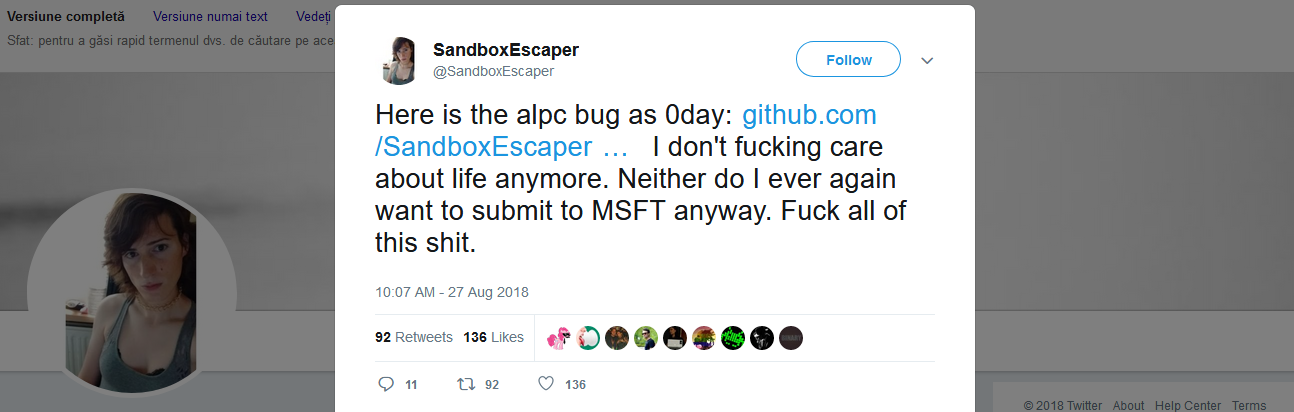
A security researcher has published on Twitter details about a vulnerability in the Windows OS.
The vulnerability is a "local privilege escalation" issue that allows an attacker to elevate the access of malicious code from a limited USER role to an all-access SYSTEM account.
Will Dormann, an engineer of CERT/CC, has confirmed the vulnerability and has issued an official CERT/CC alert last night.
Dormann says the vulnerability resides in the Windows Task Scheduler, and more precisely in the Advanced Local Procedure Call (ALPC) interface.
The ALPC interface is a Windows-internal mechanism that works as an inter-process communication system. ALPC enables a client process running within the OS to ask a server process running within the same OS to provide some information or perform some action.
The researcher, who goes online by the name of SandboxEscaper, has released proof-of-concept (PoC) code on GitHub for exploiting the ALPC interface to gain SYSTEM access on a Windows system.
Malware authors will particularly be interested in this PoC, as it allows benign malware to gain admin access on targeted systems using an exploit more reliable than many existing methods.
SandboxEscaper has not notified Microsoft about the vulnerability, meaning there is no patch for this flaw. Currently, all Windows 64-bit users are vulnerable.
Microsoft's next security updates are scheduled for September 11, the date of the company's next Patch Tuesday.









Comments
RuudHanegraaf - 6 years ago
"... benign malware ..."
Is there such a thing? ;-)
afbach - 6 years ago
The exploit has been removed from the github link