
The authors behind LokiBot info-stealer have turned to steganography to add a new layer of obfuscation, the researchers discovered in a recent variant of the malware.
LokiBot is currently under active development, with developers adding a bundle of features over the years. It is a popular choice with the Nigerian-based business email compromise (BEC) group called SilverTerrier.
It can steal browser information from over 25 different products, check for remote administration tools (SSH, VNC, RDP), and find credentials for email and file transfer clients.
Researchers at Trend Micro discovered that new strains of LokiBot use image files to hide code needed for its unpacking routine.
The analysis showed that the image hosted the encrypted binary the malware needs for different unpacking stages, which lead to LokBot being decrypted in the RAM of the infected system.
"Before loading the main code, it creates a directory in %appdatalocal% where the Loki binary and the image (same as those in %temp%) will be placed." - Trend Micro
To decrypt the binary, LokiBot searches for the marker that indicates the beginning of the file stored inside the image. The result of the decryption is then loaded during the various unpacking stages.
Analysis of the malware shows that the developer implemented their own decryption method instead of relying on a common block cipher like AES.
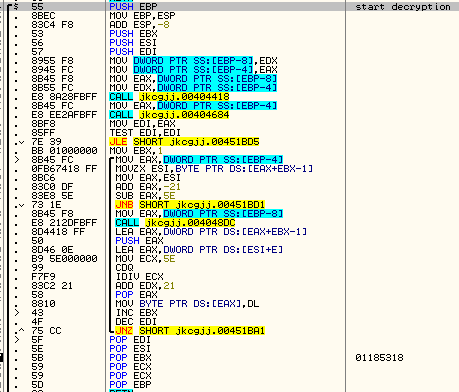
The researchers note that this strategy not only enables LokiBot to evade detection but also helps it with persistence on the compromised machine.
Executing the malware is possible with the help of a Visual Basic script, deployed by the VBS file interpreter - 'wscript.' At this moment an autostart registry is created, which points to the VB script.
A peculiarity the analysts observed in this variant is that the autostart registry entries are broken as it gets overwritten. This also happens with other samples studied by the researchers.
Although using steganography this particular way is a novelty in LokiBot, the updates are not as extensive as in other variants discovered in the past.









Comments
Morality - 5 years ago
Is this a variant of the android banking trojan?