
The US government is taking steps to fix the Common Vulnerabilities and Exposures (CVE) system that's been plagued by various problems in recent years.
The CVE was created in 1999 by the MITRE Corporation using US government funding. It is a database that contains identifiers (tracking numbers) for security vulnerabilities.
Since its creation, the CVE system has been adopted by the public and private sectors. Most modern cyber-security software use CVE numbers to identify and track cyber-attacks exploiting particular software bugs.
Despite being a US creation, the system has been widely adopted in countries all over the globe, which use and recognize the CVE identifiers issued by MITRE's staff and industry partners.
CVE database has been plagued by various problems
But in recent years, the CVE system has been under stress. Its problems became evident in late 2015 and early 2016 when a large number of security researchers reported huge delays in receiving CVE numbers for the vulnerabilities they reported [1, 2, 3]. At one point, a few of them united to create an alternative vulnerabilities database known as the Distributed Weakness Filing (DWF).
At the time, MITRE said the CVE number assignment delays were caused by the increased number of software vendors, compared to the late 90s and early 2000s, but also because of the proliferation of software-driven industrial (SCADA) equipment and Internet of Things (IoT) devices.
Both factors contributed to a huge rise in vulnerability reports, with which the CVE staff wasn't managing to keep up. A late 2016 report found that MITRE's CVE failed to assign CVE numbers to over 6,000 vulnerabilities discovered in 2015.
US Senate starts investigating the CVE program in 2017
Following the media reports cited above, the US Senate's Energy and Commerce Committee started an investigation into the CVE program in late March 2017.
The Senate has the power to investigate the running of the CVE program because MITRE receives funding for running the CVE database from the National Cyber Security Division of the United States Department of Homeland Security.
On Monday, following a year-long investigation into the CVE program, the Energy and Commerce Committee sent letters to the Department of Homeland Security (DHS) and MITRE Corporation.
In these letters, the Committee outlined the investigation's findings and proposed courses of action to fix the issues found with the CVE system.
Cause #1: Fluctuating and diminishing funding
According to the two letters, the Committee says it identified that inconsistent and largely diminishing DHS funding as one of the reasons the program has gone downhill and accumulated its huge backlogs.
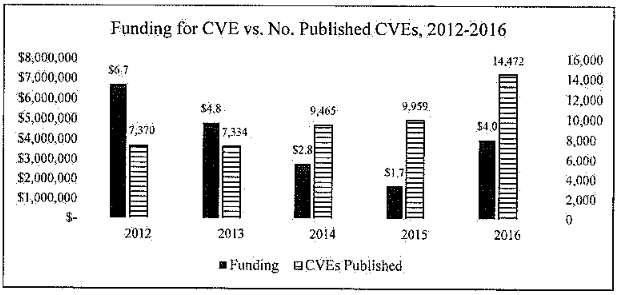
"From 2012 to 2015, the program has received on average 37 percent less year-over-year funding," the Committee writes in letters sent to both the DHS and MITRE.
"The documentation produced by DHS and MITRE shows that the CVE contract vehicle is both unstable and prone to acute fluctuations in schedule and funding," the letters added.
To solve this issue, the Committee proposes that DHS officials move CVE's funding from a contract-based funding scheme into the DHS budget itself, as a PPA (Program, Project, or Activity) funding line.
The Committee believes this would provide a constant stream of funding, reducing huge budget fluctuations, and keeping MITRE focused on running the CVE database instead of always worrying about its future funds.
Cause #2: Lack of oversight
Second, the Committee also identified a second source of problems, which was the lack of oversight for the CVE program.
"The historical practices for managing the CVE program are clearly insufficient. Barring significant improvements, they will likely lead again to challenges that have direct, negative impacts on stakeholders across society," the letters read.
The Committee suggests that DHS and MITRE perform biennial reviews to ensure the program's stability and effectiveness for the years to come. The role of these reviews will be to spot problems before they heighten to the point of where they trickle down into the downstream cyber-security industry.
The letters sent to the DHS and MITRE's CEO are available here and here, respectively.









Comments
GT500 - 6 years ago
Typical government... Declare that to solve the problem, the program needs more funds, and then also recommend that the program waste those funds with periodic "reviews" when the program is already managed by people who could have reported issues and probably weren't being listened to in the first place...