
Apple has launched the first Rapid Security Response (RSR) patches for iOS 16.4.1 and macOS 13.3.1 devices, with some users having issues installing them on their iPhones.
As the company describes in a recently published support document, RSR patches are small-sized updates that target the iPhone, iPad, and Mac platforms and patch security issues between major software updates.
Some of these out-of-band security updates may also be used to address vulnerabilities actively exploited in attacks.
"They deliver important security improvements between software updates — for example, improvements to the Safari web browser, the WebKit framework stack, or other critical system libraries," Apple explains.
"They may also be used to mitigate some security issues more quickly, such as issues that might have been exploited or reported to exist 'in the wild'."
You can go through the following steps to check if RSR patches are available for your device:
- iPhone or iPad: Go to Settings > General > Software Update > Automatic Updates, then make sure that "Security Responses & System Files" is turned on.
- Mac: Choose Apple menu > System Settings. Click General in the sidebar, then click Software Update on the right. Click the Show Details button next to Automatic Updates, then make sure that "Install Security Responses and system files" is turned on.
Should you disable automatic updates or decline to install Rapid Security Responses when offered, your device will receive the security patches as part of a future software upgrade.
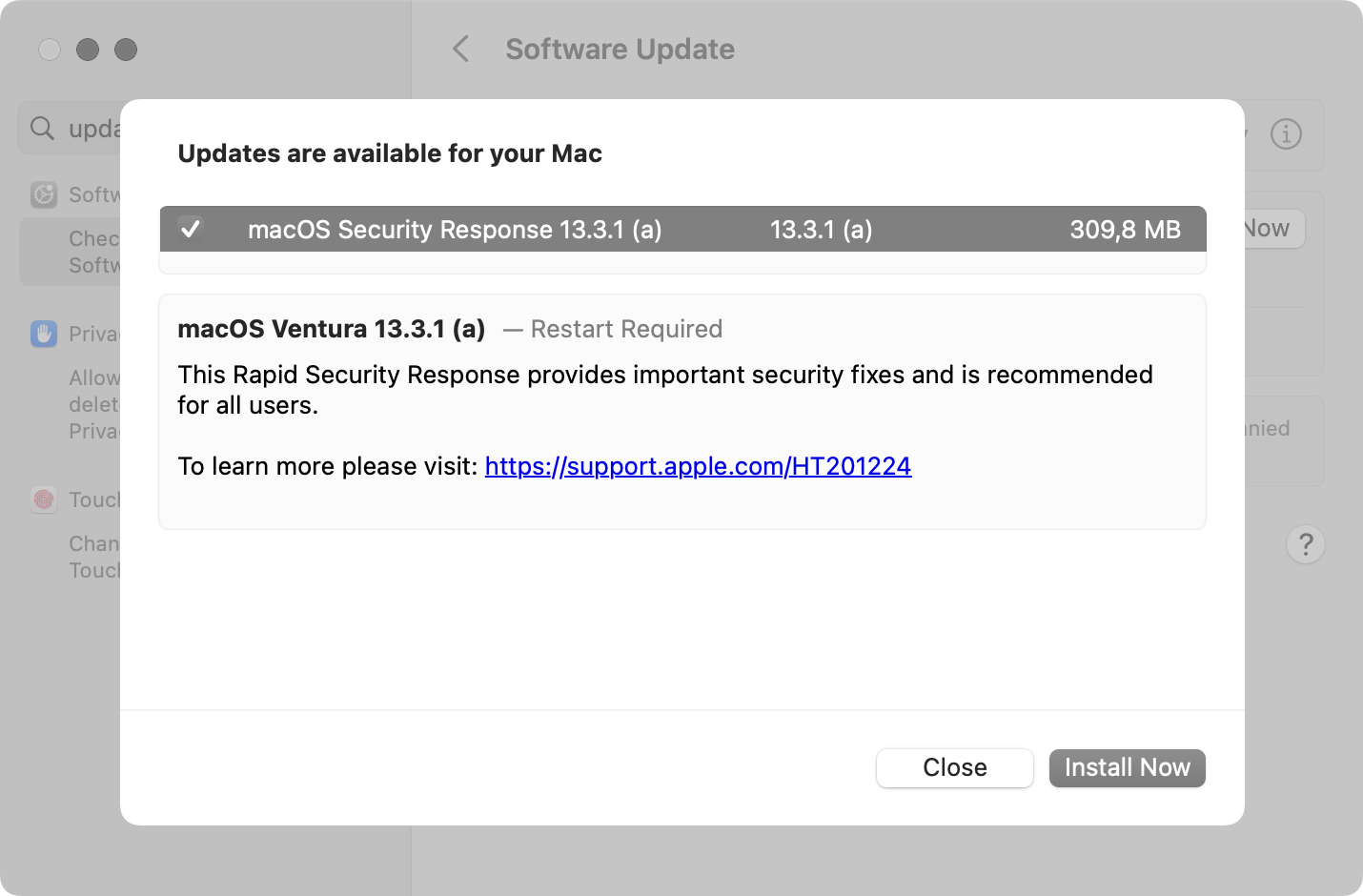
First RSR patch fails to install on some iPhones
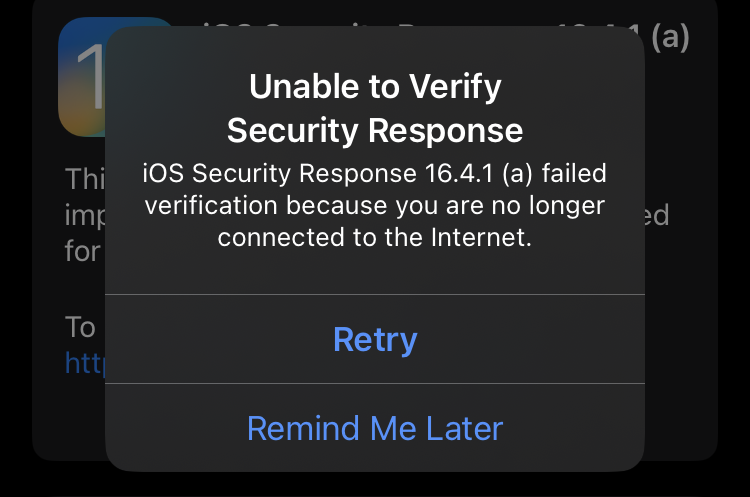
According to user reports [1, 2, 3, 4], the RSR update delivered today for iPhones also fails to install on some devices with "Unable to Verify Security Response" errors.
"iOS Security Response 16.4.1 (a) failed verification because you are no longer connected to the Internet," the errors read.
Despite this, as BleepingComputer confirmed, the affected devices are connected to the Internet, and a server-side bug likely causes the issues.
While today's Rapid Security Responses are rolling to all iOS and macOS users, Apple is yet to share what security improvements they bring.
The "Apple security updates" page, which usually lists the latest security updates, has no details on today's RSR patches, and Apple has not yet shared where they'll share this information.
The only info shared on the update screen is that "This Rapid Security Response provides important security fixes and is recommended for all users. To learn more please visit: https://support.apple.com/HT201224."
However, the page linked in the release notes is the support page published this week to explain what Rapid Security Responses are, which provides no additional details on what security vulnerabilities were fixed today.
An Apple spokesperson was not immediately available for comment when contacted by BleepingComputer for more details on what was patched in today's RSR updates and what is causing the install issues.









Comments
DarthTater - 1 year ago
Installed without an issue on my iPhone 13 which had iOS 16.4.1 already installed and now shows 16.4.1 (a)
Very fast to download and install. I like this for security updates vs the much larger full iOS updates.
LIstrong - 1 year ago
They got a little snippy yesterday when I noticed something. They claimed I had a lot of deleted apps but I never installed apps so how were they deleted? I understand how offloading apps works and that’s not what I see.
I suspect Apple never truly deletes apps, just suspends the view and that’s very dangerous to keep them in memory and let this history survive device retirement. I use devices very differently than I did in 2009. Just because I gave an app access to my data 10 years ago, doesn’t mean they still have permission to access my phone.
Also I suspect they need to let us delete texts without previewing them. We should be able do this by recipient alone without swiping. If we have unknown texts go into separate folder then we should get a list of texts recipients and whether want them deleted. I suspect the act of previewing texts (our alerts) can be how malware is delivered. But now we can only suspend previewing all texts, not by known or unknown recipients.
I also suspect alerts of all types is how data is leaked. Try sending an email without a subject line and you will see what I mean.
LIstrong - 1 year ago
Got a hang up call from China right after I posted this. So obviously I hit upon something and I need to add receiving a call from China to the list of unwanted vulnerabilities. We should be able to whitelist or blacklist countries (country codes). That would cut down on attacks and spam.
scpcguy - 1 year ago
This, coupled with the fast download/install, smacks of Apple simply trying to test the feature...which apparently still has bugs:
"the page linked in the release notes is the support page published this week to explain what Rapid Security Responses are, which provides no additional details on what security vulnerabilities were fixed today."