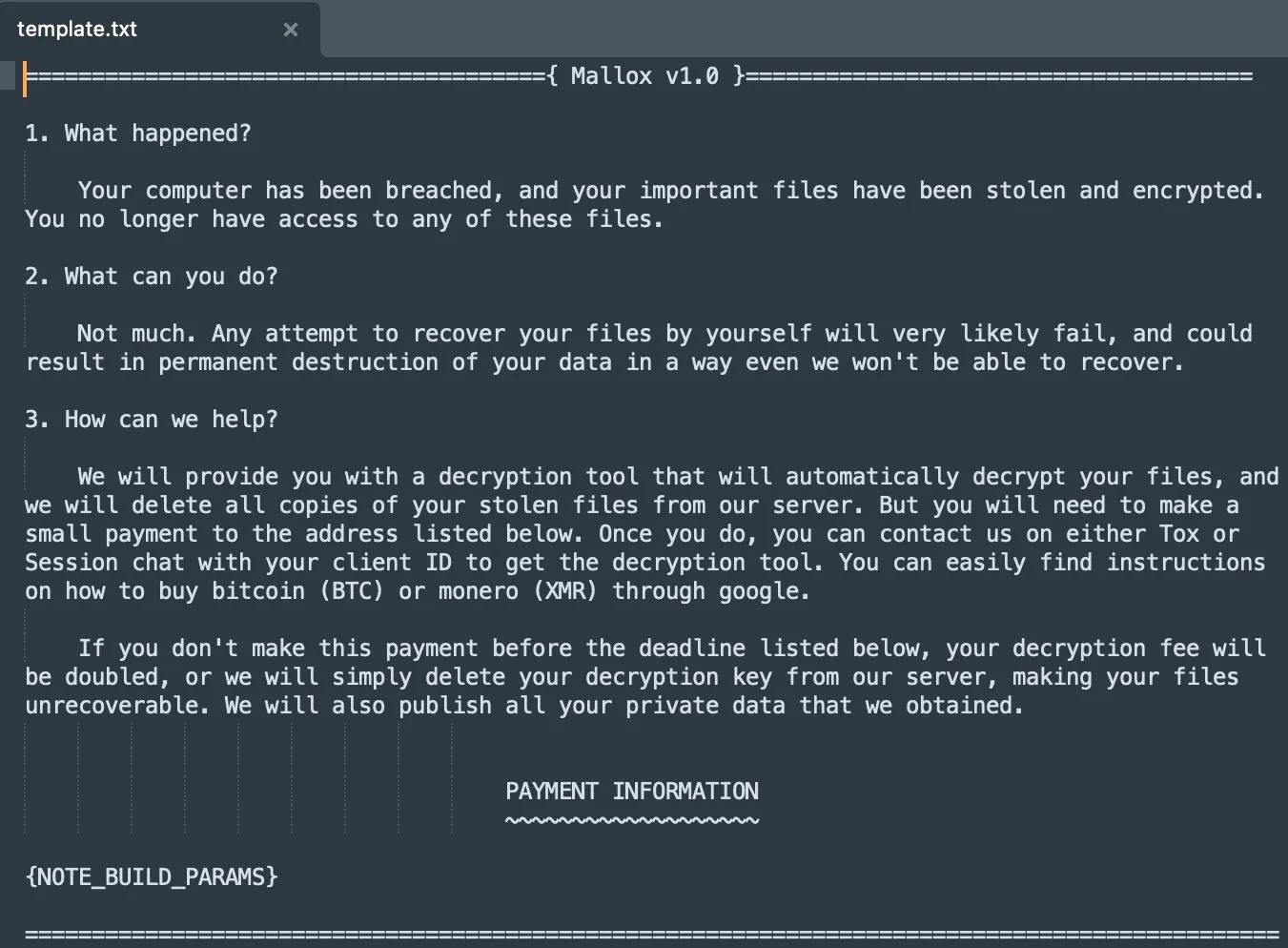
Source: SentinelLabs
Apart from Mallox Linux 1.0, SentinelLabs found various other tools on the threat actor's server, including:
- A legitimate Kaspersky password reset tool (KLAPR.BAT)
- An exploit for CVE-2024-21338, a privilege escalation flaw on Windows 10 and 11
- Privilege escalation PowerShell scripts
- Java-based Mallox payload droppers
- Disk image files containing Mallox payloads
- Data folders for 14 potential victims
Currently, it remains uncertain whether the Mallox Linux 1.0 variant is being used by a single affiliate, multiple affiliates, or all Mallox ransomware operators alongside the Linux variant discussed in our previous report.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now