A security researcher has found a way to bypass the "Controlled Folder Access" feature added in Windows 10 in October 2017, which Microsoft has touted as a reliable anti-ransomware defensive measure.
This feature, described in more depth in this Bleeping Computer review, is part of the Windows Defender antivirus built into all versions of Windows 10.
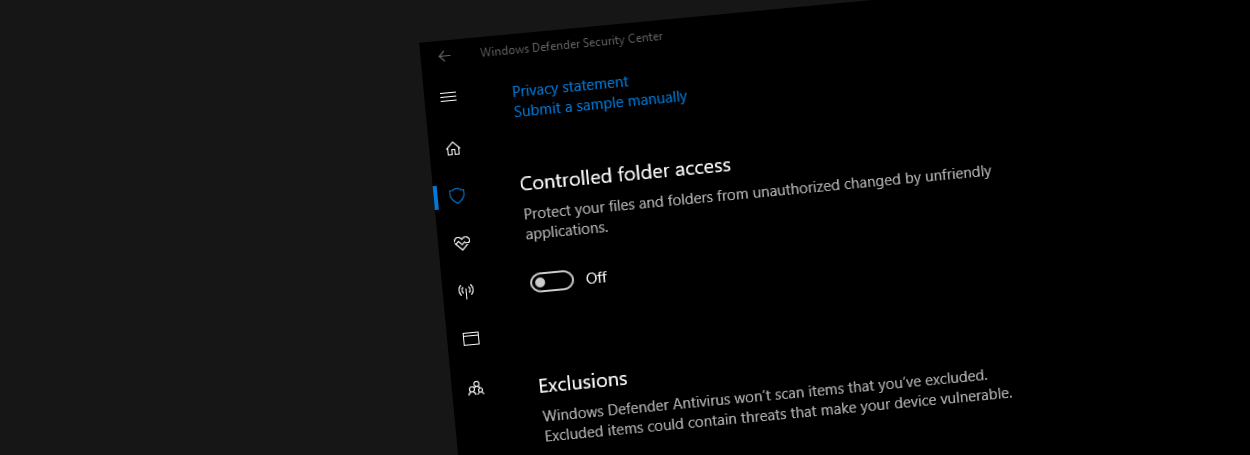
Users who updated to the Windows 10 Fall Creators Update received an update for Windows Defender named Controlled Folder Access (CFA) that allows them to block any modifications to files found in user-designated directories.
The user must manually approve any app that's allowed to edit files located in CFA folders by adding each app's executable to a whitelist managed through the "Allow an app through Controlled folder access" option.
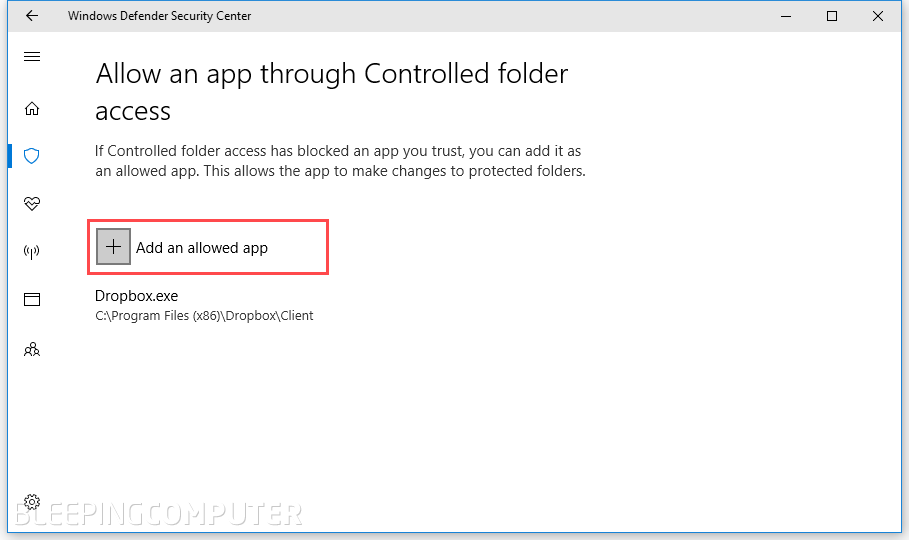
But Yago Jesus, a Spanish security researcher with SecurityByDefault, has discovered that Microsoft has automatically whitelisted all Office apps on this list. This means that Office apps can modify files located in a CFA folder, either the user likes it or not.
Ransomware can use Office OLE objects to bypass CFA
Jesus says that a ransomware developer could easily bypass Microsoft CFA anti-ransomware feature by adding simple scripts that bypass CFA via OLE objects inside Office files.
In research published over the weekend, Jesus includes three examples that utilize boobytrapped Office documents (received via spam email) to overwrite the content of other Office documents stored inside CFA folders; password-protect the same files; or copy-paste their content inside files located outside the CFA folder, encrypt those, and delete the originals.
While the first example is just destructive, the last two will work as an actual ransom, with victims having to pay the ransomware author for the password/decryption code that unlocks the files.
Jesus displeased with Microsoft
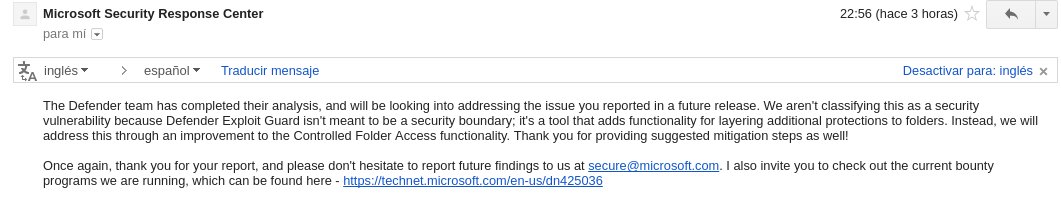
Jesus said he notified Microsoft about the issue he discovered. In a screenshot of the email he received from Microsoft, Jesus said the OS maker didn't classify the issue as a security vulnerability but said it would improve CFA in future releases to address the reported bypass method.
"That really means Microsoft will fix the vulnerability that should be classified as Mitigation bypass without acknowledgment," said Jesus, referring to the fact that he'll get no credit or bug bounty reward for the issue he pointed out.









Comments
GT500 - 6 years ago
Did anyone else giggle when they read "Jesus displeased with Microsoft"?
Count_nibbles - 6 years ago
Yes.
BeckoningChasm - 6 years ago
Very much so.