-
Ransomware Decryptors Released for Yatron, WannaCryFake, & FortuneCrypt
Security vendors released decryptors for three ransomware infections today that allow victims to recover their files for free. These decryptors are for the WannaCryFake, Yatron, and FortuneCrypt Ransomware infections.
- September 25, 2019
- 03:05 PM
 0
0
-
The Week in Ransomware - January 4th 2019 - IPMI, FilesLocker, and More
For the past two weeks, we have seen a lot of new variants, decryptors, and Ryuk ransomware outbreaks. Of particular interest is the JungleSec ransomware, which has been hacking into servers via IPMI in order to install the ransomware.
- January 04, 2019
- 05:52 PM
 0
0
-
Sponsored Content

Free shadow SaaS inventory + security insightsDiscover all SaaS accounts ever created by anyone in your org, in minutes, along with insights on security risks and spend. Save time, money and effort by curbing SaaS sprawl and automating tasks like offboarding and user access reviews. Free trial.
-
The Week in Ransomware - December 21st 2018 - No More Ransom
Slow week with ransomware news as we lead up into the holidays. Mostly small variants that won't get much distribution or releases of new variants of older ransomware.
- December 21, 2018
- 04:01 PM
 1
1
-
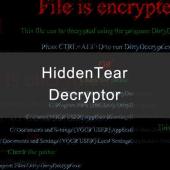
How to Decrypt HiddenTear Ransomware Variants
If you have been infected with a HiddenTear Ransomware variant, then you are in luck as a program called HiddenTearDecrypter has been created by Michael Gillespie that allows you recover your encryption key without having to pay the ransom.
- December 16, 2018
- 06:05 PM
 4
4
-
The Week in Ransomware - September 21st 2018 - Beer, Airports, & Dharma
This has been a busy week. We had a brewery hit, an airport's flight and arrival time displays taken out, and Dharma deciding to release three different variants in one week. The NSA CodeBreaker Challenge was also kicked off today and it has a ransomware theme this year.
- September 21, 2018
- 06:50 PM
 0
0
-
The Week in Ransomware - July 13th 2018 - CoinVault Court Case & More
This week has mostly been small variants released, with a bunch of new Scarab Ransomware variants. The most interesting ransomware news this week are the CoinVault authors being in a Netherlands court in front of a three-judge panel.
- July 13, 2018
- 11:56 AM
 2
2
-
The Week in Ransomware - June 22nd 2018 - Scarab Everywhere!
This has been the week of the Scarab with a continuous stream of Scarab Ransomware variants being released. We also had a few decryptors and some smaller variants, but by far Scarab dominated the ransomware distribution. Thankfully, under certain conditions Scarab can be decrypted by Dr. Web,
- June 22, 2018
- 05:12 PM
 1
1
-
The Week in Ransomware - June 1st 2018 - From Russia with Love and a Facepalm
This was a busy week with lot's of new variants of active ransomware being released. We also have Sigrun offering free decryption to Russian victims and a awesome facepalm waiting for you at the end of the article.
- June 01, 2018
- 02:38 PM
 2
2
-
The Week in Ransomware - March 2nd 2018 - GandCrab Decrypted, RaaS, and More
This week's article combines the previous week's stories as well. Lots of small in-dev ransomware over the last two weeks, but also a few RaaS (Ransomware as a Service) implementations were released and decryptor for GandCrab was released.
- March 02, 2018
- 12:49 PM
 0
0
-
The Week in Ransomware - February 2nd 2018 - TOR Sites Stealing Ransom Payments & GandCrab
This has been an interesting week in ransomware news. We had the GandCrab ransomware being released and distributed by exploit kits, TOR gateways stealing ransom payments from ransomware devs, and a bunch of towns getting hit with ransomware.
- February 02, 2018
- 05:31 PM
 0
0
-
The Week in Ransomware - January 26th 2018 - SamSam & Hack Attacks
While we are continuing to see less ransomware developed and more attackers focusing on a few large-impact strains, Ransomware is unfortunately not dead. This was particularly apparent this week with plenty of news to go around.
- January 26, 2018
- 04:50 PM
 5
5
-
The Week in Ransomware - January 12th 2018 - Ethereum & Small Variants
Another week when only small variants were released. Hopefully this downward trend is a slowdown in ransomware distribution. This biggest news was that the HC7 ransomware accepted Ethereum as a ransom payment. This is the first time this digital currency has been used with ransomware.
- January 12, 2018
- 12:45 PM
 1
1
-
The Week in Ransomware - December 22nd 2017 - WannaCry, Arrests, & More
The holidays are upon us and that means even ransomware developers are taking some time off. This showed this week with very few ransomware infections being released and for the most part we have only seen new variants of existing infections.
- December 22, 2017
- 05:23 PM
 0
0
-
The Week in Ransomware - December 15th 2017 - File Spider, California Voters Database, and More
This week was mostly about in-dev ransomware or new variants of older ransomware being released. The biggest news was the File Spider Ransomware campaign that was targeting countries in the Balkans. The other big news is the entire California voters database being leaked on the Internet and held for ransom.
- December 15, 2017
- 12:10 PM
 3
3
-
The Week in Ransomware - December 8th 2017 - StorageCrypt, HC7, and LockCrypt
This week was mostly about small ransomware variants being released, but we did have some big stories. First, we have HC7, which is targeting entire networks through hacked remote desktop services, then we had StorageCrypt being installed on NAS devices, and finally the county computers of Mecklenburg County were hit by LockCrypt.
- December 08, 2017
- 11:17 AM
 2
2
-
The Week in Ransomware - November 24th 2017 - qkG, Scarab, Necurs, and More
Not much to report this week other than Necurs starting to push the Scarab Ransomware and a new office document infecting ransomware called qkG. Otherwise, it has been a week of small variants that are in various stages of development.
- November 24, 2017
- 04:00 PM
 2
2
-
The Week in Ransomware - November 17th 2017 - CryptoMix and Targeted Attacks
This week was for the most part only small variants released. Of particular interest is the release of two CryptoMix variants and a in-development ransomware that is specifically targeting the J.Sterling Morton high school students through a fake student survey.
- November 17, 2017
- 08:00 PM
 1
1
-
The Week in Ransomware - November 10th 2017 - Ordinypt & LockCrypt
Mostly small silly variants released this week, but we did have a few interesting stories. The bigger stories include a new variant from Crysis released, a wiper disguised as a ransomware targeting companies in Germany, and hackers using RDP to install the LockCrypt ransomware.
- November 10, 2017
- 04:48 PM
 3
3
-
The Week in Ransomware - November 3rd 2017 - GIBON & ONI
Mostly small variants released this week, but we did have a new ransomware called GIBON that is interesting, and even better, decryptable. The other interesting news is about the ONI ransomware that appears to have be used as a smokescreen or wiper for an extended attack against Japanese companies.
- November 03, 2017
- 06:36 PM
 0
0
-
The Week in Ransomware - October 27th 2017 - Bad Rabbit & Tyrant
Lots of ransomware in the news this week. Of course the biggest story was the Bad Rabbit outbreak that targeted numerous countries, but mostly Russia and the Ukraine. We also had the Tyrant Ransomware, which was targeting Iranian companies.
- October 27, 2017
- 06:30 PM
 3
3