
An unknown Chinese-speaking threat actor has been targeting betting companies in Taiwan, Hong Kong, and the Philippines, leveraging a vulnerability in WPS Office to plant a backdoor on the targeted systems.
The adversary appears to be sophisticated, and its toolset features code similarities to APT group backdoors analyzed in two 2015 and 2017 reports by Palo Alto and BlackBerry, respectively.
The newest campaign was spotted by researchers at Avast, who have sampled several malware tools from the threat actors, who have compiled a rich, modular toolset.
Targeting a WPS Office flaw
The first infection vector used in this campaign is an email with a laced installer that pretends to be a critical WPS Office update, but in most attacks, the threat actors use a different method.
The second infection vector, which is predominately used in this campaign, is leveraging CVE-2022-24934, a vulnerability in the WPS Office updater utility.
WPS Office (formerly Kingsoft Office) is a cross-platform office suite with over 1.2 billion installations. Its use is prevalent in Hong Kong and China because it is historically the first word processor to support the Chinese language.
Exploit of CVE-2022-24934 leads to establishing a communication channel with the C2, fetching additional payloads, and running code on the compromised machine.
.png)
“To exploit the vulnerability, a registry key under HKEY_CURRENT_USER needs to be modified, and by doing this an attacker gains persistence on the system and control over the update process,” explains Avast in its technical report.
Avast informed the software vendor about the vulnerability, which enables the actors to execute code arbitrarily, and although a patch has been issued, not everyone has applied the security update yet.
Rich and intricate toolset
The first-stage payloads planted into the compromised system include a DLL backdoor for C2 communication and a dropper that elevates privileges on the system. The latter fetches eight payloads that fulfill various functional roles.
In the second stage, the core module, “Proto8,” is loaded onto the compromised system, and a four-step cascading structure unfolds.
- Performs initial checks and establishes evasion mechanisms.
- Module self-updates, loads configuration files, and sets up its working directory.
- Collects info like username, DNS, NetBios computer name, OS, architecture, and preloads call functions.
- Validate hardcoded C2 addresses and attempt to reach the actor-controlled server.
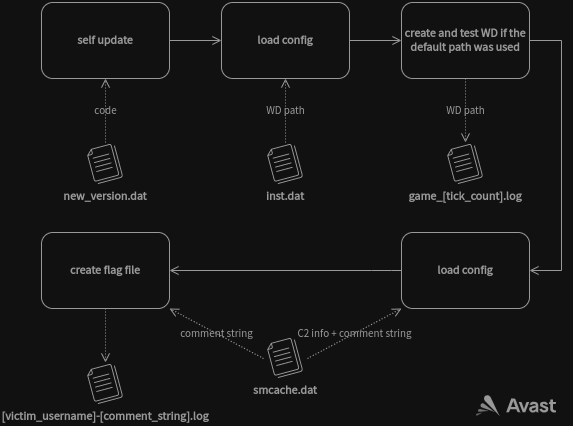
Once the above is done, the core module waits for remote commands to arrive, which can be one of the following:
- Send collected data to C2 server
- Find username, domain name, and computer name of all Remote Desktop sessions
- Enumerate root disks
- Enumerate files and find access and creation details
- Create a process with a stolen, duplicated token
- Rename files
- Delete files
- Create a directory
- Send error code via an API function
- Enumerate files on a specific folder
- Upload a file to the C2 server
- Create a directory to host files downloaded from the C2
Proto8 also features a plugin loading system, with each add-on offering various functions relating to persistence, bypassing UAC, offering backdoor capabilities, evasion, etc.
One of these plugins carries out registry manipulation to create a new user account that is then abused to establish RDP connections to the machine without having an admin password.
That plugin enables anonymous SID to be part of the everyone group in Windows, allows “Null Session” users to access shared network folders, and disables admin approval requirements to make all apps run with full privileges.
Murky campaign goals
While Avast hasn’t attributed this campaign to any known actors, they believe it is the work of a Chinese APT either looking to gather intelligence or achieve financial gains.
Considering the nature of the targets, which is betting companies, the goal of the threat actors may have been to steal financial details or take over accounts and cash out escrow balances.
The tactics and the powerful toolset used in the campaign reflect a skillful adversary, so not being able to make attributions with high confidence is somewhat expected.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now