
Security researchers analyzing a phishing campaign targeting Russian officials found evidence that points to the China-based threat actor tracked as Mustang Panda (also known as HoneyMyte and Bronze President).
The threat group was previously seen orchestrating intelligence collection campaigns against European targets, employing phishing lures inspired by the Russian invasion of Ukraine.
Russia has always remained in the threat group's crosshair, albeit at a limited scale, as the two countries generally maintain good geopolitical relationships.
In a report today, cybersecurity company Secureworks presents new evidence of such targeting, which may not be as limited as previously thought.
Phishing Russian officials
The threat actors employ phishing lures that rely on English documents supposedly released by the European Union, containing sanction details against Belarus.

Although the files sent are Windows executables (.exe), they are made to appear as PDFs and are named after a Russian city close to the border with China, Blagoveshchensk.
This suggests that the targets of this campaign are Russian personnel in the region, which further supports the theory that China may be shifting to new intelligence gathering objectives.
Upon launching the executable, a host of additional files are fetched, including the previously mentioned decoy EU document, a malicious DLL loader, an encrypted PlugX variant, and a digitally signed .EXE file.
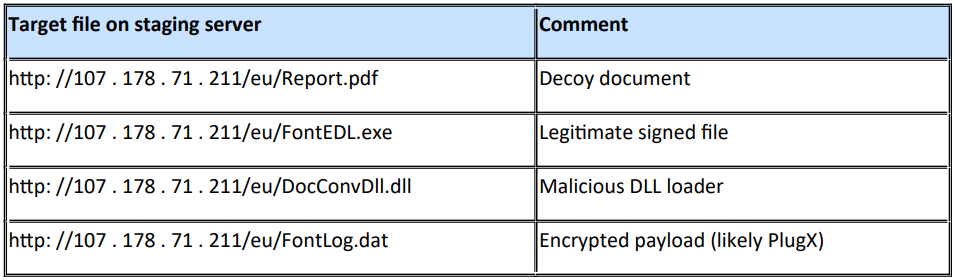
Loading PlugX
The DLL loader performs DLL search order hijacking using a legitimate signed file (from UK-based Global Graphics Software Ltd) that is vulnerable to this trick. The method s typical to Mustang Panda, used to execute the PlugX malware payload.
This approach allows threat actors to load their malicious DocConvDll.dll DLL loader in a stealthy manner that does not trigger security solutions on the system.
The DLL loader exports eight functions but only one of them comes with relevant instructions. It appears that this is to evade automatic analysis.
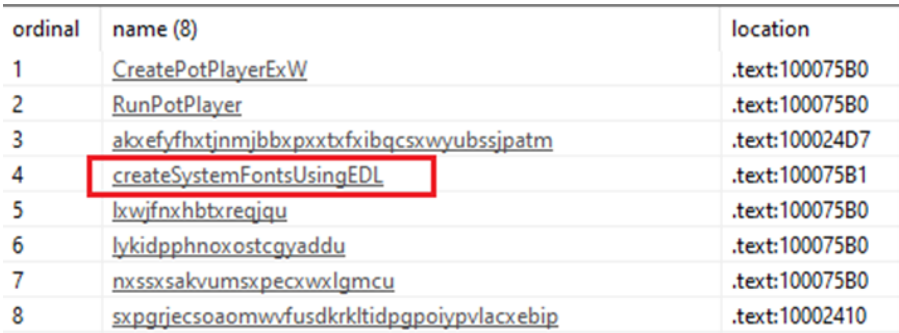
The 'createSystemFontsUsingEDL' function loads, decrypts, and executes the FontLog.dat file, which is the PlugX payload.
Although the PlugX sample analyzed by Secureworks was corrupted, its code points to DLL side-loading and malware execution from within a newly created directory, at "C:\ProgramData\Fuji Xerox\Fonts\".
The staging server used in this campaign is the same that supported the EU diplomats campaign, also hosting the zyber-i[.]com domain that was implicated in that operation.
It is worth noting that PlugX has been used by so many adversaries that attribution based on this malware is impossible.
However, Secureworks connected this campaign to Bronze President/Mustang Panda based on the infrastructure used, which has been attributed to this particular actor in the past.
Outlook
Although Mustang Panda continues deploying the same malware strains and loader tools, and even though parts of its infrastructure overlap with past campaigns, the threat actor remains relatively stealthy and potent.
Its focus appears to be refreshing the spear-phishing lures and crafting specialized email messages for very narrow targeting operations, so the intelligence collection is constantly shifting.
For now, using the provided indicators of compromise for email and network defense would render most of the threat actor's infection attempts ineffective.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now