
A new cryptocurrency mining malware dubbed LoudMiner uses virtualization software to deploy a Linux XMRig coinminer variant on Windows and macOS systems via a Tiny Core Linux virtual machine.
The malware comes bundled within cracked copies Windows and macOS VST software such as Propellerhead Reason, Ableton Live, Sylenth1, Nexus, Reaktor, and AutoTune.
LoudMiner is distributed via an attacker-controlled website which currently links to 137 VST-related apps, 42 of them for Windows and 95 for the macOS platform, all of them frequently updated and hosted on 29 servers, as discovered by ESET Research's detection engineer Michal Malik.
LoudMiner targets victims with powerful systems
The threat actors seemingly target audio production systems known for having high-end hardware and for being under constant load while processing audio content, a good way to conceal a surreptitious Monero cryptomining operation.
While the Tiny Core Linux virtual machine and the coinminer can easily be well over 100 MB in size when uncompressed, the malware's developers don't really have a reason to find a way to shrink them given that VST hosts are known to be quite large.
This makes it possible to hide the malware "in plain sight," with the victims deploying LoudMiner on their own systems by installing the pirated VST host software that comes "bundled with virtualization software, a Linux image and additional files used to achieve persistence."
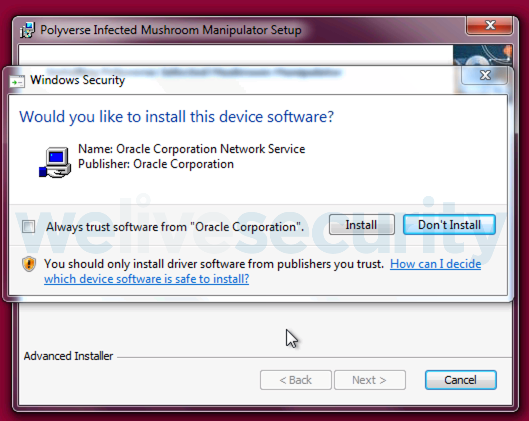
During the installation process, LoudMiner is the first to be dropped on the now compromised computer together with various scripts and the virtualization software needed to run the Linux coinminer VM — QEMU for macOS and VirtulBox for Windows — with the VST software being installed afterward.
"While analyzing the different applications, we’ve identified four versions of the miner, mostly based on how it’s bundled with the actual software, the C&C server domain, and something we believe is a version string created by the author," says Malik.
Infecting Windows and macOS computers
On macOS, LoudMiner will add "plist files in /Library/LaunchDaemons with RunAtLoad set to true" for persistence, with the KeepAlive option also set to true, ensuring the malicious process will be restarted if stopped.
These plists will automatically launch a number of shell scripts designed to launch the virtual machines on boot and load two instances of the coinminer infested images.
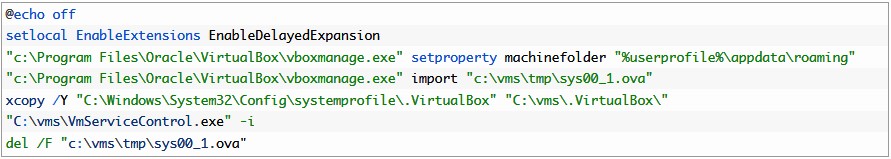
On Windows machines, the malware uses a batch script to launch the coinminer's Linux image as a service to make sure that it will be relaunched after restarts.
"The Linux image is Tiny Core Linux 9.0 configured to run XMRig, as well as some files and scripts to keep the miner updated continuously," as explained by Malik, with the updates being performed via three scripts which communicate with LoudMiner's command-and-control (C2) server via SCP (Secure File Copy).
On infected Macs, the malware also uses a "CPU monitor shell script with an accompanying daemon that can start/stop the mining based on CPU usage and whether the Activity Monitor process is running," according to Malik.
"The CPU monitor script can start and stop the mining by loading and unloading the daemon. If the Activity Monitor process is running, the mining stops."
More details on the four LoudMiner variants discovered, a full list of Indicators of Compromise (IoCs), as well as more info on the used MITRE ATT&CK techniques can be found within ESET Research's in-depth malware analysis.
While LoudMiner's usage of virtualization for targeting multiple platforms is quite exotic, it's definitely not a new idea, with researchers presenting a malware strain using VMs as part of its infection process in a paper from 2006.
The paper in questions is "SubVirt: implementing malware with virtual machines" paper published by researchers from Microsoft Research and the University of Michigan and it is available here, in PDF format.
The research showcases a virtual-machine-based rootkit (VMBR) that "installs a virtual-machine monitor underneath an existing operating system and hoists the original operating system into a virtual machine."









Comments
Angrywife - 5 years ago
We have been dealing with a similar malware for a few years. We will reinstall windows and it looks good for a while than suddenly it gets bolder and just takes over. There literally nothing suspicious looking unless you know what your looking for. It will install its own drivers from the C&C linked sites and take over our security first. I have Comodo security and internet security paid versions. It has been on my husband's computer this whole time and 2 weeks ago i bought a new laptop that i reset windows on instantly and everything was fine until my husband started poking at the program again. It has now basically wiped his computer and we have to reinstall the bios software, it downloaded drivers for his iphone and my daughters phone and my husband can hardly charge it (we put in a new battery last month) because it is running so much in the background it just drains in a matter of minutes when he takes it off. It has moved into our router and downloaded itself into my new computer. This stuff is nasty! When i plug in a 2nd monitor before starting i can see the bios boot up otherwise my screen is blank amd not active until after windows loading screen happens on the 2nd screen (even without the screen) it will not allow me access to my bios as it does not register my keyboard until after windows in loaded. Both of our copies of windows are legitimate copies especially mine that came factory pre installed. We had a usb drive my ex husband have us with all my kids pictures when it started that instantly made my old 50g hard drive i was removing photos from fill up in a matter of minutes and i lost everything i was trying to save. That is the only thing we think it came from. We even have my husbands computer in 4 separate partitions amd it moves between them with no issues. At this point im about to have a bonfire and throw everything in it and start from ground zero with electronics.
abgehort - 4 years ago
Hello,
I understand how you feel about the brazen and persistent nature of present day malware.
Recently I had an infection that spanned 2 laptops, a desktop and NAS. It required cross-platform usage of tools to bring it "under control". I mostly wanted to share some discoveries with you that from the gist of your rant seem to be the most maddening to you. So you don't feel its "Magic". 1) You disclosed that you knew that malware-virus was connecting to C2 servers. Yes they do that and they (either the app or operator) do escalate. So your IP/MAC addresses are compromised... Need to change to a new number. Malware doesn't have precognition (yet) so often an uninfected system gets compromised from being placed in the same place physically or virtually. I would recommend a Dynamic DNS or a secure DNS for communications and make sure you have a way to physically unplug PC from the internet. 2) I find that the persistence of malware and that it strikes at something we use for home and work cause extreme actions. Back in the day more "evolved" virus coders would create "hoaxes" that would lead the administrator or user of the system(s) to wipe their own drives and rebuild from base. Until recently I felt that compartmentalizing by partitions and having a legit updated windows with pass-protect user accounts offered security. That issues could be contained tp a drive or login.... Nope I discovered that all MS Windows has something called IPC (Inter Process Communication) so it is always talking especially to executables. I thought I was losing my mind on how the malware could be either immutable or invisible unless running limited windows desktop environment (Safe-mode or WinPE disc). IPC is crazy and no-one says anything because using PC be real hard without it... 3) Windows and File systems it is built on never really throw things away. But that cuts both ways.. However that means you could recover your docs, photos, movies and music pretty EZ with little data-rot. Test Disk (which can be used to repair disk comes bundled with PhotoRec program and its free and effective . If that doesn't work there is Adroit photo-recovery. The main thing you dont want to do is overwrite or scrub the disk with secure wipes because then you can't retrieve any MFT or artifacts. Which I suppose if I needed that to be sure my system was not compromised but once you connect to the internet or a mobile phone, thumb drive etc. You can''t be sure anymore... It'll drive you bonkers I know. I have learned to accept that however I keep my desktop disconnected, my laptop runs linux + windows and I use a phone and a usb key to authenticate when passwords aren't enough or too much... Remember that we now live in the 21st century and were bound to have crazy tech influences on us undreamt by those before.