
Black Basta is the latest ransomware gang to add support for encrypting VMware ESXi virtual machines (VMs) running on enterprise Linux servers.
Most ransomware groups are now focusing their attacks on ESXi VMs since this tactic aligns with their enterprise targeting. It also makes it possible to take advantage of faster encryption of multiple servers with a single command.
Encrypting VMs makes sense since many companies have recently migrated to virtual machines as they allow for easier device management and a lot more efficient resource usage.
Another ransomware gang targeting ESXi servers
In a new report, Uptycs Threat Research analysts revealed that they spotted new Black Basta ransomware binaries specifically targeting VMWare ESXi servers.
Linux ransomware encryptors are nothing new, and BleepingComputer has been reporting on similar encryptors released by multiple other gangs, including LockBit, HelloKitty, BlackMatter, REvil, AvosLocker, RansomEXX, and Hive.
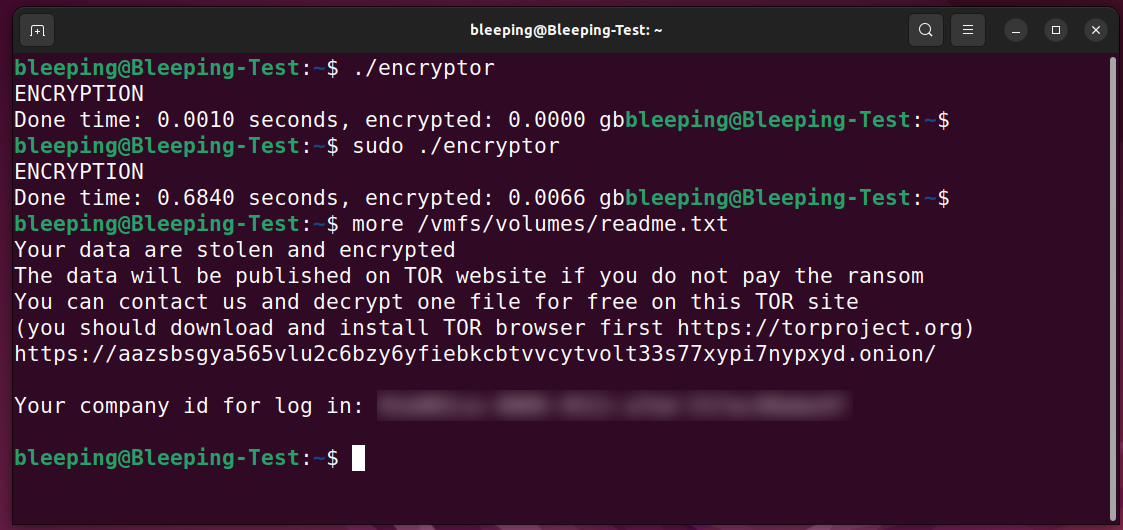
Like other Linux encryptors, Black Basta's ransomware binary will search for the /vmfs/volumes where the virtual machines are stored on the compromised ESXi servers (if no such folders are found, the ransomware exits).
BleepingComputer was unable to find command-line arguments to target other paths for encryption, suggesting that this encryptor is specifically designed to target only ESXi servers.
The ransomware uses the ChaCha20 algorithm to encrypt the files. It also takes advantage of multithreading to use multiple processors and speed up the encryption process.
While encrypting, the ransomware will append the .basta extension to the encrypted files' names and create ransom notes named readme.txt in each folder.
The notes include a link to the chat support panel and a unique ID that victims can use to communicate with the attackers.
"The Black Basta was first seen this year during the month of April, in which its variants targeted Windows systems," Uptcys' Siddharth Sharma and Nischay Hegde said.
"Based on the chat support link and encrypted file extension, we believe that the actors behind this campaign are the same who targeted Windows systems earlier with the Black Basta ransomware."
Active since April
Black Basta ransomware was first spotted in the wild in the second week of April, as the operation quickly ramped up its attacks targeting companies worldwide.
Even though the gang's ransom demands are likely to vary between victims, BleepingComputer knows of at least one who received a demand of over $2 million for a decryptor and to avoid having its data leaked online.
While not much else is known about the new ransomware gang, this is likely not a new operation but rather a rebrand due to their demonstrated ability to quickly breach new victims and the negotiating style (possibly a rebrand of the Conti ransomware operation).
Emsisoft CTO Fabian Wosar has previously told BleepingComputer that other ransomware gangs (besides the ones we reported on), including Babuk, RansomExx/Defray, Mespinoza, GoGoogle, Snatch, PureLocker, and DarkSide, have also developed and used their own Linux encryptors.
"The reason why most ransomware groups implemented a Linux-based version of their ransomware is to target ESXi specifically," Wosar explained.









Comments
r0bbienz - 2 years ago
Is keeping SSH and console shell off enough to defend against one of these?