
Update: A decryptor has been released that can recover files for victims infected prior to July 17th, 2019.
A new ransomware strain written in Go and dubbed eCh0raix by the Anomali Threat Research Team is being used in the wild to infect and encrypt documents on consumer and enterprise QNAP Network Attached Storage (NAS) devices used for backups and file storage.
Originally discovered by reports from victims in a BleepingComputer forum thread, the ransomware has been reported to target the following QNAP NAS devices: QNAP TS-231, QNAP TS-251, QNAP TS 253A, QNAP TS 253B, QNAP TS-451, and QNAP TS-459 Pro II.
According to Anomali researchers, these NAS devices are being attacked through weak credentials and by exploiting known vulnerabilities.
QNAP Systems, the manufacturer of QNAP NAS devices, provides a list of steps that could allow rannsomware victims to recover their data if the QNAP block-based snapshot feature as described HERE.
While originally named QNAP-NAS-Encrypt, Anomali named it eCh0raix ransomware after a string found within the malware's source code.
The researchers observed that even though the command and control server is located on Tor, the ransomware does not contain any Tor client to connect to it. Instead the ransomware developers created a SOCKS5 proxy that the ransomware connects to inorder to communicate with the C2.
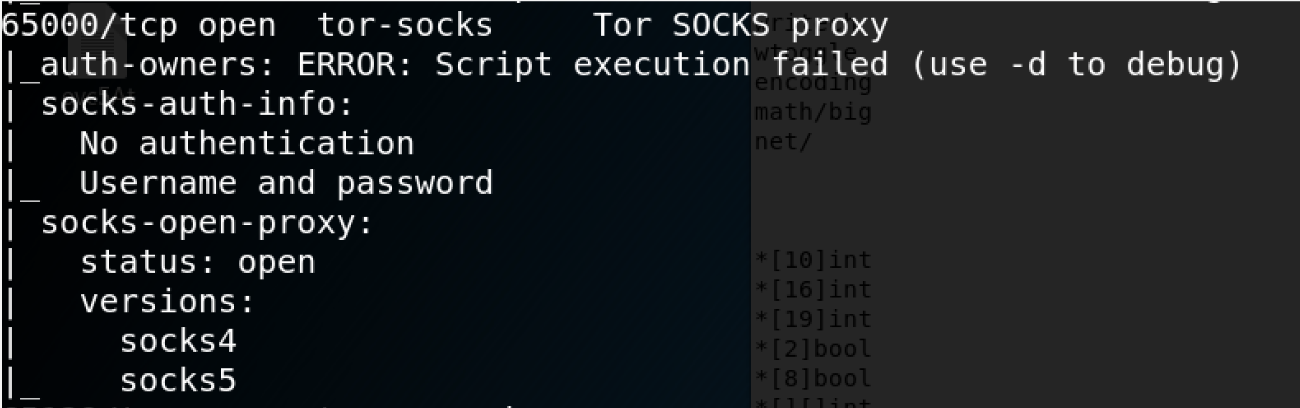
When connecting the C2 server, the ransomware will download the ransom note, a RSA public key used to encrypt the key it employs when encrypting its victims' files, and to provide the attackers with real-time insight on the malware's activity. However, while monitoring this network activity there was no system information sent to the operators to allow them to differentiate between the eCh0raix's victims.
Furthermore, the ransomware developers appear to have created an API that can be used to query for various information. For example, Anomali observed the ransomware connecting to the following URL to retrieve a public encryption key based on a campaign ID. It is not known if these IDs are associated with the ransomware developers personal campaigns or affiliates.
"One of the samples analyzed used the URL “http://sg3dwqfpnr4sl5hh[.]onion/api/GetAvailKeysByCampId/10”, that possibly suggests this was the 10th campaign run by the threat actor."
Encrypting victim's files
When executed on the NAS, the eCh0raix ransomware will perform language checks to see if the device is from certain CIS countries. If so, the ransomware will not encrypt any files.
"The sample found on C2, checks the locale of the infected NAS for Belarus, Ukraine, or Russia and exits without doing anything if a match is found," according to the researchers. "This technique is common amongst threat actors, particularly when they do not wish to infect users in their home country."
The ransomware will then search for and kill the following process on infected NAS devices using service stop %s or systemctl stop %s commands:
apache2
httpd
nginx
mysqld
mysqd
php-fpm
eCh0raix will also automatically skip files from file paths that include the following strings when searching for files to encrypt on compromised QNAP devices:
/proc
/boot/
/sys/
/run/
/dev/
/etc/
/home/httpd
/mnt/ext/opt
.system/thumbnail
.system/opt
.config
.qpkg.
As most QNAP NAS devices do not come with an active anti-malware solution, eCh0raix can freely encrypt documents on compromised systems. To make matters even worse, even on devices where an antivirus product is running in the background, the malware will very rarely be detected as proven by the very low VirusTotal detection date, with only three out of 55 malware scanning engines marking it as malicious.

The ransomware is known to encrypt Microsoft Office and OpenOffice documents, PDFs, text files, archives, databases, photos, music, video, and image files using an AES in Cipher Feedback Mode (CFB) secret key created from an AES-256 key generated locally. This AES key is then encrypted with the downloaded or embedded public RSA key and stored in base64 format in the ransom note.
When encrypting files, it will search for the following files types and append the .encrypted extension to the encrypted file's name.

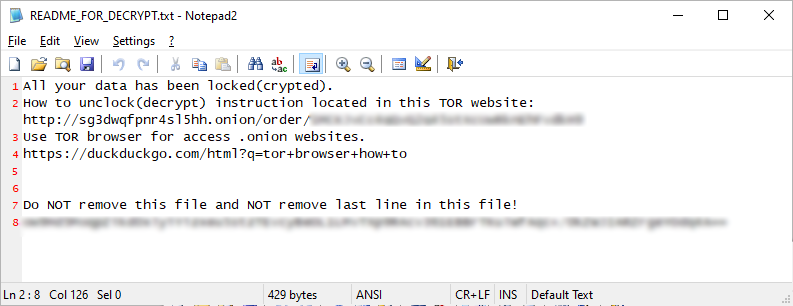
While scanning for files to encrypt, it will also create ransom notes named README_FOR_DECRYPT.txt in folders on the NAS. These ransom notes contain a link to a Tor site, an associated bitcoin address, and the users encrypted private encryption key.
If a user goes to the Tor payment site, they will be shown a bitcoin address and the ransom amount that must be sent. The Tor site will allegedly wait for the payment to go through and notify you when it has been received so that you can download the decryptor. In searches by BleepingComputer, the decryptors from the malware developers appear to be available for both Windows and macOS.
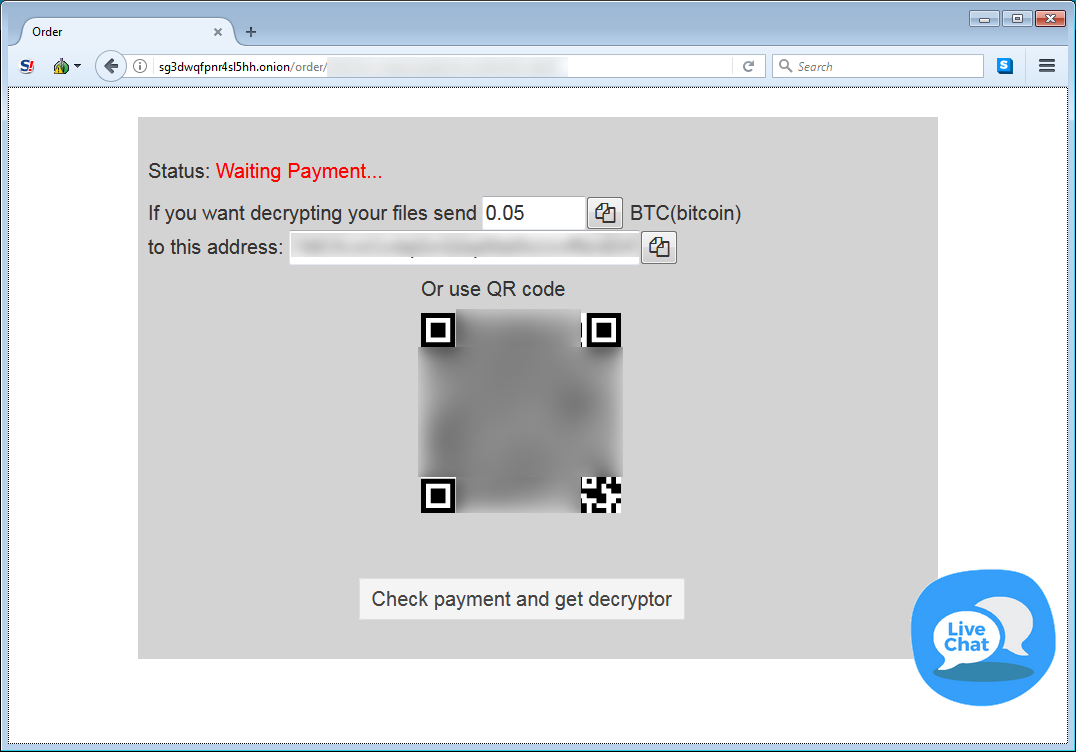
According to ransomware researcher Amigo-A, the attackers are asking for "a ransom of 0.05-0.06 BTC or more to return the files".
Decryptor not available yet
While an eCh0raix decryptor is not yet available, the Anomali Threat Research Team says that "Since it is using the math’s package to generate the secret key, it is not cryptographically random and it is likely possible to write a decryptor."
Researchers will be taking a look at this ransomware to see if it can be decrypted for free. It is advised that you do not pay the ransom or pay for recovery services until the ransomware has been adequately researched.
IOCs
Hashes:
154dea7cace3d58c0ceccb5a3b8d7e0347674a0e76daffa9fa53578c036d9357 (DE)
3d7ebe73319a3435293838296fbb86c2e920fd0ccc9169285cc2c4d7fa3f120d (TW)
95d8d99c935895b665d7da2f3409b88f ( linux_cryptor)
Associated Files:
README_FOR_DECRYPT.txt
Known Bitcoin addresses:
18C28bVEctVtVbwNytt4Uy6k7wxpysdDLH
1Fx7jev3dvHobdK8m3Jk6cA8SrfzjjLqvM
URLs:
http://sg3dwqfpnr4sl5hh[.]onion/api/GetAvailKeysByCampId/13
http://sg3dwqfpnr4sl5hh[.]onion/order/1LWqmP4oTjWS3ShfHWm1UjnvaLxfMr2kjm
http://sg3dwqfpnr4sl5hh[.]onion/static/
Associated IP addreses
192.99.206.61:65000
Yara rule:
rule eCh0raix {
meta:
author = "Anomali"
tlp = "GREEN"
description = "Rule to detect eCh0raix ransomware"
version = "1.0"
strings:
$magic = "eCh0raix"
$s0 = "go.buildid"
$s1 = "main.main"
$s2 = "makesecret"
$s3 = "chDir"
$s4 = "writemessage"
$s5 = "randSeq"
$s6 = "encrypt"
condition:
uint16(0) == 0x457f and $magic and all of ($s*)
}
Ransom Note Text:
All your data has been locked(crypted).
How to unclock(decrypt) instruction located in this TOR website: http://sg3dwqfpnr4sl5hh.onion/order/[bitcoin_address]
Use TOR browser for access .onion websites.
https://duckduckgo.com/html?q=tor+browser+how+to
Do NOT remove this file and NOT remove last line in this file!
[unique_id]









Comments
Amigo-A - 5 years ago
Still, the format of the article is constructed incorrectly.
First this Ransomware ant him attack was first discovered here on the forum on June 21, 2019. This should be written at the very beginning.
In one forum thread, victims were collected, a list of devices was compiled, sample files were presented, and the situation was described.
A description of the threat was made, the name was given, which was later corrected according to device name and extension.
Later, after 20 (!) days, an article was published by a certain Anomali, who invented a new name and ignored all preliminary work on the forum.
This threat was identified on the forum by people who are in the topic of support. Other people, from the outside, just used the situation for their own purposes.
Byzt - 5 years ago
Thanks BloodDolly to usefull tool for eCh0raix,
my client has already paid to attacker and they got the tool but it did not worked as well.
We solved this problem with BloodDolly' s eCh0raix tool
qyqyyqyq - 5 years ago
Hello, I also paid a ransom, but I couldn't unlock it. How did you solve it?
boeyretha - 3 years ago
Hi, any update for ECh0raixDecoder? it seem have new variant of Ech0raix recently.
I already use previous ECh0raixDecoder (ver. 1.0.3) but the key never found.
yannickgm - 3 years ago
Hope someone finds a solution. Just bought a TNAS from christmas and instead of safely backuping my data ending up rendering it useless. I definately hate whoever did this ....
Oscar71 - 3 years ago
I've just been caught by these ar$eholes pretty much all data on my QNAP is encrypted... strangely none of my videos are affected.
Tried BloodDolly's tool but no luck as yet.
Redbaard - 3 years ago
Same here... they've encrypted virtually every file on my QNAP also. Assholes...
jagonna - 3 years ago
Same here, just got infected few days ago (QNAP), But they encrypted only my .jpg files. All the childhood photos and my kids photos encrypted. I have a backup but it was attached to my QNAP and it is also infected. Lesson learnt, do offline backup, do not attached your backup to the network
Tried ECh0raixDecoder as well with no luck, Hope @BloodDolly comes out with an update for the latest variant of ECh0raix.
vroomzoom - 3 years ago
Adding myself to the list (QNAP). Infected a few days ago, and some file types were not affected. I am pointed to the eCh0raix order page by the README_FOR_DECRYPT.txtt
I too tried using ECh0raix Decoder 1.0.3 using the matching unencrypted/encrypted file method and multiple encrypted files method but did not find a key.
Here's to hoping we get more information soon.
medesan - 3 years ago
Adding myself to the victims list. all my pictures are encrypted with the message as shown in the article. I pm'd support from Emsisoft and they pointed me 1 file, ransom note and URL in a free ransomware detection. It brought me to this page and sadly, at the end it says no decryper available. I understand it aint easy but any timelines on when all of us can expect it to be released?
darylp - 3 years ago
me too on a network connected QNAP, 90% files are .encrypt now :-(
encrypteduser2000 - 3 years ago
I have all my jpg files infected. I hope someone can build a tool to undo this!
A79 - 3 years ago
Yes I have been impacted today 13/04/2021.
jingram1 - 3 years ago
Hi all. My TS-231 was infected a couple of weeks back. All photos now encrypted by these scumbags. Not only are files encrypted, but I also cannot login to the NAS at all via QTS. It is like the login button has been disabled. Does anyone else have the same issue. I can only 'access' the NAS via windows file manager.
I hope that someone can get a decoder created as I cannot pay the ransom.
raystdenis - 3 years ago
I got hit today 2021-04-20 on my QNAP NAS drive. I have no idea what percentage complete it was in, as I pulled the power cord as soon as I noticed the infection, so I'm hoping not everything was infected . Question: I assume if I power up the NAS it will just continue on encrypting. My router has the ability to block internet access to any specific device, so I blocked the NAS from talking to the internet. Does anyone know if the malware will continue without internet connection if I turn it back on? I'd like to at least salvage anything that didn't get hit (if any). Or is my safer bet to remove the drive and connect it with a USB adapter to my computer? Any help would be greatly appreciated.
Second question: a few files that I know were encrypted, I also have the original files as an older backup. Would knowing the before and after encryption not help in decrypting the rest of my files as I assume they are using the same hash key for the entire drive?
TommyGuns - 3 years ago
I got hit 9:30am 04-20-2021. By the time I noticed a problem it was already too late. In reaction, I forcibly shut down my TS-259 Pro.
After making firewall changes to ensure it had no outside visibility or access, I turned it back on to see what I could find, using Windows file manager to connect directly to IP address and share\directory. Nearly everything had the .encrypt extension, with a corresponding README_FOR_DECRYPT.txtt file in every directory.
I must've interrupted the process toward the end when I had forcibly shut it down because I did have some files which had not been encrypted yet. I immediately copied those off into multiple backup sets on various media. I have turned the NAS on/off multiple times now and nothing else has changed, so I am unsure if the forced shutdown killed the process entirely. If it requires any type of outside connection open to continue, it has none, so that may be end of it. Just to be sure, I've logged into QTS and disabled web interfaces, changed the default admin port, admin password, removed cloud, music, multi-media and other apps not needed. I installed Malware Remover and ran it, but it found nothing. (Very disappointing!!)
Since I was fortunate to have original and encrypted versions of the same file I, too, tried ECh0raix Decoder 1.0.3 using the matching unencrypted/encrypted file method for individual and multiple file options, but was unsuccessful.
I am currently using another computer to run the Exhaustive search method, trying to brute-force key identification using a single matched pair of original/encrypted files. It's not a very fast computer, so this will be running for a LONG time, but may eventually find a match by going through every possible combination. I am hoping BloodyDolly is able to provide an update that will assist with the current version of this problem.
I used Tor to link to the site offered in the README file...current ransom requested is 0.024 BTC, or $1277. I am not pursuing that as an option.
I will let you all know if the Exhaustive search method finds a key.
Oscar71 - 3 years ago
Has anyone paid the ransom? I hear reports that the decoder doesn't work for everyone that pays up. I really need the data on my discs... foolishly have some important documents that I need. I have noticed that almost all of my music & videos are untouched.
I've given up on QNAP now, they have only just released patches having known for the issue existed months a go.
raystdenis - 3 years ago
Update: I removed one of the NAS drives and connected it via USB to my computer. Of course because it's in Linux format, Windows can't read it. I downloaded a copy of ReclaiMe and it read the data drive just fine. Paid $200USD for a license to be able to copy any of the files off the drive. I had two shared folders: one for Business and another for Multimedia. The multimedia files (movies and 20 years of archived photos) were luckily untouched so I have all that restored to 4TB USB drive. The Business folder was not so lucky. Most were PDF files and they all got hit. At least I have all of them now archived until a solution is found.
I too tried running ECh0raix Decoder 1.0.3 for 9 hours at 10 million checks/second without success. The author mentions a 32 byte key, but I'm assuming ours is much longer. This is definitely a brand new variant since the file extension is .txtt instead of .txt, plus the bottom of the ransom file does not contain a hash key like others.
erikssongg - 3 years ago
Same here, tried Echoraix Decoder, also run the extended search for days, gave up.. I also have the .txtt note and no hash at the bottom of the note. I wish there was a way to know if the extended search is worth while or not?
steampoweredflight - 3 years ago
Infected with eCH0raix with .txtt ransom note and no hash at the bottom of the note. Echoraix Decoder did not work. Will quarantine my data and wait for a decrytpor.
Oscar71 - 3 years ago
"Will quarantine my data and wait for a decrytpor."
Good luck, I doubt a decryptor will ever be available. A friend of mine owns a security software company, he said with that level of encryption it will take a bank of GPU's to run a brute force crack many many many years. Might as well kiss your data goodbye, I've resigned myself to having lost a lot of data, some important some less so but more valuable due to being sentimental pictures