
Microsoft announced the addition of a new Windows Server 2019 feature that will enable admins to enforce Transport Layer Security (TLS) versions by blocking legacy ones via certificate binding.
"Beginning with KB4490481, Windows Server 2019 now allows you to block weak TLS versions from being used with individual certificates you designate," says Microsoft.
"We call this feature 'Disable Legacy TLS' and it effectively enforces a TLS version and cipher suite floor on any certificate you select."
Beginning with KB4490481, Windows Server 2019 now allows you to block weak TLS versions from being used with individual certificates you designate. This new "Disable Legacy TLS" feature helps make your transition to a TLS 1.2+ world easier https://t.co/SltLmQ71ct
— Microsoft Security Intelligence (@MsftSecIntel) September 30, 2019
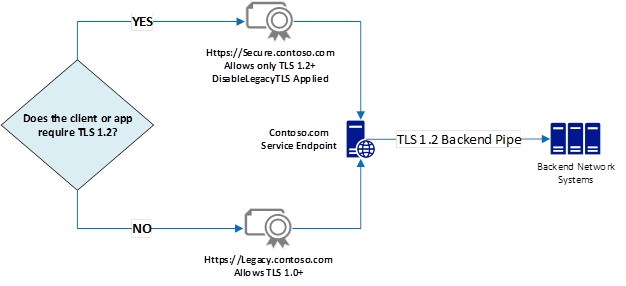
The Disable Legacy TLS feature makes it possible for services delivered locally or from online resources to offer "two distinct groupings of endpoints on the same hardware," namely one that will only allow TLS 1.2+ traffic and another one designed to also support legacy TLS 1.0 traffic.
While previously enforcing a specific TLS version would required additional hardware and they needed system-wide registry-based configuration, the new changes are implemented within HTTP.sys and will allow TLS-aware traffic routing with the help of certificates.
The new per-certificate TLS version binding in Windows Server 2019 allows admins to match the needs of customer groups that have already moved on to using TLS 1.2+ on a daily basis and the ones of clients that are still working on migrating from weaker implementations such as TLS 1.0, all without having to invest in "two physically separate hosts to handle all the traffic and provide for TLS version enforcement."
Microsoft has made changes to various other products in the past to make sure that customers are able to transition to TLS 1.2+ easier:
• by shipping new logging formats in IIS for detecting weak TLS usage by clients,
• as well as providing the latest technical guidance for eliminating TLS 1.0 dependencies.
Redmond also provides a deployment guide for the new Windows Server 2019 Disable Legacy TLS feature, allowing admins to enable it via the Internet Information Services (IIS) Server UI, via PowerShell commands, or the C++ HTTP.sys APIs, as explained in this support article.
When the Disable Legacy TLS featured is toggled on, the following restrictions will be enforced:
• Disable encryption ciphers DES, 3DES, and RC4 (so only AES is used).
• Disable encryption cipher AES with CBC chaining mode (so only AES GCM is used).
• Disable RSA key exchange.
• Disable DH key exchange with key size less than 2048.
• Disable ECDH key exchanges with key size less than 224.
Microsoft previously stated, in a coordinated announcement with Google, Apple, and Mozilla, that they will be retiring the TLS 1.0 and TLS 1.1 secure communication protocols beginning with the first half of 2020.
TLS is a protocol used for encrypting the communication channels between websites and web browsers, with the original TLS 1.0 specification and the TLS 1.1 successor having been in use for the last 20 years or so.
However, browsers are now switching to the more secure TLS 1.2 and TLS 1.3 specs that also come with support for newer protocols such as the HTTP/2 and HTTP/3 network protocols, which can greatly increase the browsing speed.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now