Microsoft has fixed a bug that could allow a threat actor to create specially crafted downloads that crash Windows 10 simply by opening the folder where they are downloaded.
Last month, we reported on a bug in the Windows 10 console multiplexer driver, condrv.sys, that caused a blue screen of death crash (BSOD) when attempting to connect to the following path.
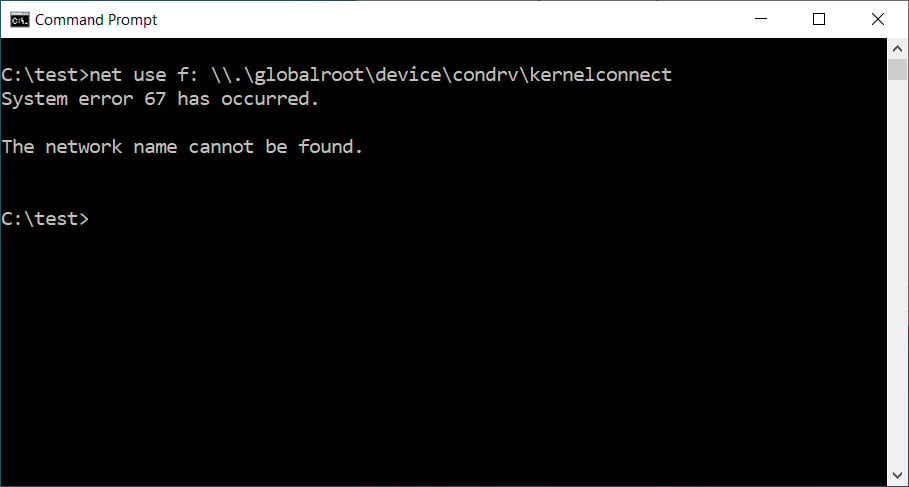
\\.\globalroot\device\condrv\kernelconnect
When connecting to the device, developers are meant to pass the 'attach' extended attribute. However, a lack of error checking allowed you to access the path without the attribute and crash Windows.
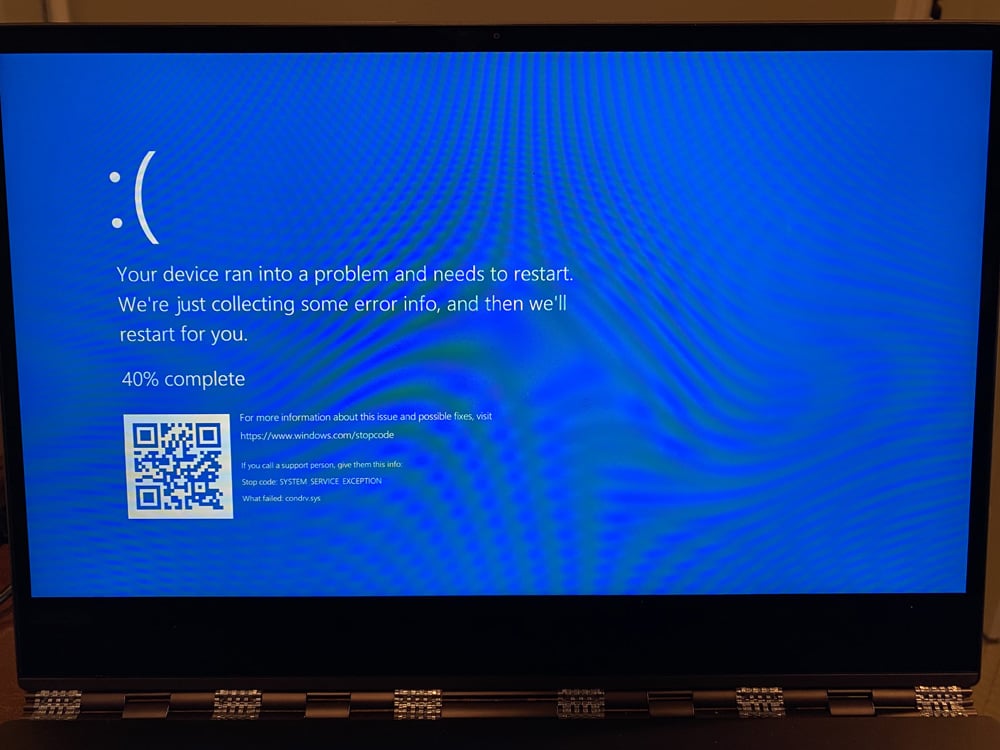
This bug opened up a myriad of potential methods to crash Windows, including accessing the path from a browser's address bar, trying to assign it to a drive letter using 'net use,' or creating a specially crafted URL file that sets its icon to the path.
Even worse, threat actors who gain access to a system can use it to force a crash of a breached system to hide their activities.
As part of the February 2021 Patch Tuesday, Microsoft has fixed this bug and tracking it as CVE-2021-24098, with a description of 'Windows Console Driver Denial of Service Vulnerability.'
Microsoft's FAQ for the vulnerability explains how threat actors can exploit the bug.
"In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) that contains a specially crafted file that is designed to exploit the vulnerability. However, an attacker would have no way to force the user to visit the website."
"Instead, an attacker would have to convince the user to click a link, typically by way of an enticement in an email or Instant Messenger message, and then convince the user to open the specially crafted file," explains Microsoft's CVE-2021-24098 vulnerability page.
After installing the update, BleepingComputer can confirm that the bug can no longer be exploited. For example, when we attempted to assign the path to the f: drive using the 'net use' command, Windows 10 no longer crashes.
BleepingComputer strongly recommends that Windows 10 users install the latest Windows 10 updates to fix this bug. This is even more important, considering the large amount of publicly disclosed vulnerabilities fixed in February 2021's Patch Tuesday.









Comments
DentonPowell72 - 3 years ago
Awesome info! Thanks as always!