
The Knauf Group has announced it has been the target of a cyberattack that has disrupted its business operations, forcing its global IT team to shut down all IT systems to isolate the incident.
The cyberattack took place on the night of June 29, and at the time of writing this, Knauf is still in the process of forensic investigation, incident response, and remediation.
“We are currently working heavily to mitigate the impact to our customers and partners – as well as to plan a safe recovery. However, we apologize for any inconvenience or delays in our delivery processes, that may occur,” reads the short announcement posted on Knauf’s main page.
Emails seen by BleepingComputer warned that email systems were shut down as part of the response to the attack but that mobile phones and Microsoft Teams were still working for communication.
Knauf is a German-based multinational building and construction materials producer that holds approximately 81% of the world’s wallboard market.
The firm operates 150 production sites in several countries worldwide and owns U.S.-based Knauf Insulation and USG Corporation.
Notably, Knauf Insulation has also posted a notice about the cyberattack on its site, so that entity has been impacted too.
Black Basta claimed responsibility
While Knauf’s announcements doesn't explain the type of cyberattack they suffered, the extended duration, impact, and difficulty in restoring the IT systems point to a ransomware incident.
Indeed, the ransomware gang known as Black Basta has taken responsibility for the attack via an announcement on their extortion site, listing Knauf as a victim on July 16, 2022.
The ransomware gang has published 20% of the files they allegedly exfiltrated during the attack on Knauf, which over 350 visitors have accessed.
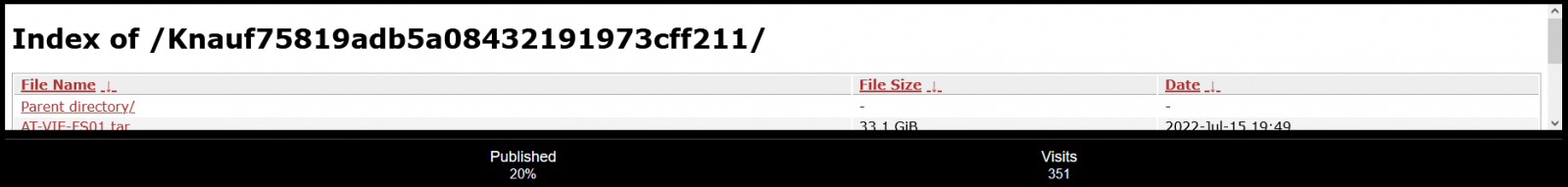
Bleeping Computer has seen samples of email communication, user credentials, employee contact information, production documents, and ID scans.
The fact that not all files have been leaked online yet indicates that the threat actors still have hope of a successful negotiation outcome and receiving a ransom payment.
The Black Basta rise
The Black Basta ransomware gang launched its RaaS operation in April 2022 and quickly assumed high notoriety status in the double-extortion space with high-profile victims.
Due to showcasing knowledge and capability early on and similarities in the negotiation style, many experts in the field assumed that Black Basta was a rebrand of Conti.
By June 2022, Black Basta had established a payload delivery cooperation with the Qbot (QuakBot) operators, also used for dropping Cobalt Strike and aiding lateral network movement.
At the same time, the authors of the new ransomware strain created a Linux version that targeted VMware ESXi virtual machines running on Linux servers.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now