
Threatpost has posted a story about a previously disclosed Netgear exploit that is now publicly being used to hack Netgear routers. This exploit allows a remote user to gain access to the administrative section of your router without knowing your login credentials as long as Remote Administration is enabled.
Once the router is exploited, attackers will modify its DNS server settings so that any DNS requests are being routed to DNS servers under the attacker's control. This allows the attacker to perform man-in-the-middle attacks or redirect users to fake banking and shopping sites in order to steal credit card information or account credentials. It has been reported that approximately 10 thousand routers have been affected by this vulnerability.
This exploit was first discovered by Compass Security who informed Netgear about the vulnerability on July 21st, 2015. A month later, Netgear sent them a beta firmware to be tested and Compass confirmed that the vulnerability was fixed. Unfortunately, Netgear never released the firmware to the public and thus this vulnerability still exists. On September 29th, 2015, Shellshock Labs also discovered the vulnerabilty and publicly disclosed it. On further research, it looks like variants of this vulnerability have been around since April of 2013!
It has since been discovered that attackers are now using this vulnerability and approximately 10,000 routers have been hijacked. As there is no available firmware updates that resolves this issue, it is important that all Netgear users disable Remote Administration on their routers as a precaution. To be honest, unless you absolutely need it, all remote administration on all routers should be disabled as it is a potential door into your network. The known Netgear firmwares that are affected by this vulnerability are 300_1.1.0.31_1.0.1.img and N300-1.1.0.28_1.0.1.img. The known list of affected Netgear models are JNR1010v2, JNR3000, JWNR2000v5, JWNR2010v5, N300, R3250, WNR2020, WNR614, and WNR618.
For Netgear users, you can disable Remote Administration by clicking on the Advanced category to expand it and then clicking on Remote Management. At the screen below, uncheck Turn Remote Management On and then click on the Apply button.
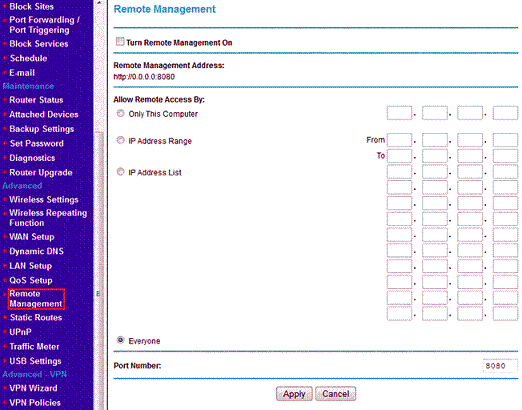
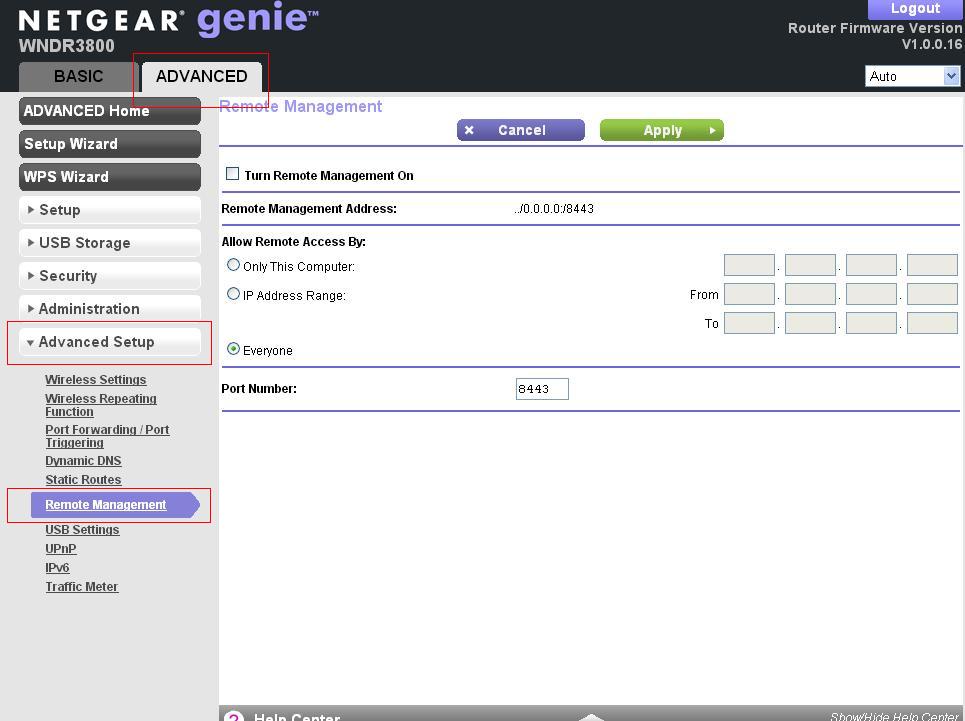
If you are using the Netgear Genie based interface, you can access the Remote Administration screen by clicking on the Advanced Setup category to expand it and then clicking on Remote Management. At the screen below, uncheck Turn Remote Management On and then click on the Apply button.
If you need help with this, please feel free to ask us here or in the forums.









Comments
Trantam - 9 years ago
Really Dangerous
Wildabeast - 9 years ago
My router isnt listed here, but I found out that I lost my login info. Is there a way to fix that? I clicked on the router login but theres nothing for lost password.
Am I outa luck?
Lawrence Abrams - 9 years ago
See this article to find the netgear default passwords in the event you lost it:
http://kb.netgear.com/app/answers/detail/a_id/1148/~/default-web-interface-password-for-netgear-devices
Otherwise the only legitimate way to recover the password is to reset the router to factory defaults.
Wildabeast - 9 years ago
Thanks Grinler, looks like Ill have to reset to factory default when I get home.