
The Black Basta ransomware gang has partnered with the QBot malware operation to spread laterally through hacked corporate environments.
QBot (QuakBot) is Windows malware that steals bank credentials, Windows domain credentials, and delivers further malware payloads on infected devices.
Victims usually become infected with Qbot via phishing attacks with malicious attachments. Even though it started as a banking trojan, it has had numerous collaborations with other ransomware gangs, including MegaCortex, ProLock, DoppelPaymer, and Egregor.
Black Basta teams up with Qbot
Black Basta is a relatively new ransomware operation that started impressively, breaching many companies in a relatively short time while demanding large ransom payments.
Analysts at the NCC Group discovered the new partnership between Qakbot and Black Basta during a recent incident response where they were able to identify the techniques used by the threat actor.
While ransomware gangs normally use QBot for initial access, NCC says that the Black Basta gang used it to spread laterally throughout the network.
More specifically, the malware remotely creates a temporary service on the target host and configures it to execute its DLL using regsvr32.exe.
Once Qakbot is up and running, it can infect network shares and drives, brute-force AD accounts, or use the SMB (Server Message Block) file-sharing protocol to create copies of itself or spread via default admin shares using current user credentials.
“Qakbot was the primary method utilized by the threat actor to maintain their presence on the network. The threat actor was also observed using Cobalt Strike beacons during the compromise,” explains the report by the NCC Group.
The analysts also note that they discovered a text file named “pc_list.txt” in the Windows folder, which contained a list of internal IP addresses of all systems in the network, likely generated by Qakbot.
Disabling Windows Defender
In the recent attack observed by the NCC responders, the Black Basta demonstrates the same characteristics that were seen since BleepingComputer initially reported on it.
These characteristics include modifying the wallpaper icon, deleting shadow copies, appending the .basta extension on encrypted files, and generating a company ID in the ransom notes.
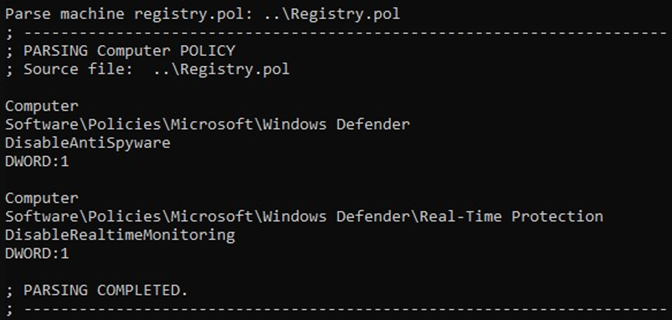
However, NCC states that the threat actors also disable Windows Defender to evade detection and minimize the chances of jeopardizing the success of the encryption step.
The ransomware operators achieved this goal either by executing PowerShell commands or creating a GPO on a compromised Domain Controller, which would perform changes on the Windows Registry.
Qakbot can quickly move inside compromised networks, snatching account credentials and pivoting to adjacent workstations. Still, the ransomware payload isn't immediately fetched, so there's always a window of opportunity for the defenders before catastrophe hits.
The trojan has intricate and varying attack pathways, each with its own opportunities for detection, but they all begin with the arrival of a malicious email. Hence, this is where the most attention needs to be paid, avoiding opening attachments or clicking on embedded links.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now