
Relying on computer memory's remanence behavior, security researchers figured out a way to extract sensitive data from RAM, such as encryption keys, even after the loss of power.
The attack subscribes to the cold-boot category and exploits a weakness in how the computers protect the low-level software responsible for interacting with the RAM.
Known for its volatility in data retention when out of power, RAM (Random Access Memory) can preserve information for a longer time - even minutes, under low-temperature conditions.
Early protection against cold-boot attacks
The first cold-boot attack was developed a decade ago. This type of side-channel compromise require physical access to the computer and this makes it practical against high-value targets rather than regular users. Even so, computer makers have implemented safeguards against it.
Trusted Computing Group, a consortium formed by AMD, Hewlett-Packard, IBM, Intel, and Microsoft, decided to protect computers against this threat vector by overwriting RAM contents when the power came back.
The specification is called TCG Reset Attack Mitigation or MORLock (Memory Overwrite Request Control).
This way, all information in memory would disappear when the system booted, even if the attacker acted sufficiently quick to create the low-temperature conditions necessary to maintain the data in memory.
Game over for MorLock
Security researchers Olle Segerdahl and Pasi Saarinen of F-Secure found a way to reprogram the non-volatile part of the memory chip that stores the overwrite instruction; thus, they were able to disable this action and enable booting from an external device (USB stick) to extract and analyze the data available in RAM.
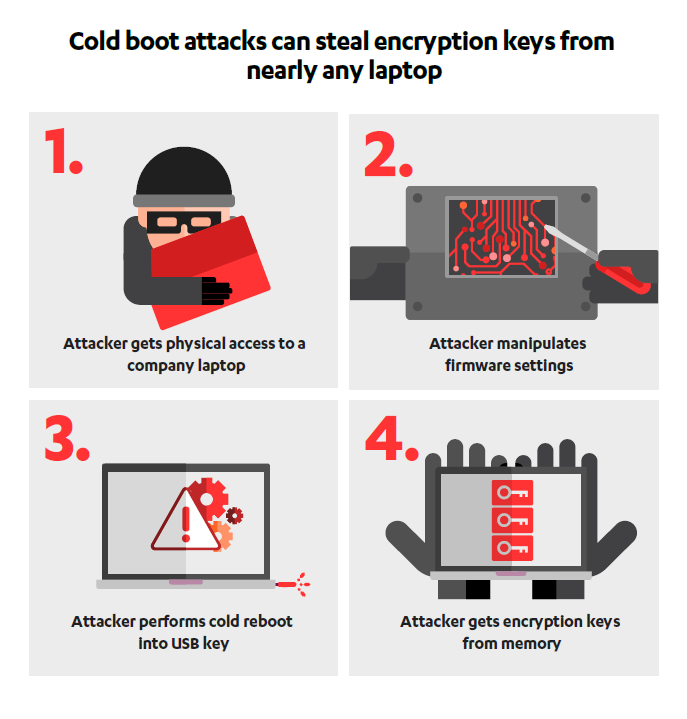
Their attack works on computers in sleep mode, since shut down and hibernation actions cut off the power, and cause the residual memory to quickly degrade beyond recovery.
When in sleep mode, the computer state is saved in RAM, which runs in a minimum power state to hold the data.
Two minutes is more than enough to get the passwords
The two researchers demonstrated the new cold-boot attack in a video, showing that a prepared adversary can execute the attack in less than two minutes:
The critical interval is between powering down the machine and starting it again. Freezing the RAM chips, though, helps preserve the data during this time, allowing booting into a live operating system from a USB stick.
The technique can steal the data in the computer memory, including hard drive encryption keys.
In the case of BitLocker, if it is configured for pre-boot authentication with a PIN, the attack has only one shot to be successful because the code is mandatory for extracting the encryption keys into the RAM.
The researchers say that their attack is reliable on Windows machines that are already running or do not require a PIN.
"It’s not exactly easy to do, but it’s not a hard enough issue to find and exploit for us to ignore the probability that some attackers have already figured this out,” says Olle Segerdahl.
He added that it is not practical on easy targets, but it would be on an attacker's list of options for a "bigger phish, like a bank or large enterprise.”
Defending against the attack
The top recommendation from the experts is to configure laptops to shut down or hibernate instead of entering sleep mode. Mixing pre-boot authentication in makes the defense even stronger.
Hibernation + pre-boot authentication is the best protection against cold boot attacks. No keys in memory to steal!
— olle@nxs.se (@nxsolle) September 4, 2018
To protect its users, Microsoft updated their documentation on Bitlocker, which now warns that the MOR bit implementation is not resilient to physical attacks. A full set of countermeasures is available here.
Apple responded by pointing to the latest generation of Macs, which have the T2 chip that does the encryption separately from the CPU and makes such an attack more difficult to execute.
The two researchers presented the attack today at SEC-T security conference, where they shared the technical details. Their talk, called "An Ice-Cold Boot to Break Bitlocker," is available below, courtesy of SEC-T conference organizers:
The organizers also prepared a video with the post-talk interview session where the two researchers provide more details about the attack, methods to bypass security implementations, such as booting a USB stick on systems with Secure Boot enabled. and the possible directions for extending it to other hardware pieces:
Update: Sec-T organizers were kind enough to let BleepingComputer know they would replace the live stream initially embedded into this article with individual videos of each talk. We have updated the article to include the permanent links for both the talk and the interview session.









Comments
NickAu - 6 years ago
Interesting article I love reading about this sort of stuff, And an interesting experiment that may affect about 50 people world wide maybe.
I really stopped paying attention after I saw " Attacker gets physical access to laptop"
JohnnyJammer - 6 years ago
Think of government laptops, both fed an state or even the army and some lazy junior IT who cant be bothered pulling the ram sticks out etc and ou go and buy a pallet load and then start running this.
Hell even mum or dads laptop which has CC info and or other info you can use to do identity fraud.
Whalley_World - 4 years ago
I've had intermittent problems with SecureBoot and HP SureStart, where it causes our systems to hang forever. The only way around this has been to disable those options in the BIOS, but I really don't like turning off security features on school district computers; of course, school kids would never cause any mischief with a computer, but...you know...